http://hotair.com/archives/2013/06/06/mark-kirk-to-holder-tell-the-truth-has-the-doj-been-harvesting-congresss-phone-records-too/
( Did DOJ spy on Congress - did Holder hint yeah , but I'll only admit that in a secret session ? )
http://ex-skf.blogspot.com/2013/06/us-nsas-top-secret-prism-program-has.html
* * *
and....
http://www.zerohedge.com/news/2013-06-06/meet-prism-us-984xn-us-governments-internet-espionage-super-operation
and....
http://www.blacklistednews.com/Two_Secretive_Israeli_Companies_May_Have_Bugged_The_US_Telecommunications_Grid_For_The_NSA/26492/0/0/0/Y/M.html
http://www.businessinsider.com/prism-spying-program-nsa-fbi-mine-data-yahoo-facebook-google-2013-6
http://www.businessinsider.com/the-impact-of-nsa-domestic-spying-2013-6
http://www.businessinsider.com/affect-of-nsa-surveillance-on-obama-2013-6
( Everyone's a terrorist ? )

The Obama administration will be bracing itself for a torrent of hostile questions this morning following the apparent revelation that the National Security Agency has been data-mining the phone records of tens of millions of ordinary Americans.


The order itself, signed by Judge Roger Vinson of the Foreign Intelligence Surveillance Court, prohibits Verizon from alerting its customers of the FBI’s request for their records.
The Obama administration confirmed that it is collecting massive numbers of telephone records from at least one carrier, but said that it is only recording data such as telephone numbers or call lengths, not subscribers' identities or the content of their calls.
Verizon has declined a request for comment by RT.
( Did DOJ spy on Congress - did Holder hint yeah , but I'll only admit that in a secret session ? )
Mark Kirk to Holder: Tell the truth, has the DOJ been harvesting Congress’s phone records too?
POSTED AT 2:41 PM ON JUNE 6, 2013 BY ALLAHPUNDIT
Via Joel Gehrke, I won’t spoil the surprise of Holder’s answer. I’ll simply amend something that I said last night on Twitter: After this exchange, we may be only two or three more scandals away from this guy’s job being in trouble.
At another point in today’s hearing, he said he won’t resign because there are still lots of“goals” he has as AG — which, given the news of the last few weeks, may be the single most terrifying soundbite to come out of Scandalmania. To cleanse your palate after you watch, read this short but pungent Onion piece that fills the gap between what Hopenchange promised circa 2008 and what it’s amounted to in practice. If you cringed at O’s insulting speech about how stricken his liberal conscience is by having to vaporize unidentified Pakistanis from the air, you’ll appreciate it.
* * *
Unlike Verizon, these Internet companies (so far) deny they had any knowledge of the government snooping.
(Sure.)
NSA has been receiving assistance from "communications providers in the US", according to The Guardian. AT&T, Verizon, Comcast,
From The Guardian (6/6/2013; emphasis is mine):
(Sure.)
NSA has been receiving assistance from "communications providers in the US", according to The Guardian. AT&T, Verizon, Comcast,
From The Guardian (6/6/2013; emphasis is mine):
NSA taps in to internet giants' systems to mine user data, secret files reveal
• Top secret PRISM program claims direct access to servers of firms including Google, Facebook and Apple
• Companies deny any knowledge of program in operation since 2007
The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian.
The NSA access is part of a previously undisclosed program called PRISM, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says.
The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation – classified as top secret with no distribution to foreign allies – which was apparently used to train intelligence operatives on the capabilities of the program. The document claims "collection directly from the servers" of major US service providers.
Although the presentation claims the program is run with the assistance of the companies, all those who responded to a Guardian request for comment on Thursday denied knowledge of any such program.
In a statement, Google said: "Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'back door' into our systems, but Google does not have a back door for the government to access private user data."
Several senior tech executives insisted that they had no knowledge of PRISM or of any similar scheme. They said they would never have been involved in such a program. "If they are doing this, they are doing it without our knowledge," one said.
An Apple spokesman said it had "never heard" of PRISM.
