http://www.guardian.co.uk/world/2013/jun/07/obama-china-targets-cyber-overseas
( Who is dishing the goods to Glenn ? )

http://www.zerohedge.com/news/2013-06-07/shoot-prism-gate-messenger-obama-launch-criminal-probe-nsa-leaks
http://www.zerohedge.com/news/2013-06-07/obama-lying-about-big-brother
http://gizmodo.com/anonymous-just-leaked-a-trove-of-nsa-documents-511854773?utm_campaign=socialflow_gizmodo_twitter&utm_source=gizmodo_twitter&utm_medium=socialflow



The document is recent, dating to April 2013. Such a leak is extremely rare in the history of the NSA, which prides itself on maintaining a high level of secrecy.

( Who is dishing the goods to Glenn ? )
Obama orders US to draw up overseas target list for cyber-attacks
Exclusive: Top-secret directive steps up offensive cyber capabilities to 'advance US objectives around the world'
• Read the secret presidential directive here
• Read the secret presidential directive here

Obama's move to establish a cyber warfare doctrine will heighten fears over the increasing militarization of the internet. Photograph: Jim Young/Reuters
Barack Obama has ordered his senior national security and intelligence officials to draw up a list of potential overseas targets for US cyber-attacks, a top secret presidential directive obtained by the Guardian reveals.
The 18-page Presidential Policy Directive 20, issued in October last year but never published, states that what it calls Offensive Cyber Effects Operations (OCEO) "can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging".
It says the government will "identify potential targets of national importance where OCEO can offer a favorable balance of effectiveness and risk as compared with other instruments of national power".
The directive also contemplates the possible use of cyber actions inside the US, though it specifies that no such domestic operations can be conducted without the prior order of the president, except in cases of emergency.
The aim of the document was "to put in place tools and a framework to enable government to make decisions" on cyber actions, a senior administration official told the Guardian.
The administration published some declassified talking points from the directive in January 2013, but those did not mention the stepping up of America's offensive capability and the drawing up of a target list.
Obama's move to establish a potentially aggressive cyber warfare doctrine will heighten fears over the increasing militarization of the internet.
The directive's publication comes as the president plans to confront his Chinese counterpart Xi Jinping at a summit in California on Friday over alleged Chinese attacks on western targets.
Even before the publication of the directive, Beijing had hit back against US criticism, with a senior official claiming to have "mountains of data" on American cyber-attacks he claimed were every bit as serious as thoseChina was accused of having carried out against the US.
Presidential Policy Directive 20 defines OCEO as "operations and related programs or activities … conducted by or on behalf of the United StatesGovernment, in or through cyberspace, that are intended to enable or produce cyber effects outside United States government networks."
Asked about the stepping up of US offensive capabilities outlined in the directive, a senior administration official said: "Once humans develop the capacity to build boats, we build navies. Once you build airplanes, we build air forces."
The official added: "As a citizen, you expect your government to plan for scenarios. We're very interested in having a discussion with our international partners about what the appropriate boundaries are."
The document includes caveats and precautions stating that all US cyber operations should conform to US and international law, and that any operations "reasonably likely to result in significant consequences require specific presidential approval".
The document says that agencies should consider the consequences of any cyber-action. They include the impact on intelligence-gathering; the risk of retaliation; the impact on the stability and security of the internet itself; the balance of political risks versus gains; and the establishment of unwelcome norms of international behaviour.
Among the possible "significant consequences" are loss of life; responsive actions against the US; damage to property; serious adverse foreign policy or economic impacts.
The US is understood to have already participated in at least one major cyber attack, the use of the Stuxnet computer worm targeted on Iranian uranium enrichment centrifuges, the legality of which has been the subject of controversy. US reports citing high-level sources within the intelligence services said the US and Israel were responsible for the worm.
In the presidential directive, the criteria for offensive cyber operations in the directive is not limited to retaliatory action but vaguely framed as advancing "US national objectives around the world".
The revelation that the US is preparing a specific target list for offensive cyber-action is likely to reignite previously raised concerns of security researchers and academics, several of whom have warned that large-scale cyber operations could easily escalate into full-scale military conflict.
Sean Lawson, assistant professor in the department of communication at the University of Utah, argues: "When militarist cyber rhetoric results in use of offensive cyber attack it is likely that those attacks will escalate into physical, kinetic uses of force."
An intelligence source with extensive knowledge of the National Security Agency's systems told the Guardian the US complaints again China were hypocritical, because America had participated in offensive cyber operations and widespread hacking – breaking into foreign computer systems to mine information.
Provided anonymity to speak critically about classified practices, the source said: "We hack everyone everywhere. We like to make a distinction between us and the others. But we are in almost every country in the world."
The US likes to haul China before the international court of public opinion for "doing what we do every day", the source added.
