Update - July 3rd.....
A hack ......
https://krebsonsecurity.com/2014/07/microsoft-darkens-4mm-sites-in-malware-fight/







https://krebsonsecurity.com/2014/06/microsoft-kills-security-emails-blames-canada/







 Update, 5:39 p.m. ET: In an apparent reversal, Microsoft now says it will be re-instating the security notifications via email. Please read the update at the end of this post.
Update, 5:39 p.m. ET: In an apparent reversal, Microsoft now says it will be re-instating the security notifications via email. Please read the update at the end of this post.
http://rt.com/news/169532-russian-hackers-energy-industry/
http://www.bloomberg.com/news/2014-06-30/symantec-warns-energetic-bear-hackers-threaten-energy-firms.html
A hack ......

https://krebsonsecurity.com/2014/07/microsoft-darkens-4mm-sites-in-malware-fight/
Microsoft Darkens 4MM Sites in Malware Fight
Millions of Web sites were shuttered Monday morning after Microsoft executed a legal sneak attack against a malware network thought to be responsible for more than 7.4 million infections of Windows PCs worldwide.

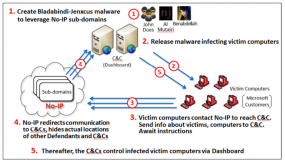
A diagram showing how crooks abused no-ip.com’s services to control malware networks. Source: Microsoft.
In its latest bid to harness the power of the U.S. legal system to combat malicious software and cybercrooks, Microsoft convinced a Nevada court to grant the software giant authority over nearly two dozen domains belonging to no-ip.com, a company that provides dynamic domain name services.
Dynamic DNS services are used to map domain names to numeric Internet address that may change frequently. Typically, the biggest users of dynamic DNS services are home Internet users who wish to have a domain name that will always point back to their home computer, no matter how many times their ISP changes the numeric Internet address assigned to that computer.
In this case, however, the attackers responsible for leveraging these two malware families — remote-access Trojans known as “njrat” and “njw0rm” — were using no-ip.com’s services to guarantee that PCs infected with this malware would always be able to reach the Internet servers that the attackers were using to control them.
Microsoft told the court that miscreants who were using these two malware strains were leveraging more than 18,400 hostnames that belonged to no-ip.com. On June 26, the court granted Microsoft the authority to temporarily seize control over 23 domains owned by no-ip.com — essentially all of the domains that power no-ip.com’ free dynamic DNS services.
Microsoft was supposed to filter out the traffic flowing to and from those 18,400+ hostnames, and allow the remaining, harmless traffic to flow through to its rightful destination. But according to no-ip.com marketing manager Natalie Gogun, that’s not at all what happened.
“They made comments that they’d only taken down bad hostnames and were supposedly redirecting all good traffic through to users, but it’s not happening, and they’re not able to handle our traffic volumes,” Gogun said. “Many legitimate users that use our services have been down all day.”
Gogun said while Microsoft claimed that there were more than 18,000 malicious hostnames involved, no-ip.com could only find a little more than 2,000 from that list that were still active as of Monday morning. Meanwhile, some four million hostnames remain offline, with customer support requests piling up.
“So, to go after 2,000 or so bad sites, [Microsoft] has taken down four million,” Gogun said.
Microsoft told the Nevada court that despite numerous reports released by Internet security firms over the past year about large volumes of malicious activity emanating form no-ip.com’s service, the company “consistently failed to take sufficient steps to correct, remedy, or prevent the abuse and to keep its domains free from malicious activity.”
But according to Gogun, the first time Microsoft brought its concerns to no-ip.com was at 7 a.m. on June 30, when the company’s CEO received a knock on the door of his family home and was served with a copy of the court order granting Microsoft authority over the 23 no-ip.com domains.
“We work with law enforcement all the time, and our abuse department responds to abuse requests within 24 hours,” Gogun said. “It’s pretty sad that Microsoft had to take such extreme measures to go about this.”
