http://www.theguardian.com/world/2013/sep/05/nsa-gchq-encryption-codes-security

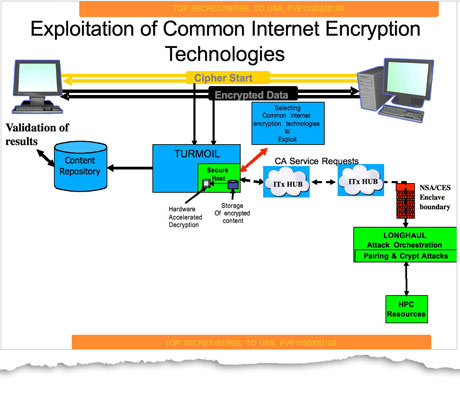 This network diagram, from a GCHQ pilot program, shows how the agency proposed a system to identify encrypted traffic from its internet cable-tapping programs and decrypt what it could in near-real time. Photograph: Guardian
This network diagram, from a GCHQ pilot program, shows how the agency proposed a system to identify encrypted traffic from its internet cable-tapping programs and decrypt what it could in near-real time. Photograph: Guardian Classified briefings between the NSA and GCHQ celebrate their success at 'defeating network security and privacy'. Photograph: Guardian
Classified briefings between the NSA and GCHQ celebrate their success at 'defeating network security and privacy'. Photograph: Guardian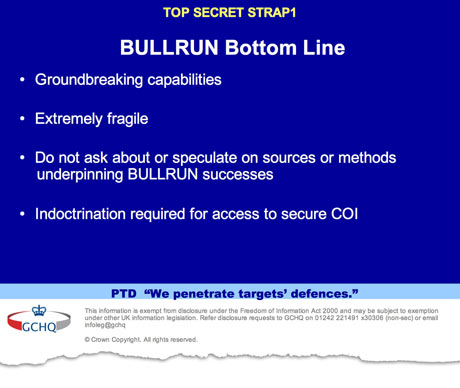 A slide showing that the secrecy of the agencies' capabilities against encryption is closely guarded. Photograph: Guardian
A slide showing that the secrecy of the agencies' capabilities against encryption is closely guarded. Photograph: Guardian
South American backlash.....

MORE ON THIS STORY
Sreeharsha, a McClatchy special correspondent, reported from Sao Paulo.
"I can give assurances to the public in Europe and around the world that we're not going around snooping at people's emails or listening to their phone calls," Obama told reporters at a press conference in Stockholm. "What we try to do is target very specific areas of concern."

Through covert partnerships with tech companies, the spy agencies have inserted secret vulnerabilities into encryption software. Photograph: Kacper Pempel/Reuters
US and British intelligence agencies have successfully cracked much of the online encryption relied upon by hundreds of millions of people to protect the privacy of their personal data, online transactions and emails, according to top-secret documents revealed by former contractor Edward Snowden.
The files show that the National Security Agency and its UK counterpart GCHQ have broadly compromised the guarantees thatinternet companies have given consumers to reassure them that their communications, online banking and medical records would be indecipherable to criminals or governments.
The agencies, the documents reveal, have adopted a battery of methods in their systematic and ongoing assault on what they see as one of the biggest threats to their ability to access huge swathes of internet traffic – "the use of ubiquitous encryption across the internet".
Those methods include covert measures to ensure NSA control over setting of international encryption standards, the use of supercomputers to break encryption with "brute force", and – the most closely guarded secret of all – collaboration with technology companies and internet service providers themselves.
Through these covert partnerships, the agencies have inserted secret vulnerabilities – known as backdoors or trapdoors – into commercial encryption software.
The files, from both the NSA and GCHQ, were obtained by the Guardian, and the details are being published today in partnership with the New York Times and ProPublica. They reveal:
• A 10-year NSA program against encryption technologies made a breakthrough in 2010 which made "vast amounts" of data collected through internet cable taps newly "exploitable".
• The NSA spends $250m a year on a program which, among other goals, works with technology companies to "covertly influence" their product designs.
• The secrecy of their capabilities against encryption is closely guarded, with analysts warned: "Do not ask about or speculate on sources or methods."
• The NSA describes strong decryption programs as the "price of admission for the US to maintain unrestricted access to and use of cyberspace".