The NSA access was enabled by changes to US surveillance law introduced under President Bush and renewed under Obama in December 2012.
The program facilitates extensive, in-depth surveillance on live communications and stored information. The law allows for the targeting of any customers of participating firms who live outside the US, or those Americans whose communications include people outside the US.
It also opens the possibility of communications made entirely within the US being collected without warrants.
Disclosure of the PRISM program follows a leak to the Guardian on Wednesday of a top-secret court order compelling telecoms provider Verizon to turn over the telephone records of millions of US customers.
The participation of the internet companies in PRISM will add to the debate, ignited by the Verizon revelation, about the scale of surveillance by the intelligence services. Unlike the collection of those call records, this surveillance can include the content of communications and not just the metadata.
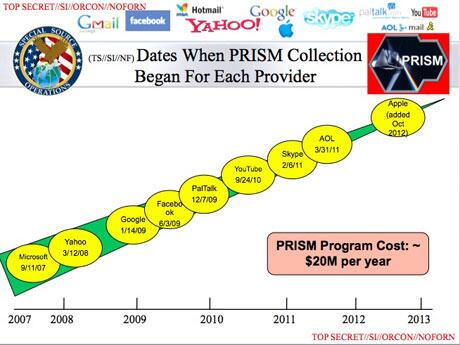
Some of the world's largest internet brands are claimed to be part of the information-sharing program since its introduction in 2007. Microsoft – which is currently running an advertising campaign with the slogan "Your privacy is our priority" – was the first, with collection beginning in December 2007.
It was followed by Yahoo in 2008; Google, Facebook and PalTalk in 2009; YouTube in 2010; Skype and AOL in 2011; and finally Apple, which joined the program in 2012. The program is continuing to expand, with other providers due to come online.The extent and nature of the data collected from each company varies.
Companies are legally obliged to comply with requests for users' communications under US law, but the PRISM program allows the intelligence services direct access to the companies' servers. The NSA document notes the operations have "assistance of communications providers in the US".
(Full article at the link)
US's Washington Post has the article on the same subject. A joint operation by the two papers?It was in 2006 when an AT&T whistleblower, Mark Klein, leaked internal AT&T documents that revealed the company had set up a secret room in its San Francisco office to give the National Security Agency access to its fiber optic internet cables.
No one cared then, and the Foreign Intelligence Surveillance Act was amended in July 2008 to authorize the NSA program of warrantless wiretapping. Will anyone care now?
(So far Twitter seems to be safe. I wonder how long.)
and....
http://www.zerohedge.com/news/2013-06-06/meet-prism-us-984xn-us-governments-internet-espionage-super-operation
Meet PRISM / US-984XN - The US Government's Internet Espionage Super Operation
Submitted by Tyler Durden on 06/06/2013 19:31 -0400

- Apple
- FBI
- national intelligence
- national security
- President Obama
- PrISM
- SPY
- Totalitarianism
- Verizon
The disclosures involving this (and the prior) administration's Big Brother surveillance state, which would make Nixon blush with envy are now coming fast and furious (one wonders - why now: even that bastion of liberalism the NY Times, has turned against Obama). Although while the Guardian's overnight news that Verizon (and most certainly AT&T as well among others) was cooperating with the NSA on spying on US citizens, so far at least the internet seemed, if only to the great unwashed masses, immune. That is no longer the case following news from the WaPo exposing PRISM, a highly classified program, which has not been disclosed publicly before. "Its establishment in 2007 and six years of exponential growth took place beneath the surface of a roiling debate over the boundaries of surveillance and privacy." What PRISM does is to allow the NSA and the FBI to tap directly "into the central servers of nine leading U.S. Internet companies, extracting audio, video, photographs, e-mails, documents and connection logs that enable analysts to track a person’s movements and contacts over time."
The secrecy is so deep we expect even the president himself may not know about it (but he does):
The highly classified program, code-named PRISM, has not been disclosed publicly before. Its establishment in 2007 and six years of exponential growth took place beneath the surface of a roiling debate over the boundaries of surveillance and privacy. Even late last year, when critics of the foreign intelligence statute argued for changes, the only members of Congress who know about PRISM were bound by oaths of office to hold their tongues.