One of the unclassified points released by the administration in January stated: "It is our policy that we shall undertake the least action necessary to mitigate threats and that we will prioritize network defense and law enforcement as preferred courses of action."
The full classified directive repeatedly emphasizes that all cyber-operations must be conducted in accordance with US law and only as a complement to diplomatic and military options. But it also makes clear how both offensive and defensive cyber operations are central to US strategy.
Under the heading "Policy Reviews and Preparation", a section marked "TS/NF" - top secret/no foreign - states: "The secretary of defense, the DNI [Director of National Intelligence], and the director of the CIA … shall prepare for approval by the president through the National Security Advisor a plan that identifies potential systems, processes and infrastructure against which the United States should establish and maintain OCEO capabilities…" The deadline for the plan is six months after the approval of the directive.
The directive provides that any cyber-operations "intended or likely to produce cyber effects within the United States" require the approval of the president, except in the case of an "emergency cyber action". When such an emergency arises, several departments, including the department of defense, are authorized to conduct such domestic operations without presidential approval.
Obama further authorized the use of offensive cyber attacks in foreign nations without their government's consent whenever "US national interests and equities" require such nonconsensual attacks. It expressly reserves the right to use cyber tactics as part of what it calls "anticipatory action taken against imminent threats".
The directive makes multiple references to the use of offensive cyber attacks by the US military. It states several times that cyber operations are to be used only in conjunction with other national tools and within the confines of law.
When the directive was first reported, lawyers with the Electronic PrivacyInformation Center filed a Freedom of Information Act request for it to be made public. The NSA, in a statement, refused to disclose the directive on the ground that it was classified.
In January, the Pentagon announced a major expansion of its Cyber Command Unit, under the command of General Keith Alexander, who is also the director of the NSA. That unit is responsible for executing both offensive and defensive cyber operations.
Earlier this year, the Pentagon publicly accused China for the first time of being behind attacks on the US. The Washington Post reported last month that Chinese hackers had gained access to the Pentagon's most advanced military programs.
The director of national intelligence, James Clapper, identified cyber threats in general as the top national security threat.
Obama officials have repeatedly cited the threat of cyber-attacks to advocate new legislation that would vest the US government with greater powers to monitor and control the internet as a means of guarding against such threats.
One such bill currently pending in Congress, the Cyber Intelligence Sharing and Protection Act (Cispa), has prompted serious concerns from privacy groups, who say that it would further erode online privacy while doing little to enhance cyber security.
In a statement, Caitlin Hayden, national security council spokeswoman, said: "We have not seen the document the Guardian has obtained, as they did not share it with us. However, as we have already publicly acknowledged, last year the president signed a classified presidential directive relating to cyber operations, updating a similar directive dating back to 2004. This step is part of the administration's focus on cybersecurity as a top priority. The cyber threat has evolved, and we have new experiences to take into account.
"This directive establishes principles and processes for the use of cyber operations so that cyber tools are integrated with the full array of national security tools we have at our disposal. It provides a whole-of-government approach consistent with the values that we promote domestically and internationally as we have previously articulated in the International Strategy for Cyberspace.
"This directive will establish principles and processes that can enable more effective planning, development, and use of our capabilities. It enables us to be flexible, while also exercising restraint in dealing with the threats we face. It continues to be our policy that we shall undertake the least action necessary to mitigate threats and that we will prioritize network defense and law enforcement as the preferred courses of action. The procedures outlined in this directive are consistent with the US Constitution, including the president's role as commander in chief, and other applicable law and policies."
Shoot The PRISM-Gate Messenger: Obama To Launch Criminal Probe Into NSA Leaks
Submitted by Tyler Durden on 06/07/2013 21:29 -0400
Suddenly embroiled in too many scandals to even list, and humiliated by a publicly-exposed (because everyone knew about the NSA superspy ambitions before, but with one major difference: it was a conspiracy theory.... now it is a conspiracy fact) surveillance scandal that makes Tricky Dick look like an amateur, earlier today, as expected, Obama came out and publicly declared "I am not a hacker" and mumbled something about "security", "privacy" and "inconvenience." He went on to explain how the government "welcomes the debate" of all three in the aftermath of the public disclosure that every form of electronic communication is intercepted and stored by the US government (now that said interception is no longer secret, of course) but more importantly how it is only the government, which is naturally here to help, that should be the ultimate arbiter in deciding what is best for all.
Yet the PRISM-gate scandal which is sure to only get worse with time as Americans slowly realize they are living in a Orwellian police state, meant Obama would have to do more to appease a public so furious even the NYT issued a scathing editorial lamenting the obliteration of Obama's credibility. Sure enough, the president did. Reuters reports that the first course of action by the US government will be to... shoot the messenger.
Reuters reports that "President Barack Obama's administration is likely to open a criminal investigation into the leaking of highly classified documents that revealed the secret surveillance of Americans' telephone and email traffic, U.S. officials said on Friday."