• A GCHQ team has been working to develop ways into encrypted traffic on the "big four" service providers, named as Hotmail, Google, Yahoo and Facebook.
 This network diagram, from a GCHQ pilot program, shows how the agency proposed a system to identify encrypted traffic from its internet cable-tapping programs and decrypt what it could in near-real time. Photograph: Guardian
This network diagram, from a GCHQ pilot program, shows how the agency proposed a system to identify encrypted traffic from its internet cable-tapping programs and decrypt what it could in near-real time. Photograph: Guardian
The agencies insist that the ability to defeat encryption is vital to their core missions of counter-terrorism and foreign intelligence gathering.
But security experts accused them of attacking the internet itself and the privacy of all users. "Cryptography forms the basis for trust online," said Bruce Schneier, an encryption specialist and fellow at Harvard's Berkman Center for Internet and Society. "By deliberately undermining online security in a short-sighted effort to eavesdrop, the NSA is undermining the very fabric of the internet." Classified briefings between the agencies celebrate their success at "defeating network security and privacy".
"For the past decade, NSA has lead [sic] an aggressive, multi-pronged effort to break widely used internet encryption technologies," stated a 2010 GCHQ document. "Vast amounts of encrypted internet data which have up till now been discarded are now exploitable."
An internal agency memo noted that among British analysts shown a presentation on the NSA's progress: "Those not already briefed were gobsmacked!"
The breakthrough, which was not described in detail in the documents, meant the intelligence agencies were able to monitor "large amounts" of data flowing through the world's fibre-optic cables and break its encryption, despite assurances from internet company executives that this data was beyond the reach of government.
The key component of the NSA's battle against encryption, its collaboration with technology companies, is detailed in the US intelligence community's top-secret 2013 budget request under the heading "Sigint [signals intelligence] enabling".
 Classified briefings between the NSA and GCHQ celebrate their success at 'defeating network security and privacy'. Photograph: Guardian
Classified briefings between the NSA and GCHQ celebrate their success at 'defeating network security and privacy'. Photograph: Guardian
Funding for the program – $254.9m for this year – dwarfs that of thePrism program, which operates at a cost of $20m a year, according to previous NSA documents. Since 2011, the total spending on Sigint enabling has topped $800m. The program "actively engages US and foreign IT industries to covertly influence and/or overtly leverage their commercial products' designs", the document states. None of the companies involved in such partnerships are named; these details are guarded by still higher levels of classification.
Among other things, the program is designed to "insert vulnerabilities into commercial encryption systems". These would be known to theNSA, but to no one else, including ordinary customers, who are tellingly referred to in the document as "adversaries".
"These design changes make the systems in question exploitable through Sigint collection … with foreknowledge of the modification. To the consumer and other adversaries, however, the systems' security remains intact."
The document sets out in clear terms the program's broad aims, including making commercial encryption software "more tractable" toNSA attacks by "shaping" the worldwide marketplace and continuing efforts to break into the encryption used by the next generation of 4G phones.
Among the specific accomplishments for 2013, the NSA expects the program to obtain access to "data flowing through a hub for a major communications provider" and to a "major internet peer-to-peer voice and text communications system".
The document sets out in clear terms the program's broad aims, including making commercial encryption software "more tractable" toNSA attacks by "shaping" the worldwide marketplace and continuing efforts to break into the encryption used by the next generation of 4G phones.
Among the specific accomplishments for 2013, the NSA expects the program to obtain access to "data flowing through a hub for a major communications provider" and to a "major internet peer-to-peer voice and text communications system".
Technology companies maintain that they work with the intelligence agencies only when legally compelled to do so. The Guardian has previously reported that Microsoft co-operated with the NSA to circumvent encryption on the Outlook.com email and chat services. The company insisted that it was obliged to comply with "existing or future lawful demands" when designing its products.
The documents show that the agency has already achieved another of the goals laid out in the budget request: to influence the international standards upon which encryption systems rely.
Independent security experts have long suspected that the NSA has been introducing weaknesses into security standards, a fact confirmed for the first time by another secret document. It shows the agency worked covertly to get its own version of a draft security standard issued by the US National Institute of Standards and Technology approved for worldwide use in 2006.