Of course, PRISM is from the government,and it is here to help you. But the question is why are some of the biggest private companies explicitly collaborating with what is now the biggest exposed spying operation in history, companies which include such household names as Microsoft Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple. Yes, everyone's beloved Apple was added in October 2012: the NSA knows all about your music playlist, not to mention has a database of all your iMessages.
In other words, all those newly minted people known as corporations are in on it, but not:dear debt serf. It's a small club, and there is a multimillion liquid net-worth cutoff... and you are not in it. From WaPo:
An internal presentation on the Silicon Valley operation, intended for senior analysts in the NSA’s Signals Intelligence Directorate, described the new tool as the most prolific contributor to the President’s Daily Brief, which cited PRISM data in 1,477 articles last year. According to the briefing slides, obtained by The Washington Post, “NSA reporting increasingly relies on PRISM” as its leading source of raw material, accounting for nearly 1 in 7 intelligence reports.That is a remarkable figure in an agency that measures annual intake in the trillions of communications. It is all the more striking because the NSA, whose lawful mission is foreign intelligence, is reaching deep inside the machinery of American companies that host hundreds of millions of American-held accounts on American soil.The technology companies, which participate knowingly in PRISM operations, include most of the dominant global players of Silicon Valley. They are listed on a roster that bears their logos in order of entry into the program: “Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.” PalTalk, although much smaller, has hosted significant traffic during the Arab Spring and in the ongoing Syrian civil war....the PRISM program appears more nearly to resemble the most controversial of the warrantless surveillance orders issued by President George W. Bush after the al-Qaeda attacks of Sept. 11, 2001. Its history, in which President Obama presided over “exponential growth” in a program that candidate Obama criticized, shows how fundamentally surveillance law and practice have shifted away from individual suspicion in favor of systematic, mass collection techniques.
Spying on US citizens is "incidental"... kinda like killing thousands of women and children in drone raids is "collateral damage":
Even when the system works just as advertised, with no American singled out for targeting, the NSA routinely collects a great deal of American content. That is described as “incidental,” and it is inherent in contact chaining, one of the basic tools of the trade. To collect on a suspected spy or foreign terrorist means, at minimum, that everyone in the suspect’s inbox or outbox is swept in. Intelligence analysts are typically taught to chain through contacts two “hops” out from their target, which increases “incidental collection” exponentially. The same math explains the aphorism, from the John Guare play, that no one is more than “six degrees of separation” from any other person.
This is how the big corporations sleep at night:
Formally, in exchange for immunity from lawsuits, companies like Yahoo and AOL are obliged to accept a “directive” from the attorney general and the director of national intelligence to open their servers to the FBI’s Data Intercept Technology Unit, which handles liaison to U.S. companies from the NSA. In 2008, Congress gave the Justice Department authority to for a secret order from the Foreign Surveillance Intelligence Court to compel a reluctant company “to comply.”In practice, there is room for a company to maneuver, delay or resist. When a clandestine intelligence program meets a highly regulated industry, said a lawyer with experience in bridging the gaps, neither side wants to risk a public fight. The engineering problems are so immense, in systems of such complexity and frequent change, that the FBI and NSA would be hard pressed to build in back doors without active help from each company.
Some "do lots of evil" by their customers. They just don't disclose it:
“Google cares deeply about the security of our users’ data,” a company spokesman said. “We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a ‘back door’ for the government to access private user data.”
Time to kill that Facebook profile... or be accidentally killed for being "of a terroristy persuasion" based on some NSA algo:
There has been “continued exponential growth in tasking to Facebook and Skype,” according to the 41 PRISM slides. With a few clicks and an affirmation that the subject is believed to be engaged in terrorism, espionage or nuclear proliferation, an analyst obtains full access to Facebook’s “extensive search and surveillance capabilities against the variety of online social networking services.”
And some more charts:
Introducing the program
A slide briefing analysts at the National Security Agency about the program touts its effectiveness and features the logos of the companies involved.

Monitoring a target's communication
This diagram shows how the bulk of the world’s electronic communications move through companies based in the United States.