And how did Reuters learn this: from "law enforcement and security officials who were not authorized to speak publicly."
The mimetic absurdity of the narrative is just too surreal to even contemplate for more than a minute before bursting out in laughter: the administration's plans to launch criminal charges against those who "leaked" its Nixonian espionage masterplan involving every US (and world) citizen using the Internet, revealed by another group of sources leaking in secret. Pure poetry.
Of course, this was inevitable - once you start down the path of a totalitarian surveillance superstate, you don't stop until all dissent is crushed: either peacefully through submission to debt serfdom, or, well, not so peacefully.
It was unclear on Friday whether a complaint had been submitted by the publicity-shy National Security Agency, which was most directly involved in the collection of trillions of telephone and email communications.However, one U.S. official with knowledge of the situation said that given the extent and sensitivity of the recent leaks, federal law may compel officials to open an investigation.A criminal probe would represent another turn in the Obama administration's battle against national security leaks. This effort has been under scrutiny lately because of a Justice Department investigation that has involved searches of the phone records of Associated Press journalists and a Fox News reporter.
But what's worst, is that it may all turn very personal against the same journalists who dared to divulge the NSA's spy-op:
Journalists involved in The Guardian and Washington Post articles have reported in depth on WikiLeaks, the website known for publishing secret U.S. government documents.The Post report on the PRISM program was co-written by Laura Poitras, a filmmaker who has been working on a documentary on WikiLeaks, with the cooperation of its founder Julian Assange, and who last year made a short film about Bill Binney, a former NSA employee who became a whistleblowing critic of the agency.Last year, the web magazine Salon published a lengthy article by the author of the Guardian report, Glenn Greenwald, accusing U.S. authorities of harassing Poitras when she left and re-entered the United States. Greenwald also has written frequently about Assange.The Guardian and Post stories appeared in the same week that U.S. Army Private First Class Bradley Manning went on trial in Maryland accused of leaking hundreds of thousands of classified documents to WikiLeaks.In an email to Reuters on Friday, Poitras rejected the notion that the trial had any impact on the timing of her story."I am fully aware we are living in a political climate where national security reporting is being targeted by the government, however, I don't think fear should stop us from reporting these stories," Poitras wrote."To suggest that the timing of the NSA PRISM story is linked in any way to other events or stories I'm following is simply wrong. Like any journalist, I have many contacts and follow multiple stories."Kris Coratti, a Washington Post spokeswoman, said the timing of the paper's publication of Poitras' story had nothing to do with Manning's trial and that Assange had played no role in arranging or encouraging the story.Greenwald did not respond to emailed requests for comment. The Guardian's editor-in-chief, Alan Rusbridger, declined to comment.
Needless to say, once political retribution for publicizing the nuances of the police state becomes a personal affair targeting the very journalists whose task is to provide much needed information, the first amendment is basically finished.
Alas, on the path to tyranny the loss of rights and privileges, let alone the occasional amendment written on a very old parchment and which nobody follows or cares about, is inevitable.
And it is up to the citizens of such a tyrannical government to reclaim their nation. Which they will... Just as soon as The Bachelorette/Big Brother (no pun intended)/X Factor is over and the next disability check clears.
Is Obama Lying About Big Brother?
Submitted by Tyler Durden on 06/07/2013 12:36 -0400
As of this moment, Obama is making the case that the US government is not eavesdropping on phone calls. Specifically, he said "nobody is listening to your phone calls - they are just looking at phone numbers and duration of calls" and concluded that the NSA was only engaged in "modest encroachments." It was unclear if that clarification was meant to put to rest fears that Big Brother has made personal privacy a thing of the past. He further went on to add that the telephone surveillance program is fully vetted by Congress and supervised by the Federal Intelligence Surveillance Court (FISA). In other words: Obama is making the case that the NSA's Big Brother supervision is perfectly legal and not only that, there are checks and balances and neither the telephonic snooping nor the internet supervision is anything to be concerned about. There is one problem: Obama is lying.
Back in April 2009, three months into the Obama regime, none other than the NSA admitted it has overstepped its legal boundaries. As the NYT reported: "The National Security Agency intercepted private e-mail messages and phone calls of Americans in recent months on a scale that went beyond the broad legal limits established by Congress last year, government officials said in recent interviews. "
Several intelligence officials, as well as lawyers briefed about the matter, said the N.S.A. had been engaged in “overcollection” of domestic communications of Americans. They described the practice as significant and systemic, although one official said it was believed to have been unintentional.The Justice Department, in response to inquiries from The New York Times, acknowledged Wednesday night that there had been problems with the N.S.A. surveillance operation, but said they had been resolved.As part of a periodic review of the agency’s activities, the department “detected issues that raised concerns,” it said. Justice Department officials then “took comprehensive steps to correct the situation and bring the program into compliance” with the law and court orders, the statement said. It added that Attorney General Eric H. Holder Jr. went to the national security court to seek a renewal of the surveillance program only after new safeguards were put in place.