The documents show that the agency has already achieved another of the goals laid out in the budget request: to influence the international standards upon which encryption systems rely.
Independent security experts have long suspected that the NSA has been introducing weaknesses into security standards, a fact confirmed for the first time by another secret document. It shows the agency worked covertly to get its own version of a draft security standard issued by the US National Institute of Standards and Technology approved for worldwide use in 2006.
"Eventually, NSA became the sole editor," the document states.
The NSA's codeword for its decryption program, Bullrun, is taken from a major battle of the American civil war. Its British counterpart, Edgehill, is named after the first major engagement of the English civil war, more than 200 years earlier.
A classification guide for NSA employees and contractors on Bullrun outlines in broad terms its goals.
"Project Bullrun deals with NSA's abilities to defeat the encryption used in specific network communication technologies. Bullrun involves multiple sources, all of which are extremely sensitive." The document reveals that the agency has capabilities against widely used online protocols, such as HTTPS, voice-over-IP and Secure Sockets Layer (SSL), used to protect online shopping and banking.
The document also shows that the NSA's Commercial Solutions Center, ostensibly the body through which technology companies can have their security products assessed and presented to prospective government buyers, has another, more clandestine role.
The document also shows that the NSA's Commercial Solutions Center, ostensibly the body through which technology companies can have their security products assessed and presented to prospective government buyers, has another, more clandestine role.
It is used by the NSA to "to leverage sensitive, co-operative relationships with specific industry partners" to insert vulnerabilities into security products. Operatives were warned that this information must be kept top secret "at a minimum".
A more general NSA classification guide reveals more detail on the agency's deep partnerships with industry, and its ability to modify products. It cautions analysts that two facts must remain top secret: that NSA makes modifications to commercial encryption software and devices "to make them exploitable", and that NSA "obtains cryptographic details of commercial cryptographic information security systems through industry relationships".
The agencies have not yet cracked all encryption technologies, however, the documents suggest. Snowden appeared to confirm this during a live Q&A with Guardian readers in June. "Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on," he said before warning that NSA can frequently find ways around it as a result of weak security on the computers at either end of the communication.
The agencies have not yet cracked all encryption technologies, however, the documents suggest. Snowden appeared to confirm this during a live Q&A with Guardian readers in June. "Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on," he said before warning that NSA can frequently find ways around it as a result of weak security on the computers at either end of the communication.
The documents are scattered with warnings over the importance of maintaining absolute secrecy around decryption capabilities.
 A slide showing that the secrecy of the agencies' capabilities against encryption is closely guarded. Photograph: Guardian
A slide showing that the secrecy of the agencies' capabilities against encryption is closely guarded. Photograph: Guardian
Strict guidelines were laid down at the GCHQ complex in Cheltenham, Gloucestershire, on how to discuss projects relating to decryption. Analysts were instructed: "Do not ask about or speculate on sources or methods underpinning Bullrun." This informaton was so closely guarded, according to one document, that even those with access to aspects of the program were warned: "There will be no 'need to know'."
The agencies were supposed to be "selective in which contractors are given exposure to this information", but it was ultimately seen by Snowden, one of 850,000 people in the US with top-secret clearance.A 2009 GCHQ document spells out the significant potential consequences of any leaks, including "damage to industry relationships".
"Loss of confidence in our ability to adhere to confidentiality agreements would lead to loss of access to proprietary information that can save time when developing new capability," intelligence workers were told. Somewhat less important to GCHQ was the public's trust which was marked as a moderate risk, the document stated.
"Loss of confidence in our ability to adhere to confidentiality agreements would lead to loss of access to proprietary information that can save time when developing new capability," intelligence workers were told. Somewhat less important to GCHQ was the public's trust which was marked as a moderate risk, the document stated.
"Some exploitable products are used by the general public; some exploitable weaknesses are well known eg possibility of recovering poorly chosen passwords," it said. "Knowledge that GCHQ exploits these products and the scale of our capability would raise public awareness generating unwelcome publicity for us and our political masters."
The decryption effort is particularly important to GCHQ. Its strategic advantage from its Tempora program – direct taps on transatlantic fibre-optic cables of major telecommunications corporations – was in danger of eroding as more and more big internet companies encrypted their traffic, responding to customer demands for guaranteed privacy.