Providers and data
The PRISM program collects a wide range of data from the nine companies, although the details vary by provider.
In retrospect, it is sad what a farce this country has become: artificial market, centrally-planned economy, pervasive spying on the people, a tax collector that target political enemies, an administration that openly lies under oath...
If we didn't know better we would say this was 1955 Stalingrad, although Stalingrad at the height of totalitarianism was for amateurs. This is next lever shit: "Firsthand experience with these systems, and horror at their capabilities, is what drove a career intelligence officer to provide PowerPoint slides about PRISM and supporting materials to The Washington Post in order to expose what he believes to be a gross intrusion on privacy. “They quite literally can watch your ideas form as you type,” the officer said."
and....
http://www.blacklistednews.com/Two_Secretive_Israeli_Companies_May_Have_Bugged_The_US_Telecommunications_Grid_For_The_NSA/26492/0/0/0/Y/M.html
Two Secretive Israeli Companies May Have Bugged The US Telecommunications Grid For The NSA
June 6, 2013
Source: Business Insider
http://www.businessinsider.com/prism-spying-program-nsa-fbi-mine-data-yahoo-facebook-google-2013-6
IT GETS WORSE: Google, Facebook, Apple Share Shocking Amount Of User Data With The Government

White House on www.flickr.com
|
The National Security Agency and FBI have been engaging in a highly classified program that mines data from leading U.S. internet companies, according to a bombshell report in The Washington Post Thursday night.
The program is code-named PRISM, and the Post reports that it was established in 2007. According to the report, the nine companies that "participate knowingly" in the program are Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.
The NSA and FBI tap directly into the central servers of the companies. It allows the agencies to obtain audio, video, photographs, emails, documents and connection logs that "enable analysts to track a person’s movements and contacts over time."
The program has not been disclosed publicly, and is only being disclosed now after whistleblower revealed the program to the Post because of "horror" at its capabilities.
"They quite literally can watch your ideas form as you type," said the whistleblower, described as a career intelligence officer, in a truly harrowing quote.
The Washington Post's report comes less than 24 hours after revelations of the NSA's collection of data from millions of Americans' phone records. The Obama administration and members of both parties of Congress defended that practice, which they acknowledged has been going on for seven years.
From Guardian editor Julian Borger, here's a key chart that breaks down when each of the nine companies joined the program:
http://www.businessinsider.com/the-impact-of-nsa-domestic-spying-2013-6
The Guardian's Bombshell Revelation About NSA Domestic Spying Is Only The Tip Of The Iceberg

William Binney
|
Although the revelation doesn't surprise privacy advocates, the fact that Greenwald obtained a top secret court order compelling Verizon to give the NSA information on all telephone calls in its systems is the first concrete piece of evidence exposing dragnet domestic surveillance.
But, unfortunately for U.S. citizens who don't want their government routinely spying on them, that's just the beginning.
From The Guardian:
It is not known whether Verizon is the only cell-phone provider to be targeted with such an order, although previous reporting has suggested the NSA has collected cell records from all major mobile networks.
Thanks to AT&T whistleblower Mark Klein and NSA whistleblowers William Binney and Thomas Drake, we know that the NSA has been perpetually amassing not only phone records but virtually all electronic records and communications.
As an AT&T engineer, Klein discovered that a special NSA network actively "vacuumed up Internet and phone-call data from ordinary Americans with the cooperation of AT&T," emphasizing that "much of the data sent through AT&T to the NSA was purely domestic."
Jame Bamford of Wired subsequently reported that the NSA had hired secretive contractors with extensive ties to Israeli intelligence to establish 10 to 20 wiretapping rooms at key telecommunication points throughout the country.
Binney — one of the best mathematicians and code breakers in NSA history — worked for the Defense Department's foreign signals intelligence agency for 32 years before resigning in late 2001 because he "could not stay after the NSA began purposefully violating the Constitution."
He's detailed how, ever since 9/11, the NSA has run a top-secret surveillance program that amasses electronic data — phone calls, GPS information, emails, social media, banking and travel records, entire government databases — and analyzes the information "to be able to monitor what people are doing" and who they are doing it with.