The same Eric Holder who is currently being investigated for perjury before congress. As for "compliance" 4 years later it seems nothing has changed.
As for Obama's clear conscience:
The legal and operational problems surrounding the N.S.A.’s surveillance activities have come under scrutiny from the Obama administration, Congressional intelligence committees and a secret national security court, said the intelligence officials, who spoke only on the condition of anonymity because N.S.A. activities are classified.Classified government briefings have been held in recent weeks in response to a brewing controversy that some officials worry could damage the credibility of legitimate intelligence-gathering efforts.
Well thank god the most transparent administration held classified briefings to discuss the biggest government espionage program ever conceived. One may have gotten ideas otherwise...
Finally, on Obama's pinky swear that it is only foreigners' emails and iMessages that are being intercepted, turns out he is lying here too:
In recent weeks, theeavesdropping agency notified members of the Congressional intelligence committees that it had encountered operational and legal problems in complying with the new wiretapping law, Congressional officials said.Officials would not discuss details of the overcollection problem because it involves classified intelligence-gathering techniques. But the issue appears focused in part on technical problems in the N.S.A.’s ability at times to distinguish between communications inside the United States and those overseas as it uses its access to American telecommunications companies’ fiber-optic lines and its own spy satellites to intercept millions of calls and e-mail messages.
And so on.
In short: what difference does it make - it is only the stripping of the most fundamental privacy rights of US citizens! And how else can you build a totalitarian government if you don't give up some freedoms - good heavens, one can't ask the poor president to provide 100% security without experiencing some "inconvenience" and handing over a little privacy. Or a lot.
In the end, let's not forget what really matters: the NSA spying program is from the government, and it is here to help you.
* * *
Finally, here is Matt Damon explaining why he wouldn't work for the NSA:
and.....
Anonymous Just Leaked a Trove of NSA Documents
In the wake of last night’s revelation that everyone in the world has a creepy NSA-shaped stalker, defenders of online liberty and generally angry internet peopleAnonymous have leaked a treasure trove of NSA documents, including seriously important stuff like the US Department of Defense’s ‘Strategic Vision’ for controlling the internet.
The documents — 13 in total — were posted online, along with an accompanying message full of the normal Anonymous bluster: people won’t be silenced, they have the memory of trivia-master elephants, the governments of the world will fall, your average press release really.
The documents seem to mostly relate to PRISM and supporting operations, and mostly date from around 2008, supposedly not long after PRISM first reared its ugly head. One of the key things Anonymous has highlighted from the documents is the existence of an “intelligence-sharing network” that shares data gleaned from PRISM with “intelligence partners” around the world. Although we’re still in the process of combing through the documents, you can bet your last Bitcoin that ‘intelligence’ has been shared with British security services.
Hit up the documents for further details; just be warned that although this might look like the plot of a B-list movie starring Aston Kutcher, the docs themselves are incredibly dry and full of more acronyms than whatever presentation you should be working on. [Pastebin]
http://www.guardian.co.uk/world/2013/jun/06/us-tech-giants-nsa-data
NSA Prism program taps in to user data of Apple, Google and others
• Top-secret Prism program claims direct access to servers of firms including Google, Apple and Facebook
• Companies deny any knowledge of program in operation since 2007
• Obama orders US to draw up overseas target list for cyber-attacks
• Companies deny any knowledge of program in operation since 2007
• Obama orders US to draw up overseas target list for cyber-attacks

A slide depicting the top-secret PRISM program.
The National Security Agency has obtained direct access to the systems of Google, Facebook, Apple and other US internet giants, according to a top secret document obtained by the Guardian.
The NSA access is part of a previously undisclosed program called Prism, which allows officials to collect material including search history, the content of emails, file transfers and live chats, the document says.
The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation – classified as top secret with no distribution to foreign allies – which was apparently used to train intelligence operatives on the capabilities of the program. The document claims "collection directly from the servers" of major US service providers.
Although the presentation claims the program is run with the assistance of the companies, all those who responded to a Guardian request for comment on Thursday denied knowledge of any such program.
In a statement, Google said: "Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'back door' into our systems, but Google does not have a back door for the government to access private user data."
Several senior tech executives insisted that they had no knowledge of Prism or of any similar scheme. They said they would never have been involved in such a program. "If they are doing this, they are doing it without our knowledge," one said.
An Apple spokesman said it had "never heard" of Prism.
The NSA access was enabled by changes to US surveillance law introduced under President Bush and renewed under Obama in December 2012.

The program facilitates extensive, in-depth surveillance on live communications and stored information. The law allows for the targeting of any customers of participating firms who live outside the US, or those Americans whose communications include people outside the US.
It also opens the possibility of communications made entirely within the US being collected without warrants.