Gogun isn’t the only one who believes Microsoft swatted a fly with the equivalent of an atom bomb. Some of Microsoft’s previous legal sneak attacks targeted “bulletproof” hosting providers — those that promise to keep sketchy (and high-paying) customers online despite pressure from security firms and law enforcement. But according to Dmitri Alperovitch, co-founder of security firm CrowdStrike, treating no-ip.com like one of these shady providers is a mistake.
“They have always been very responsive to security researchers and law enforcement,” Alperovitch said of no-ip.com. “I do not consider them a bullet-proof or abuse-proof host.”
Meanwhile, Gogun said no-ip.com is considering its legal options for responding to the outage and to Microsoft’s allegations that the company somehow turns a blind eye to abuse complaints.
“We’re speaking with our lawyers about this, but right now we’re doing everything we can to fix this, and we need our users to understand that.”
In tandem with the action against no-ip.com, Microsoft also named two accused two men — software developers in Kuwait and Algeria — of authoring and selling the njrar and njw0rm.
The complaint against no-ip, the accused malware authors, and the rest of Microsoft’s various legal filings in this case are available at this link.
https://krebsonsecurity.com/2014/06/microsoft-kills-security-emails-blames-canada/
Microsoft Kills Security Emails, Blames Canada
In a move that may wind up helping spammers, Microsoft is blaming a new Canadian anti-spam law for the company’s recent decision to stop sending regular emails about security updates for its Windows operating system and other Microsoft software.
 Update, 5:39 p.m. ET: In an apparent reversal, Microsoft now says it will be re-instating the security notifications via email. Please read the update at the end of this post.
Update, 5:39 p.m. ET: In an apparent reversal, Microsoft now says it will be re-instating the security notifications via email. Please read the update at the end of this post.
Original story:
Last week, Microsoft sent the following notice to IT professionals and others who have signed up to receive email notices of security updates:
“As of July 1, 2014, due to changing governmental policies concerning the issuance of automated electronic messaging, Microsoft is suspending the use of email notifications that announce the following:”
* Security bulletin advance notifications
* Security bulletin summaries
* New security advisories and bulletins
* Major and minor revisions to security advisories and bulletins
* Security bulletin summaries
* New security advisories and bulletins
* Major and minor revisions to security advisories and bulletins
“In lieu of email notifications, you can subscribe to one or more of the RSS feeds described on the Security TechCenter website.”
“For more information, or to sign up for an RSS feed, visit the Microsoft Technical Security Notifications webpage at http://technet.microsoft.com/security/dd252948.”
Asked about the reason for the change, a Microsoft spokesperson said email communication was suspended to comply with a new Canadian anti-spam law that takes effect on July 1, 2014.
Some anti-spam experts who worked very closely on Canada’s Anti-Spam Law (CASL) say they are baffled by Microsoft’s response to a law which has been almost a decade in the making.
Neil Schwartzman, executive director of the Coalition Against Unsolicited Commercial Email(CAUCE), said CASL contains carve-outs for warranty and product safety and security alerts that would more than adequately exempt the Microsoft missives from the regulation.
Indeed, an exception in the law says it does not apply to commercial electronic messages that solely provide “warranty information, product recall information or safety or security information about a product, goods or a service that the person to whom the message is sent uses, has used or has purchased.”
“I am at a complete and total loss to understand how the people in Redmond made such an apparently panicked decision,” Schwartzman said,” noting that Microsoft was closely involved in the discussions in the Canadian parliament over the bill’s trajectory and content. “This is the first company I know of that’s been that dumb.”
Schwartzman said many companies have used CASL as an excuse to freshen up their email lists and to re-engage their customers. Some have even gone so far as to enter respondents who verify that they still want to receive email communications from a company into drawings for cash prizes and other giveaways.
“Over the past couple of weeks, I’ve seen nothing but a steady stream of reconfirmation mails from various companies,” he said. “I’m now in the running for several $500 dollar gift certificates because I confirmed my email. And at the bottom of each of these messages is a note that says ‘please ignore this offer if you’re not Canadian.’”