Binney would know — he built the original software (i.e. ThinThread) that identified, in real time, networks of connections between individuals based on their electronic communications.
"I can pull your entire life together from all those domains and map it out and show your entire life over time," Binney told documentarian Laura Poitras while she was investigating the NSA's $2 billion data storage facility in Bluffdale, Utah. "This is something the KGB, the Stasi or the Gestapo would have loved to have had."
Drake, a former NSA senior executive charged under the espionage act after blowing the whistle, has repeatedly discussed how he also believes that the NSA was using Israeli-made NARUS hardware to "seize and save all personal electronic communications."
So although Greenwald notes that the "unlimited nature of the records being handed over to the NSA is extremely unusual," his report simply confirms what's been happening for more than a decade.
And according to a classified ruling by the Foreign Intelligence Surveillance Court (FISC) — which oversees requests for surveillance warrants — the NSA was found to have violated the Fourth Amendment of the Constitution "on at least one occasion."
WH on NSA snooping: You can totally trust us
POSTED AT 8:01 AM ON JUNE 6, 2013 BY ED MORRISSEY
The White House admitted this morning that the Guardian story last night was accurate — the NSA has been collecting metadata on Verizon’s phone calls for the last couple of months. Thanks to a secret court order, the phone records and location of calls by over 121 million customers now rest within the vaults of the NSA. And according to the Associated Press’ White House source, that’s no problem, because we can totally trust them to only do nice things with them, and not be evil and rotten like the previous administration who did pretty much the same thing:
The White House on Thursday defended the National Security Agency’s need to collect telephone records of U.S. citizens, calling such information “a critical tool in protecting the nation from terrorist threats.”While defending the practice, a senior Obama administration official did not confirm a newspaper report that the NSA has been collecting the telephone records of millions of U.S. customers of Verizon under a top secret court order. …Under the terms of the order, the phone numbers of both parties on a call are handed over, as are location data, call duration, unique identifiers, and the time and duration of all calls. The contents of the conversation itself are not covered, The Guardian said.The administration official said, “On its face, the order reprinted in the article does not allow the government to listen in on anyone’s telephone calls.”
The AP explains the difference:
The broad, unlimited nature of the records being handed over to the NSA is unusual. FISA court orders typically direct the production of records pertaining to a specific named target suspected of being an agent of a terrorist group or foreign state, or a finite set of individually named targets. NSA warrantless wiretapping during the George W. Bush administration after the 9/11 attacks was very controversial.
They’re conflating a couple of things. First, the Bush administration did conduct massive data-mining of phone providers in the same way being done here, but the warrantless wiretapping was much more narrow. That surveillance was conducted on specific phone numbers discovered by intelligence operations that were in use by suspected terrorists, and on calls in which at least one end was in a foreign country. It was still controversial as the other end of the call was often inside the US and arguably comprised the forbidden practice of intel services spying domestically (the FBI has jurisdiction but has to proceed in criminal court with warrants), and eventually the Bush administration was forced to seek FISA warrants for it. But those were and are two different kinds of operations.
Hypocrisy is an unfortunately ubiquitous condition in politics, but in the case of NSA seizing Verizon’s phone records, it’s particularly widespread. Some of the people expressing outrage for the Obama administration’s efforts at data mining had a different attitude toward it when Bush was in office. Conversely, we’ll see some people defending Obama who considered Bush evil incarnate for the same thing.
Either way, we’re left with the situation of having the federal government seizing private records without any meaningful civil due process that engages the citizens affected, whether that includes actual wiretaps or just cataloguing our calls and movements. Perhaps this will move this issue out of the partisan sphere and into a common ground in which we can all work to define exactly how far we’re willing to go in trading privacy for security. In order to get there, we’d all better recognize the hypocrisy that has abounded on this issue for far too long, and start thinking about higher principles than party affiliation when it comes to national security and constitutional protections.
http://www.businessinsider.com/affect-of-nsa-surveillance-on-obama-2013-6
( Everyone's a terrorist ? )
Domestic Spying Revelation Could Be Devastating For The Obama White House

AP Photo/M. Spencer Green
Democratic presidential hopeful Sen. Barack Obama D-Ill., pauses as he talks about the assasination of Pakistan opposition leader Benazir Bhutto as he begins a campaign rally Thursday, Dec. 27, 2007 in Des Moines, Iowa.