Without attention, the 2010 GCHQ document warned, the UK's "Sigint utility will degrade as information flows changes, new applications are developed (and deployed) at pace and widespread encryption becomes more commonplace." Documents show that Edgehill's initial aim was to decode the encrypted traffic certified by three major (unnamed) internet companies and 30 types of Virtual Private Network (VPN) – used by businesses to provide secure remote access to their systems. By 2015, GCHQ hoped to have cracked the codes used by 15 major internet companies, and 300 VPNs.
Another program, codenamed Cheesy Name, was aimed at singling out encryption keys, known as 'certificates', that might be vulnerable to being cracked by GCHQ supercomputers.
Another program, codenamed Cheesy Name, was aimed at singling out encryption keys, known as 'certificates', that might be vulnerable to being cracked by GCHQ supercomputers.
Analysts on the Edgehill project were working on ways into the networks of major webmail providers as part of the decryption project. A quarterly update from 2012 notes the project's team "continue to work on understanding" the big four communication providers, named in the document as Hotmail, Google, Yahoo and Facebook, adding "work has predominantly been focused this quarter on Google due to new access opportunities being developed".
To help secure an insider advantage, GCHQ also established a Humint Operations Team (HOT). Humint, short for "human intelligence" refers to information gleaned directly from sources or undercover agents.
This GCHQ team was, according to an internal document, "responsible for identifying, recruiting and running covert agents in the global telecommunications industry."
"This enables GCHQ to tackle some of its most challenging targets," the report said. The efforts made by the NSA and GCHQ against encryption technologies may have negative consequences for all internet users, experts warn.
"Backdoors are fundamentally in conflict with good security," said Christopher Soghoian, principal technologist and senior policy analyst at the American Civil Liberties Union. "Backdoors expose all users of a backdoored system, not just intelligence agency targets, to heightened risk of data compromise." This is because the insertion of backdoors in a software product, particularly those that can be used to obtain unencrypted user communications or data, significantly increases the difficulty of designing a secure product."
This was a view echoed in a recent paper by Stephanie Pell, a former prosecutor at the US Department of Justice and non-resident fellow at the Center for Internet and Security at Stanford Law School.
"[An] encrypted communications system with a lawful interception back door is far more likely to result in the catastrophic loss of communications confidentiality than a system that never has access to the unencrypted communications of its users," she states.
Intelligence officials asked the Guardian, New York Times and ProPublica not to publish this article, saying that it might prompt foreign targets to switch to new forms of encryption or communications that would be harder to collect or read.
The three organisations removed some specific facts but decided to publish the story because of the value of a public debate about government actions that weaken the most powerful tools for protecting the privacy of internet users in the US and worldwide.
http://thehill.com/blogs/hillicon-valley/technology/320357-nra-claims-nsa-illegally-created-a-gun-database
The National Rifle Association joined the American Civil Liberties Union's lawsuit on Wednesday to end the government's massive phone record collection program.
In a brief filed in federal court, the NRA argues that the National Security Agency's database of phone records amounts to a "national gun registry."
After leaks by Edward Snowden, the NSA acknowledged that it collects records on virtually all U.S. phone calls. The data include phone numbers, call times and call durations, but not the contents of the conversations. The NSA says it only "queries" the database a limited number of times for specific national security reasons.
The NSA argues that Congress authorized the phone data surveillance with Section 215 of the Patriot Act, which allows for the collection of business records "relevant" to terrorism.
In its filing, the gun-rights group claims that the NSA's database would allow the government to identify and track gun owners based on whether they've called gun stores, shooting ranges or the NRA.
"Under the government’s reading of Section 215, the government could simply demand the periodic submission of all firearms dealers’ transaction records, then centralize them in a database indexed by the buyers’ names for later searching," the NRA writes.
The group claims that Congress could never have meant to authorize such a vast surveillance operation because it has repeatedly rejected proposals to create a national gun registry.
The NRA's brief also claims that the phone record program violates its members' First Amendment rights to associate and communicate freely. The group argues that people could fear retribution for associating with the gun-rights group if they knew the government was monitoring their phone records.
The Reporters Committee for Freedom of the Press, along with a host of news organizations including Bloomberg, Fox, National Public Radio and The New Yorker, also filed a brief on Wednesday in support of the ACLU lawsuit. The groups claim that the phone data collection inhibits the ability of journalists to contact sources and gather news.