CAUCE board member Jeff Williams, a former group program manager at Microsoft’s Malware Protection Center, chalked Microsoft’s decision up to a little more than a tough call.
“I can imagine the discussion and wondering among the lawyers and [Microsoft] whether they should try to get hundreds of millions of opt-ins before June 30 or if they should change the way they share info,” Williams said. “I’m sure it wasn’t an wasn’t an easy decision, but I wouldn’t call it an overreaction.”
In addition to pushing notices about new updates out via Microsoft’s RSS feeds, the company also appears to be making the security email alerts available to users who have Live, Outlookor Hotmail accounts with Microsoft. And of course, readers can continue to rely on KrebsOnSecurity to feature information on any new security updates available from Microsoft, including each Patch Tuesday bundle as well as emergency, “out-of-band” updates released to address zero-day security threats.
Update, 5:40 p.m. ET: In an apparent reversal of its decision, Microsoft now says it will be re-starting its security notifications via email early next month. From a Microsoft’s spokesperson: “On June 27, 2014, Microsoft notified customers that we were suspending Microsoft Security Notifications due to changing governmental policies concerning the issuance of automated electronic messaging. We have reviewed our processes and will resume these security notifications with our monthly Advanced Notification Service (ANS) on July 3, 2014
Moon of Alabama....
Moon of Alabama....
NYT Claims "Russian Hacker" Attack Without Any Supporting Evidence
A 800 words New York times story on some alleged computer hacking of some energy companies mentions "Russian hackers" ten times.
From Hackers in Russia ... Russian hackers have ... Russian hackers are targeting ... The Russian attacks ... an unusually sophisticated and aggressive Russian group targeting ... believed the hackers were backed by the Russian government ... The Russian hackers ... the Russian hacking group ... The Russian hackers have ... the Russian group intended ...
The story includes zero (as in nil, none) evidence and no reasoning at all why the hackers involved are supposed to be "Russian".
It is the nature of the internet that geo-localizing the original source of an attack is nearly impossible. There are myriad ways hackers from anywhere could frame one country or group as an attacker. It is therefore highly irresponsible and nothing but pure hostile propaganda to attribute any such attack to a certain source, group or country without any further evidence and very sound and detailed technological reasoning.
The NYT story links to a Symantec report about the hacks. Symantec's sole reasoning on the source location, unmentioned in the NYT story, is this:
Analysis of the compilation timestamps on the malware used by the attackers indicate that the group mostly worked between Monday and Friday, with activity mainly concentrated in a nine-hour period that corresponded to a 9am to 6pm working day in the UTC +4 time zone. Based on this information, it is likely the attackers are based in Eastern Europe.
Such reasoning is much too basic to be of any evidence. The UTC +4 timezone includes not only west Russia but also other countries like Iran. It is also just as possible that the computers used for the compilation of the malware were sitting in Ohio, Tel Aviv or Nanking but had their clock settings changed to make it appear that they were in an UTC +4 working environment. Notice that Symantec named the source in question "Dragonfly" probably hinting that the attacks were originally though of as having an Asian origin.
It is highly irresponsible to publicly accuse a certain country as the source of this attack without having any further evidence to support such a claim. Doing so exposes the NYT as a vile propaganda paper again doing the U.S. war-hawk's bidding.
http://rt.com/news/169532-russian-hackers-energy-industry/
Industrial infection: Hackers put chokehold on energy firms with Stuxnet-like viruses
Hackers are targeting energy companies in the US and Europe in an apparent case of industrial espionage, according to several security companies, which say the perpetrators seem to be based in Eastern Europe.
The group of hackers, known as 'Energetic Bear' or 'Dragonfly', are attacking hundreds of Western oil and gas companies, as well as energy investment firms, and infecting them with malware capable of disrupting power supplies.
Additional targets have included energy grid operators, major electricity generation firms, petroleum pipeline operators, and industrial energy equipment providers. The majority of the victims were located in the United States, Spain, France, Italy, Germany, Turkey, and Poland, according to a Symantec report released on Monday.