Not to be confused with eaves-dropping, or bugging the phones of those suspected of conspiring to commit a terrorist or criminal offence, the top secret court order published by The Guardian appears to show that the NSA has been trawling the anonymous 'metadata' of potentially billions of phone-calls.
On the one hand, American might take comfort that the 'internals' of their phone conversations – ie the voices themselves - are not being routinely recorded, but on the other, it seems from this leak that potentially everyone with a phone is under some form of surveillance in the USA.
Studies have shown that while anonymous, the 'metadata' – records of location data, call duration, unique identifiers – can provide a surprising amount of information, surprisingly quickly when zeroed in on by investigators.
For Mr Obama– a president who prided himself on his liberal credentials – this leak is a potentially devastating revelation since it exposes him to attack on two fronts - from both the libertarian Right and the liberal Left.
Already the administration has been hammered over its aggressive prosecution of leakers, including what appeared to be an attempt to criminalise a Fox News journalist, James Rosen, for working a source to obtain a leak from the State Department about North Korea.
That story caused the New York Times – usually a reliable friend of the Obama administration - to write a seething editorial accusing the Department of Justice of over-reaching, and using its powers to send a "chilling" message to the media.
It is not clear how wide the NSA data-mining project goes, it's effectiveness as a counter-terrorism tool in identifying potential terrorist or criminal cells or – indeed – whether it has been used for any other purposes.
It appears from previous reports that the NSA's data-mining operation is not new, and has long been suspected – but this is the first clear-cut proof, in the shape of a highly unusual leak from the secretive Foreign Intelligence Service Court (Fisa), that the practice is occurring.
A report in USA Today newspaper from 2006, quoting anonymous intelligence officials, alleged that the NSA been "secretly collecting the phone call records of tens of millions of Americans" and that the agency was using the data to "analyze calling patterns in an effort to detect terrorist activity".
Since September 11 and the passing of the 2001 Patriot Act, the American public has accepted a great deal of inconvenience and intrusion in the name of national security. The publication of this court order will re-open the debate on how far the security services' writ should run.
Politically, the difficulty for Mr Obama is that even if the NSA is actually doing nothing different than it did for George W Bush, the American public – particularly on the liberal left – had believed that Mr Obama's administration represented a fundamental departure from the excesses of the Bush years.
Now, with the continued debate over the use of drones, the failure to close Guantanamo, the ultra-aggressive prosecution of leaks even to the point, perhaps, of muzzling a free press – the questions from the public and the media are starting to weigh down on the Obama White House.
Already last night, within hours of publication, civil liberties groups who have long warned about the extent of secret surveillance, were jumping on the revelations.
"This confirms what we had long suspected," says Cindy Cohn, an attorney at the Electronic Frontier Foundation (EFF), a civil liberties organization that has accused the government of operating a secret dragnet surveillance program told the Washington Post.
"I don't think Congress thought it was authorizing dragnet surveillance" when it passed the Patriot Act, Ms Cohn said, "I don't think Americans think that's OK. I would be shocked if the majority of Congressmen thought it's okay." Over the next few days and weeks, expect a fierce and polarizing debate over just what Americans do feel is acceptable, in the name of their national security.
http://rt.com/usa/nasa-collecting-millions-verizon-records-291/
Top-secret court order reveals NSA's daily data collection on millions of Americans
Published time: June 06, 2013 02:09
Edited time: June 06, 2013 12:23
Edited time: June 06, 2013 12:23

Reuters / Rick Wilking
The US National Security Agency is currently collecting the telephone records of millions of unwitting individuals via a secret court order issued in April obtained by The Guardian newspaper, which has posted it online.