Disclosure of the Prism program follows a leak to the Guardian on Wednesday of a top-secret court order compelling telecoms provider Verizon to turn over the telephone records of millions of US customers.
The participation of the internet companies in Prism will add to the debate, ignited by the Verizon revelation, about the scale of surveillance by the intelligence services. Unlike the collection of those call records, this surveillance can include the content of communications and not just the metadata.
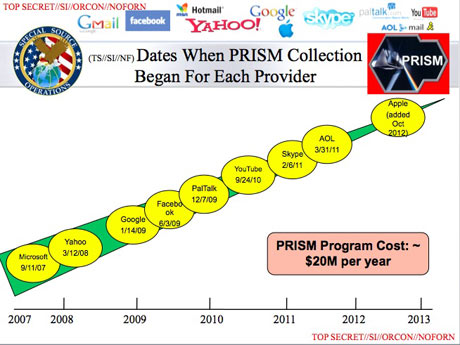
Some of the world's largest internet brands are claimed to be part of the information-sharing program since its introduction in 2007. Microsoft – which is currently running an advertising campaign with the slogan "Yourprivacy is our priority" – was the first, with collection beginning in December 2007.
It was followed by Yahoo in 2008; Google, Facebook and PalTalk in 2009; YouTube in 2010; Skype and AOL in 2011; and finally Apple, which joined the program in 2012. The program is continuing to expand, with other providers due to come online.
Collectively, the companies cover the vast majority of online email, search, video and communications networks.

The extent and nature of the data collected from each company varies.
Companies are legally obliged to comply with requests for users' communications under US law, but the Prism program allows the intelligence services direct access to the companies' servers. The NSA document notes the operations have "assistance of communications providers in the US".
The revelation also supports concerns raised by several US senators during the renewal of the Fisa Amendments Act in December 2012, who warned about the scale of surveillance the law might enable, and shortcomings in the safeguards it introduces.
When the FAA was first enacted, defenders of the statute argued that a significant check on abuse would be the NSA's inability to obtain electronic communications without the consent of the telecom and internet companies that control the data. But the Prism program renders that consent unnecessary, as it allows the agency to directly and unilaterally seize the communications off the companies' servers.
A chart prepared by the NSA, contained within the top-secret document obtained by the Guardian, underscores the breadth of the data it is able to obtain: email, video and voice chat, videos, photos, voice-over-IP (Skype, for example) chats, file transfers, social networking details, and more.

The document is recent, dating to April 2013. Such a leak is extremely rare in the history of the NSA, which prides itself on maintaining a high level of secrecy.
The Prism program allows the NSA, the world's largest surveillance organisation, to obtain targeted communications without having to request them from the service providers and without having to obtain individual court orders.
With this program, the NSA is able to reach directly into the servers of the participating companies and obtain both stored communications as well as perform real-time collection on targeted users.
The presentation claims Prism was introduced to overcome what the NSA regarded as shortcomings of Fisa warrants in tracking suspected foreign terrorists. It noted that the US has a "home-field advantage" due to housing much of the internet's architecture. But the presentation claimed "Fisa constraints restricted our home-field advantage" because Fisa required individual warrants and confirmations that both the sender and receiver of a communication were outside the US.
"Fisa was broken because it provided privacy protections to people who were not entitled to them," the presentation claimed. "It took a Fisa court order to collect on foreigners overseas who were communicating with other foreigners overseas simply because the government was collecting off a wire in the United States. There were too many email accounts to be practical to seek Fisas for all."
The new measures introduced in the FAA redefines "electronic surveillance" to exclude anyone "reasonably believed" to be outside the USA – a technical change which reduces the bar to initiating surveillance.
The act also gives the director of national intelligence and the attorney general power to permit obtaining intelligence information, and indemnifies internet companies against any actions arising as a result of co-operating with authorities' requests.
In short, where previously the NSA needed individual authorisations, and confirmation that all parties were outside the USA, they now need only reasonable suspicion that one of the parties was outside the country at the time of the records were collected by the NSA.
The document also shows the FBI acts as an intermediary between other agencies and the tech companies, and stresses its reliance on the participation of US internet firms, claiming "access is 100% dependent on ISP provisioning".
In the document, the NSA hails the Prism program as "one of the most valuable, unique and productive accesses for NSA".
It boasts of what it calls "strong growth" in its use of the Prism program to obtain communications. The document highlights the number of obtained communications increased in 2012 by 248% for Skype – leading the notes to remark there was "exponential growth in Skype reporting; looks like the word is getting out about our capability against Skype". There was also a 131% increase in requests for Facebook data, and 63% for Google.
The NSA document indicates that it is planning to add Dropbox as a PRISM provider. The agency also seeks, in its words, to "expand collection services from existing providers".
The revelations echo fears raised on the Senate floor last year during the expedited debate on the renewal of the FAA powers which underpin the PRISM program, which occurred just days before the act expired.