South American backlash.....
MEXICO CITY — Mexican President Enrique Pena Nieto says reported surveillance by the U.S. National Security Agency would constitute an illegal act.
Agency would constitute an illegal act.
Pena Nieto demanded the United States investigate the allegations aired in a report Sunday night on Brazil’s Globo TV.
The report cites 2012 documents from NSA leaker Edward Snowden indicating the U.S. monitored Pena Nieto’s communications before he was elected in July 2012.
before he was elected in July 2012.
Pena Nieto spoke to reporters Monday at Canada’s Gander International Airport in Newfoundland on a stopover during his trip to Russia for a G-20 summit.
Pena Nieto said that “if proved … it is an act outside the law.” He said he may discuss the issue with President Barack Obama at the summit.
On Monday, Mexico’s foreign ministry said it summoned the U.S. ambassador to express Mexico’s concerns.
and.....
NSA leak might lead to cancellation of Brazil state visit

Brazilian President Dilma Rousseff | Marcello Casal Jr/Fama News/Abaca Press/MCT
- On the Web | More world coverage from McClatchy
By Tim Johnson and Vinod Sreeharsha | McClatchy Foreign Staff
MEXICO CITY — Revelations of a U.S. spy program that allegedly allows digital surveillance of the presidents of Brazil and Mexico have drawn cries of indignation and anger in both nations, but the fallout may be strongest for U.S.-Brazil relations.
At stake is whether Brazilian President Dilma Rousseff will cancel a planned state visit to Washington in October, the first offered by President Barack Obama this year, or will take action on digital security that may affect U.S. companies such as Google, Facebook and Yahoo.
Brazil’s O Globo television network reported Sunday night that the National Security Agency had spied on the emails, telephone calls and text messages of Rousseff and President Enrique Pena Nieto of Mexico. The report was based on documents obtained by journalist Glenn Greenwald, who lives in Rio de Janeiro, from Edward Snowden, a fugitive former NSA contractor who’s living in Moscow.
O Globo’s “Fantastico” program displayed an NSA document dated June 2012 that contained email sent by Pena Nieto, who was a presidential candidate at the time, discussing whom he might name to his Cabinet once elected. The network displayed a separate document that revealed communication patterns between Rousseff and her top advisers.
The revelations drew expressions of indignation in Brazil and Mexico.
Rousseff held an emergency Cabinet meeting Monday and her foreign minister, Luiz Alberto Figueiredo, summoned U.S. Ambassador Thomas Shannon for the second time since early July.
At a joint news conference Monday in Brasilia with Minister of Justice Jose Eduardo Cardozo, Figueiredo called the actions “an inadmissible and unacceptable violation of Brazilian sovereignty” and said Brazil expected a written explanation from the White House by the end of the week.
For its part, Mexico’s Foreign Secretariat said it “rejects and categorically condemns any act of espionage against Mexican citizens in violation of international law.” Mexico also summoned the U.S. ambassador, Anthony Wayne, but no meeting has yet taken place, as Wayne was out of the country.
Outrage seemed deeper and more widespread in Brazil than in Mexico.
One former Mexican ambassador, Andres Rozental, said he expected little fallout: “I don’t think this is a major event for Mexico and Mexico-U.S. relations.”
“Mexico has very little to gain out of going into a big hissy over this,” added Vanda Felbab-Brown, a security and intelligence expert at the Brookings Institution, a Washington research center.
The U.S. government shares electronic signals swept from the skies over Mexico to help the nation catch drug kingpins and disrupt criminal organizations.
“The reality is that even under Pena Nieto, the high-value targeting is still there through signals intelligence,” Felbab-Brown said.
The Brazilian newspaper O Estado de Sao Paulo reported Tuesday that Rousseff was considering canceling the state visit and might recall Brazil’s ambassador to the United States.
Brazil also said it would raise the issue at the Group of 20 meeting this week in Russia, where Rousseff will see Obama for the first time since the original NSA leaks surfaced in June.
Rubens Barbosa, a former Brazilian ambassador to Washington under Fernando Henrique Cardoso, an elder statesman and the de facto leader of Brazil’s opposition party, called the Rousseff administration’s reaction “adequate,” adding “you have to show that you are not comfortable with what the U.S. is doing.”