Unlike warrants that have been issued to collect the information of suspects targetted by intelligence agencies, the newly disclosed top secret order requires Verizon, one of the largest telecom agencies in the US, to provide both the FBI and the NSA information on all telephone calls made through its systems, both domestically and to foreign countries.
According to a copy of the order, Verizon is required to disclose the numbers of both parties during a call, as well as location, call duration, and other unique data on an "ongoing, daily basis.” Meaning that, regardless of whether an individual is suspected of or linked to any crime, the data of all Verizon customers is currently being delivered in bulk to the intelligence agency.
As to the authority claimed by the government via this order, that is specifically cited to fall under the “business records” provision of the PATRIOT Act of 2001, which was granted a four-year extension by President Obama in May of 2011.
It remains unclear as to whether the order, which spans a three-month period, represents a single instance, or is indicative of recurring cases of Verizon and other telephony providers being ordered to disclose all their clients' call records.
According to a copy of the order, Verizon is required to disclose the numbers of both parties during a call, as well as location, call duration, and other unique data on an "ongoing, daily basis.” Meaning that, regardless of whether an individual is suspected of or linked to any crime, the data of all Verizon customers is currently being delivered in bulk to the intelligence agency.
As to the authority claimed by the government via this order, that is specifically cited to fall under the “business records” provision of the PATRIOT Act of 2001, which was granted a four-year extension by President Obama in May of 2011.
It remains unclear as to whether the order, which spans a three-month period, represents a single instance, or is indicative of recurring cases of Verizon and other telephony providers being ordered to disclose all their clients' call records.

Reuters / Will Burgess
The order itself, signed by Judge Roger Vinson of the Foreign Intelligence Surveillance Court, prohibits Verizon from alerting its customers of the FBI’s request for their records.
The Obama administration confirmed that it is collecting massive numbers of telephone records from at least one carrier, but said that it is only recording data such as telephone numbers or call lengths, not subscribers' identities or the content of their calls.
Verizon has declined a request for comment by RT.
Though the agencies have yet to respond to the publication of the secret order, justification for the thus far unprecedented, warrantless request made to Verizon in April would fall under the interpretation of such “business records.” The latter applies to a wide-ranging amount of electronic “metadata,” though not the actual content of texts and voice calls.
The order seems likely to be associated with the NSA’s longstanding collection program over telephone, Internet and email data, which was secretly authorized by former president Bush in 2001, though not disclosed publicly until a 2006 USA Today report. That particular authorization applied to multiple carriers: AT&T, Verizon and BellSouth, and was intended to allow US intelligence services “to analyze calling patterns in an effort to detect terrorist activity."
Julian Sanchez, a surveillance expert with the libertarian Cato Institute who spoke to The Guardian believes that the newly disclosed court order undermines the legal definition of reasonable suspicion.
"We've certainly seen the government increasingly strain the bounds of 'relevance' to collect large numbers of records at once — everyone at one or two degrees of separation from a target — but vacuuming all metadata up indiscriminately would be an extraordinary repudiation of any pretense of constraint or particularized suspicion," said Sanchez.
The order seems likely to be associated with the NSA’s longstanding collection program over telephone, Internet and email data, which was secretly authorized by former president Bush in 2001, though not disclosed publicly until a 2006 USA Today report. That particular authorization applied to multiple carriers: AT&T, Verizon and BellSouth, and was intended to allow US intelligence services “to analyze calling patterns in an effort to detect terrorist activity."
Julian Sanchez, a surveillance expert with the libertarian Cato Institute who spoke to The Guardian believes that the newly disclosed court order undermines the legal definition of reasonable suspicion.
"We've certainly seen the government increasingly strain the bounds of 'relevance' to collect large numbers of records at once — everyone at one or two degrees of separation from a target — but vacuuming all metadata up indiscriminately would be an extraordinary repudiation of any pretense of constraint or particularized suspicion," said Sanchez.






![How Post-9/11 Surveillance Has Drastically Changed America [INFOGRAPHIC]](http://static6.businessinsider.com/image/5033fd3d6bb3f7f90300000f-140-140/how-post-911-surveillance-has-drastically-changed-america-infographic.jpg)


No comments:
Post a Comment