Senator Christopher Coons of Delaware specifically warned that the secrecy surrounding the various surveillance programs meant there was no way to know if safeguards within the act were working.
"The problem is: we here in the Senate and the citizens we represent don't know how well any of these safeguards actually work," he said.
"The law doesn't forbid purely domestic information from being collected. We know that at least one Fisa court has ruled that the surveillance program violated the law. Why? Those who know can't say and average Americans can't know."
Other senators also raised concerns. Senator Ron Wyden of Oregon attempted, without success, to find out any information on how many phone calls or emails had been intercepted under the program.
When the law was enacted, defenders of the FAA argued that a significant check on abuse would be the NSA's inability to obtain electronic communications without the consent of the telecom and internet companies that control the data. But the Prism program renders that consent unnecessary, as it allows the agency to directly and unilaterally seize the communications off the companies' servers.
When the NSA reviews a communication it believes merits further investigation, it issues what it calls a "report". According to the NSA, "over 2,000 Prism-based reports" are now issued every month. There were 24,005 in 2012, a 27% increase on the previous year.
In total, more than 77,000 intelligence reports have cited the PRISM program.
Jameel Jaffer, director of the ACLU's Center for Democracy, that it was astonishing the NSA would even ask technology companies to grant direct access to user data.
"It's shocking enough just that the NSA is asking companies to do this," he said. "The NSA is part of the military. The military has been granted unprecedented access to civilian communications.
"This is unprecedented militarisation of domestic communications infrastructure. That's profoundly troubling to anyone who is concerned about that separation."
A senior administration official said in a statement: "The Guardian and Washington Post articles refer to collection of communications pursuant to Section 702 of the Foreign Intelligence Surveillance Act. This law does not allow the targeting of any US citizen or of any person located within the United States.
"The program is subject to oversight by the Foreign Intelligence Surveillance Court, the Executive Branch, and Congress. It involves extensive procedures, specifically approved by the court, to ensure that only non-US persons outside the US are targeted, and that minimize the acquisition, retention and dissemination of incidentally acquired information about US persons.
"This program was recently reauthorized by Congress after extensive hearings and debate.
"Information collected under this program is among the most important and valuable intelligence information we collect, and is used to protect our nation from a wide variety of threats.
"The Government may only use Section 702 to acquire foreign intelligence information, which is specifically, and narrowly, defined in the Foreign Intelligence Surveillance Act. This requirement applies across the board, regardless of the nationality of the target."
http://www.guardian.co.uk/commentisfree/2013/jun/07/whistleblowers-and-leak-investigations
On whistleblowers and government threats of investigation
No healthy democracy can endure when the most consequential acts of those in power remain secret and unaccountable

James Clapper, the US director of national intelligence, who called the Guardian's revelations 'reprehensible'. Photograph: Michael Reynolds/EPA
We followed Wednesday's story about the NSA's bulk telephone record-gathering with one yesterday about the agency's direct access to the servers of the world's largest internet companies. I don't have time at the moment to address all of the fallout because - to borrow someone else's phrase - I'm Looking Forward to future revelations that are coming (and coming shortly), not Looking Backward to ones that have already come.
But I do want to make two points. One is about whistleblowers, and the other is about threats of investigations emanating from Washington:
1) Ever since the Nixon administration broke into the office of Daniel Ellsberg's psychoanalyst's office, the tactic of the US government has been to attack and demonize whistleblowers as a means of distracting attention from their own exposed wrongdoing and destroying the credibility of the messenger so that everyone tunes out the message. That attempt will undoubtedly be made here.
I'll say more about all that shortly, but for now: as these whistleblowing acts becoming increasingly demonized ("reprehensible", declaredDirector of National Intelligence James Clapper yesterday), please just spend a moment considering the options available to someone with access to numerous Top Secret documents.
They could easily enrich themselves by selling those documents for huge sums of money to foreign intelligence services. They could seek to harm the US government by acting at the direction of a foreign adversary and covertly pass those secrets to them. They could gratuitously expose the identity of covert agents.
None of the whistleblowers persecuted by the Obama administration as part of its unprecedented attack on whistleblowers has done any of that: not one of them. Nor have those who are responsible for these current disclosures.
They did not act with any self-interest in mind. The opposite is true: they undertook great personal risk and sacrifice for one overarching reason: to make their fellow citizens aware of what their government is doing in the dark. Their objective is to educate, to democratize, to create accountability for those in power.
The people who do this are heroes. They are the embodiment of heroism. They do it knowing exactly what is likely to be done to them by the planet's most powerful government, but they do it regardless. They don't benefit in any way from these acts. I don't want to over-simplify: human beings are complex, and usually act with multiple, mixed motives. But read this outstanding essay on this week's disclosures from The Atlantic's security expert, Bruce Schneier, to understand why these brave acts are so crucial.