Brazil might respond in ways that have teeth.
Rousseff is reported to be considering a proposal that would suspend the operations of companies that cooperate with the NSA or U.S. intelligence agencies.
This might be a new bill or may be inserted into a proposal under debate in Congress called the Marco Civil, a framework for Internet governance in Brazil that’s being pushed by companies that include Google, Facebook, and Yahoo. If Rousseff were to propose modifying the Marco Civil to include her government’s concerns, these companies probably would stop supporting it.
The Washington Post cited NSA documents in reports in June and last month that said Facebook, Google and Yahoo routinely provide information to U.S. agencies.
Rousseff also has talked about requiring foreign websites or Internet companies to store data in Brazil rather than in the United States.
Brazil’s minister of communications, Paulo Bernardo, told O Estado de Sao Paulo that if companies cooperate with spying, their licenses to operate in Brazil will be canceled.
Peter Hakim, the president emeritus of the Inter-American Dialogue, a Washington-based policy group, noted that Secretary of State John Kerry had visited Brasilia last month to patch things up after the initial NSA leaks but “really did not do a very good job. He just brushed it off.”
Hakim said he believed the O Globo report, and he added that “snooping at presidents is disrespectful and offensive.”
Rousseff and Pena Nieto had to issue strong statements, Hakim said. “Both have to show they are not pushovers, that they can stand up to the U.S.,” he said.
Questions remain over whether Washington is pressuring Brasilia to make life difficult for Greenwald, a U.S. citizen who resides in Brazil.
No evidence of that has yet surfaced, but a Brazilian official said that according to a cable, a U.S. official had brought up Greenwald at a meeting with a Brazilian official in Washington in August, saying that, “Greenwald’s objective was to disrupt bilateral relations.”
The Brazilian official, who spoke only on the condition of anonymity because he wasn’t authorized to talk to journalists, added: “After Sunday, for certain Greenwald is being seen as an ally” by the Brazilian government.
The O Globo report has been widely covered in the rest of Latin America, and some experts say it’s served as a new wake-up call on needs for cyber-security.
“Governments still don’t have a grasp of the real dimensions of the problem,” said Rafael Bonifaz, an Ecuadorean cryptographer and activist for free encryption software.
Not only sitting leaders should be concerned about surveillance, Bonifaz said, but also anyone with an eye on future elections.
“It’s possible that future leaders are being spied on right now, and when they come to power the NSA will have a complete dossier on them,” Bonifaz said.
http://thehill.com/video/in-the-news/320185-obama-to-europe-us-not-snooping-on-phone-calls-emails
President Obama on Wednesday sought to reassure Europeans that the United States is not "snooping" into their phone calls and emails.
He defended the National Security Agency's surveillance programs, insisting they are focused only on counterterrorism, weapons of mass destruction, and cybersecurity.
The president conceded that the U.S. "has enormous capabilities when it comes to intelligence" but said the programs were under review to prevent "situations where we're gathering info just because we can."
"With changes in technology, with the growth in our capabilities, if our attitude is because we can do it, we should go ahead and do it, we may not be addressing some of the legitimate concerns and dangers that exist," Obama said.
The president also reiterated that he had confidence that domestically, the U.S. did "not surveil the American people or people within the United States." He said in instances when "procedures, because these are human endeavors, have not worked as they should … we've tightened them up."
But he also stressed that allies who had objected to the U.S. programs had benefited from their findings — or might use similar techniques.
"Some of the folks who have been the most offended publicly, we know use the same methods as us," Obama said.
The president was visiting Stockholm after canceling a previously planned summit in Moscow ahead of the G-20 summit. The scheduled bilateral talks with Russian President Vladimir Putin were canceled after the Kremlin announced it would grant temporary asylum to Edward Snowden, the former Defense contractor who leaked information about the NSA programs.



I did find your response to this mornings comment pretty quickly, much better format.
ReplyDeleteWow what a day, 10 year almost 3%, pm smackdown, lack of Syria votes and yes it seems like the Russians are the good guys now.
Yeah - some kind of day ..... can hardly wait to see what tomorrow brings !
ReplyDelete