https://krebsonsecurity.com/2014/09/home-depot-56m-cards-impacted-malware-contained/







 The disclosure, the first real information about the damage from a data breach that was initially disclosed on this site Sept. 2, also sought to assure customers that the malware used in the breach has been eliminated from its U.S. and Canadian store networks.
The disclosure, the first real information about the damage from a data breach that was initially disclosed on this site Sept. 2, also sought to assure customers that the malware used in the breach has been eliminated from its U.S. and Canadian store networks.














 On July 21, 2014, this site broke the newsthat multiple banks were reporting indications that Goodwill Industries had suffered an apparent breach that led to the theft of customer credit and debit card data. Goodwill later confirmed that the breach impacted a portion of its stores, but blamed the incident on an unnamed “third-party vendor.”
On July 21, 2014, this site broke the newsthat multiple banks were reporting indications that Goodwill Industries had suffered an apparent breach that led to the theft of customer credit and debit card data. Goodwill later confirmed that the breach impacted a portion of its stores, but blamed the incident on an unnamed “third-party vendor.”





















Home Depot: 56M Cards Impacted, Malware Contained
Home Depot said today that cyber criminals armed with custom-built malware stole an estimated 56 million debit and credit card numbers from its customers between April and September 2014. That disclosure officially makes the incident the largest retail card breach on record.
 The disclosure, the first real information about the damage from a data breach that was initially disclosed on this site Sept. 2, also sought to assure customers that the malware used in the breach has been eliminated from its U.S. and Canadian store networks.
The disclosure, the first real information about the damage from a data breach that was initially disclosed on this site Sept. 2, also sought to assure customers that the malware used in the breach has been eliminated from its U.S. and Canadian store networks.
“To protect customer data until the malware was eliminated, any terminals identified with malware were taken out of service, and the company quickly put in place other security enhancements,” the company said via press release (PDF). “The hackers’ method of entry has been closed off, the malware has been eliminated from the company’s systems, and the company has rolled out enhanced encryption of payment data to all U.S. stores.”
That “enhanced payment protection,” the company said, involves new payment security protection “that locks down payment data through enhanced encryption, which takes raw payment card information and scrambles it to make it unreadable and virtually useless to hackers.”
“Home Depot’s new encryption technology, provided by Voltage Security, Inc., has been tested and validated by two independent IT security firms,” the statement continues. “The encryption project was launched in January 2014. The rollout was completed in all U.S. stores on Saturday, September 13, 2014. The rollout to Canadian stores will be completed by early 2015.”
****
http://krebsonsecurity.com/2014/09/in-home-depot-breach-investigation-focuses-on-self-checkout-lanes/
In Home Depot Breach, Investigation Focuses on Self-Checkout Lanes
The malicious software that unknown thieves used to steal credit and debit card numbers in the data breach at Home Depot this year was installed mainly on payment systems in the self-checkout lanes at retail stores, according to sources close to the investigation. The finding could mean thieves stole far fewer cards during the almost five-month breach than they might have otherwise.
Since news of the Home Depot breach first broke on Sept. 2, this publication has been in constant contact with multiple financial institutions that are closely monitoring daily alerts from Visa and MasterCardfor reports about new batches of accounts that the card associations believe were compromised in the break-in. Many banks have been bracing for a financial hit that is much bigger than the exposure caused by the breach at Target, which lasted only three weeks and exposed 40 million cards.
But so far, banking sources say Visa and MasterCard have been reporting far fewer compromised cards than expected given the length of the Home Depot exposure.
Sources now tell KrebsOnSecurity that in a conference call with financial institutions today, officials at MasterCard shared several updates from the ongoing forensic investigation into the breach at the nationwide home improvement store chain. The card brand reportedly told banks that at this time it is believed that only self-checkout terminals were impacted in the breach, but stressed that the investigation is far from complete.
****
http://krebsonsecurity.com/2014/09/breach-at-goodwill-vendor-lasted-18-months/
Breach at Goodwill Vendor Lasted 18 Months
C&K Systems Inc., a third-party payment vendor blamed for a credit and debit card breach at more than 330 Goodwill locations nationwide, disclosed this week that the intrusion lasted more than 18 months and has impacted at least two other organizations.
 On July 21, 2014, this site broke the newsthat multiple banks were reporting indications that Goodwill Industries had suffered an apparent breach that led to the theft of customer credit and debit card data. Goodwill later confirmed that the breach impacted a portion of its stores, but blamed the incident on an unnamed “third-party vendor.”
On July 21, 2014, this site broke the newsthat multiple banks were reporting indications that Goodwill Industries had suffered an apparent breach that led to the theft of customer credit and debit card data. Goodwill later confirmed that the breach impacted a portion of its stores, but blamed the incident on an unnamed “third-party vendor.”
Last week, KrebsOnSecurity obtained some internal talking points apparently sent by Goodwill to prepare its member organizations to respond to any calls from the news media about the incident. Those talking points identified the breached third-party vendor as C&K Systems, a retail point-of-sale operator based in Murrells Inlet, S.C.