Those who step forward to blow these whistles rarely benefit at all. The ones who benefit are you. You discover what you should know but what is hidden from you: namely, the most consequential acts being taken by those with the greatest power, and how those actions are affecting your life, your country and your world.
In 2008, candidate Obama decreed that "often the best source of information about waste, fraud, and abuse in government is an existing government employee committed to public integrity and willing to speak out," and he hailed whistleblowing as:
"acts of courage and patriotism, which can sometimes save lives and often save taxpayer dollars, should be encouraged rather than stifled as they have been during the Bush administration."
The current incarnation of Obama prosecutes those same whistlelblowers at double the number of all previous presidents combined, and spent the campaign season boasting about it.
The 2008 version of Obama was right. As the various attacks are inevitably unleashed on the whistleblower(s) here, they deserve the gratitude and - especially - the support of everyone, including media outlets, for the noble acts that they have undertaken for the good of all of us. When it comes to what the Surveillance State is building and doing in the dark, we are much more informed today than we were yesterday, and will be much more informed tomorrow than we are today, thanks to them.
(2) Like puppets reading from a script, various Washington officials almost immediately began spouting all sorts of threats about "investigations" they intend to launch about these disclosures. This has been their playbook for several years now: they want to deter and intimidate anyone and everyone who might shed light on what they're doing with their abusive, manipulative exploitation of the power of law to punish those who bring about transparency.
That isn't going to work. It's beginning completely to backfire on them. It's precisely because such behavior reveals their true character, their propensity to abuse power, that more and more people are determined to bring about accountability and transparency for what they do.
They can threaten to investigate all they want. But as this week makes clear, and will continue to make clear, the ones who will actually be investigated are them.
The way things are supposed to work is that we're supposed to know virtually everything about what they do: that's why they're called publicservants. They're supposed to know virtually nothing about what we do: that's why we're called private individuals.
This dynamic - the hallmark of a healthy and free society - has been radically reversed. Now, they know everything about what we do, and are constantly building systems to know more. Meanwhile, we know less and less about what they do, as they build walls of secrecy behind which they function. That's the imbalance that needs to come to an end. No democracy can be healthy and functional if the most consequential acts of those who wield political power are completely unknown to those to whom they are supposed to be accountable.
There seems to be this mentality in Washington that as soon as they stamp TOP SECRET on something they've done we're all supposed to quiver and allow them to do whatever they want without transparency or accountability under its banner. These endless investigations and prosecutions and threats are designed to bolster that fear-driven dynamic. But it isn't working. It's doing the opposite.
The times in American history when political power was constrained was when they went too far and the system backlashed and imposed limits. That's what happened in the mid-1970s when the excesses of J Edgar Hoover and Richard Nixon became so extreme that the legitimacy of the political system depended upon it imposing restraints on itself. And that's what is happening now as the government continues on its orgies of whistleblower prosecutions, trying to criminalize journalism, and building a massive surveillance apparatus that destroys privacy, all in the dark. The more they overreact to measures of accountability and transparency - the more they so flagrantly abuse their power of secrecy and investigations and prosecutions - the more quickly that backlash will arrive.
I'm going to go ahead and take the Constitution at its word that we're guaranteed the right of a free press. So, obviously, are other people doing so. And that means that it isn't the people who are being threatened who deserve and will get the investigations, but those issuing the threats who will get that. That's why there's a free press. That's what adversarial journalism means.
BY the way - are the tech giants " voluntarily participating in Prism ? Do you buy what Goggle is selling ?
http://hotair.com/archives/2013/06/07/mystery-deepens-are-tech-behemoths-participating-in-prism-voluntarily/
Mystery deepens: Are tech behemoths participating in PRISM voluntarily?
POSTED AT 6:41 PM ON JUNE 7, 2013 BY ALLAHPUNDIT
Go look at this post at TechCrunch rounding up reaction from Google, Facebook, Apple, etc. All of them deny giving the feds “direct access” to their servers; some of them claim never to have even heard of PRISM until WaPo’s story yesterday. “But wait,” you say, “what if they’re being slippery in their statements and they actually gave the feds indirect access to their servers?” That’s possible. Other people have noticed that loophole too.
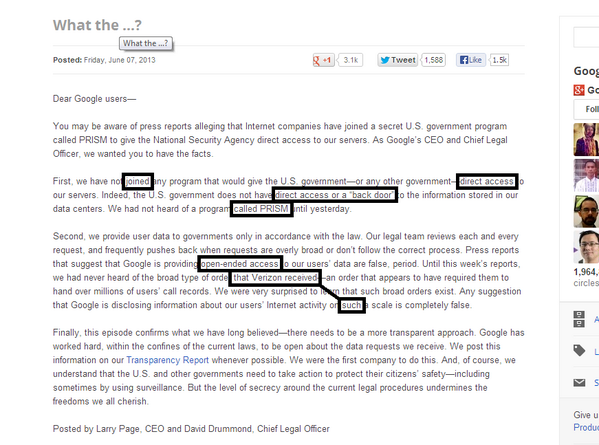
But what to make of this new statement on Google’s blog, signed by CEO Larry Page himself?