The malware campaign is somewhat similar to Operation Olympic Games, an alleged cyberwarfare attacks mounted by the US and Israel that used a virus called Stuxnet to target the Iranian nuclear industry in July 2010. The attack was the first known major malware campaign to target industrial control system (ICS) equipment providers.
The US-Israeli operation was tailored against Iranian uranium enrichment facilities, but the Dragonfly attacks, while having signatures of a government-sponsored operation, are more ambitious, the IT security firm believes.
Espionage, potential sabotage
The hackers infect the industrial control software with a remote access-type (RAT) Trojan horse malware code – called Havex RAT – which gives them a “beachhead in the targeted organizations’ networks,” as well as the ability to sabotage infected ICS computers. The malware also allows the hackers to monitor energy consumption in real time and to potentially cripple physical systems such as wind turbines, gas pipelines and power plants through that software.
Symantec says the Dragonfly hackers have been in operation since at least 2011, and initially targeted defense and aviation companies in the US and Canada. The shift in focus to US and European energy firms occurred in early 2013.
That campaign began with phishing emails to top executives in targeted firms. Then Dragonfly began using watering hole attacks, which compromise websites likely to be visited by those working in the sector, then redirect visitors to websites hosting an exploit kit. That kit then delivers malware to the victims’ computers. Finally, the hackers began 'Trojanizing' legitimate software bundles belonging to three different ICS equipment manufacturers.
“Dragonfly bears the hallmarks of a state-sponsored operation, displaying a high degree of technical capability. The group is able to mount attacks through multiple vectors and compromise numerous third party websites in the process,” Symantec wrote in the report published on its blog.
Clever, sometimes unprofessional
Finnish security company F-Secure has also been tracking the use of the Havex malware. “The attackers behind Havex are conducting industrial espionage using a clever method. Trojanizing ICS... software installers is an effective method in gaining access to target systems, potentially even including critical infrastructure,” the company said on its blog.
F-Secure noted that “the group doesn't always manage the C&C's [command and control servers] in a professional manner, revealing lack of experience in operations.”
But its security analyst, Sean Sullivan, told Infosecurity that the group could well be state-sponsored.
“It fits the pattern of a nation state doing intelligence work, getting the lay of the land, in order to find exploitable systems for future 'need',” he argued.
Symantec, F-Secure and a third security company, CrowdStrike, all believe that cyber espionage is the main motive. “Dragonfly has targeted multiple organizations in the energy sector over a long period of time. Its main motive appears to be cyber espionage, with potential for sabotage a definite secondary capability,” Symantec said.
Russian trail?
Symantec analyzed the compilation of timestamps on the malware used by the hackers.
“The group mostly worked between Monday and Friday, with activity mainly concentrated in a nine-hour period that corresponded to a 9am to 6pm working day in the UTC +4 time zone. Based on this information, it is likely the attackers are based in Eastern Europe,” the Silicon Valley-based security company wrote.
CrowdStrike, also based in California, began tracking a group of hackers it called Energetic Bear in August 2012. Symantec believes that the group it calls Dragonfly and the group “known by other vendors as Energetic Bear” are the same.
In its 2013 Global Threat Report, CrowdStrike detailed the evidence that led it to believe Energetic Bear is a group of Russian hackers. Like Symantec, it noted the times of the attacks indicated Eastern Europe, but went further in its assessment.
“Targeted entities and countries are consistent with likely strategic interests of a Russia-based adversary. Several infected hosts were observed within the Russian Federation, but this could be the result of accidental compromise through large-scale SWC operations or deliberate efforts to conduct domestic internal monitoring,” the report said.
But among victims of the hacker group identified by F-Secure, the majority of which are based in Europe, there is a Russian construction company “that appears to specialize in structural engineering.”
http://www.bloomberg.com/news/2014-06-30/symantec-warns-energetic-bear-hackers-threaten-energy-firms.html
Russian Hackers Theaten Power Companies, Researchers Say
Save
 RT
RT


No comments:
Post a Comment