In response to inquiries from this reporter, C&K released a statement acknowledging that it was informed on July 30 by “an independent security analyst” that its “hosted managed services environment may have experienced unauthorized access.” The company says it then hired an independent cyber investigative team and alerted law enforcement about the incident.
C&K says the investigation determined malicious hackers had access to its systems “intermittently” between Feb. 10, 2013 and Aug. 14, 2014, and that the intrusion led to the the installation of “highly specialized point of sale (POS) infostealer.rawpos malware variant that was undetectable by our security software systems until Sept. 5, 2014,” [link added].
*****
http://krebsonsecurity.com/2014/09/in-wake-of-confirmed-breach-at-home-depot-banks-see-spike-in-pin-debit-card-fraud/
In Wake of Confirmed Breach at Home Depot, Banks See Spike in PIN Debit Card Fraud
Nearly a week after this blog first reported signs that Home Depot was battling a major security incident, the company has acknowledged that it suffered a credit and debit card breach involving its U.S. and Canadian stores dating back to April 2014. Home Depot was quick to assure customers and banks that no debit card PIN data was compromised in the break-in. Nevertheless, multiple financial institutions contacted by this publication are reporting a steep increase over the past few days in fraudulent ATM withdrawals on customer accounts.
The card data for sale in the undergroundthat was stolen from Home Depot shoppers allows thieves to create counterfeit copies of debit and credit cards that can be used to purchase merchandise in big box stores. But if the crooks who buy stolen debit cards also are able to change the PIN on those accounts, the fabricated debit cards can then be used to withdraw cash from ATMs.
Experts say the thieves who are perpetrating the debit card fraud are capitalizing on a glut of card information stolen from Home Depot customers and being sold in cybercrime shops online. Those same crooks also are taking advantage of weak authentication methods in the automated phone systems that many banks use to allow customers to reset the PINs on their cards.
Here’s the critical part: The card data stolen from Home Depot customers and now for sale on the crime shop Rescator[dot]cc includes both the information needed to fabricate counterfeit cards as well as the legitimate cardholder’s full name and the city, state and ZIP of the Home Depot store from which the card was stolen (presumably by malware installed on some part of the retailer’s network, and probably on each point-of-sale device).
****
http://krebsonsecurity.com/2014/09/home-depot-hit-by-same-malware-as-target/
Home Depot Hit By Same Malware as Target
The apparent credit and debit card breach uncovered last week at Home Depot was aided in part by a new variant of the malicious software program that stole card account data from cash registers at Target last December, according to sources close to the investigation.
On Tuesday, KrebsOnSecurity broke the news that Home Depot was working with law enforcement to investigate “unusual activity” after multiple banks said they’d traced a pattern of card fraud back to debit and credit cards that had all been used at Home Depot locations since May of this year.
A source close to the investigation told this author that an analysis revealed at least some of Home Depot’s store registers had been infected with a new variant of “BlackPOS” (a.k.a. “Kaptoxa”), a malware strain designed to siphon data from cards when they are swiped at infected point-of-sale systems running Microsoft Windows.
The information on the malware adds another indicator that those responsible for the as-yet unconfirmed breach at Home Depot also were involved in the December 2013 attack on Target that exposed 40 million customer debit and credit card accounts. BlackPOS also was found on point-of-sale systems at Target last year. What’s more, cards apparently stolen from Home Depot shoppers first turned up for sale on Rescator[dot]cc, the same underground cybercrime shop that sold millions of cards stolen in the Target attack.
****
http://krebsonsecurity.com/2014/09/medical-records-for-sale-in-underground-stolen-from-texas-life-insurance-firm/
Medical Records For Sale in Underground Stolen From Texas Life Insurance Firm
How much are your medical records worth in the cybercrime underground? This week, KrebsOnSecurity discovered medical records being sold in bulk for as little as $6.40 apiece. The digital documents, several of which were obtained by sources working with this publication, were apparently stolen from a Texas-based life insurance company that now says it is working with federal authorities on an investigation into a possible data breach.
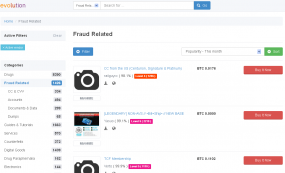
Purloined medical records are among the many illicit goods for sale on theEvolution Market, a black market bazaar that traffics mostly in narcotics and fraud-related goods — including plenty of stolen financial data. Evolution cannot be reached from the regular Internet. Rather, visitors can only browse the site using Tor, software that helps users disguise their identity by bouncing their traffic between different servers, and by encrypting that traffic at every hop along the way.
Last week, a reader alerted this author to a merchant on Evolution Market nicknamed “ImperialRussia” who was advertising medical records for sale. ImperialRussia was hawking his goods as “fullz” — street slang for a package of all the personal and financial records that thieves would need to fraudulently open up new lines of credit in a person’s name.
Each document for sale by this seller includes the would-be identity theft victim’s name, their medical history, address, phone and driver license number, Social Security number, date of birth, bank name, routing number and checking/savings account number. Customers can purchase the records using the digital currency Bitcoin.
A set of five fullz retails for $40 ($8 per record). Buy 20 fullz and the price drops to $7 per record. Purchase 50 or more fullz, and the per record cost falls to just $6.40 — roughly the price of a value meal at a fast food restaurant. Incidentally, even at $8 per record, that’s cheaper than the price most stolen credit cards fetch on the underground markets.


No comments:
Post a Comment