First, we have not joined any program that would give the U.S. government—or any other government—direct access to our servers. Indeed, the U.S. government does not have direct access or a “back door” to the information stored in our data centers. We had not heard of a program called PRISM until yesterday.Second, we provide user data to governments only in accordance with the law. Our legal team reviews each and every request, and frequently pushes back when requests are overly broad or don’t follow the correct process.Press reports that suggest that Google is providing open-ended access to our users’ data are false, period. Until this week’s reports, we had never heard of the broad type of order that Verizon received—an order that appears to have required them to hand over millions of users’ call records. We were very surprised to learn that such broad orders exist. Any suggestion that Google is disclosing information about our users’ Internet activity on such a scale is completely false.Finally, this episode confirms what we have long believed—there needs to be a more transparent approach. Google has worked hard, within the confines of the current laws, to be open about the data requests we receive. We post this information on our Transparency Report whenever possible. We were the first company to do this. And, of course, we understand that the U.S. and other governments need to take action to protect their citizens’ safety—including sometimes by using surveillance. But the level of secrecy around the current legal procedures undermines the freedoms we all cherish.
Emphasis mine. Even if Google’s not allowing the feds any access, directly or indirectly, to their servers, you can imagine them handing over the data contained in those servers pursuant to a broooooad order issued “in accordance with the law.” But the second boldface bit says they’re not doing that. As far as I can tell, this amounts to a flat denial of voluntary participation. Plus, if they are participating voluntarily somehow, they’d be much better off with a terse statement signed by a random PR official simply saying that they don’t provide “direct” access to servers and they comply with applicable laws, which would put the heat back on Congress for making PRISM possible in the first place. Instead you have an elaborate denial here emphasizing that they don’t deal with very broad requests for information signed by the company’s CEO. If Google’s being cute in using weasel words to hide its complicity, it’ll look even worse when the truth of their compliance comes out. So maybe they’re not being cute. Maybe they’re really not participating in this voluntarily.
But in that case … what’s going on? Three obvious possibilities. One: They’re not participating voluntarily. Somehow PRISM’s lifting the data off of their servers without them knowing it. Which, if true, takes this story from bombshell to atomic bombshell. Two: Page and his counterparts at the other tech behemoths are flat-out lying. As noted above, it would be risky for them to do that given the breach of trust that would result if/when their lie is exposed. Some people on Twitter are speculating that they’re being required to lie, per some sort of provision of the Patriot Act, but I’ve never heard of a law that does that. Even if there were a secret law that did, one of the tech behemoths could have exposed it when the feds approached them about PRISM and the resulting scandal would have exploded in Obama’s face. Plus, a tech reporter tweeted me to note that Google’s locked in other litigation with the FBI; they’re not afraid to challenge the feds on national security issues.
Three: There’s something fishy about the details of PRISM as reported by WaPo and the Guardian. Read this post at Business Insider rounding up some of the odder details of the story, from the suspiciously amateurish Powerpoint slides to the odd timing of the revelations to the implausibly low pricetag for the program. ($20 million a year to harvest data from nearly the entire Internet?) There’s no question that a program called PRISM exists — other news sources have independently confirmed its existence since WaPo’s story came out — but there is some question as to whether it’s as extensive and intrusive as the WaPo report claims. James Clapper’s statement last night also accused WaPo of “numerous inaccuracies” in its story. Hmmmmmm.
Exit question: If WaPo’s scoop was bogus in some material way, wouldn’t Obama have emphasized that in his remarks this afternoon? Why let a damaging story that’s false in key respects gain traction when you can shoot it down in front of a national audience?
Update: Mark Zuckerberg just issued his own statement and, as Andy Levy notes on Twitter, it’s similar to Page’s. Very similar. Extremely similar, in fact. Hmmm.
Update: Matt Yglesias spots more weasel words in Google’s statement:
http://hotair.com/archives/2013/06/07/video-did-the-nsa-director-lie-to-congress/
Video: Did the NSA director lie to Congress?
POSTED AT 12:01 PM ON JUNE 7, 2013 BY ED MORRISSEY
First off, let’s marvel at the unexpected genius of Rep. Hank Johnson (D-GA), who turns out to be Congress’ most adept perjury-trap specialist, perhaps of all time. Recall that it was Johnson’s gentle and friendly softball question on May 15th that ended up encouraging Eric Holder to categorically deny that he’d ever heard or or been involved in the potential prosecution of a reporter under the Espionage Act of 1917 … eight days before the warrant he personally approved making that argument in 2010 surfaced. In an exchange from March 2012, Johnson had an opportunity to question NSA Director Keith Alexander about precisely the kind of concerns that the exposé of PRISM confirms — that the signals intel agency can spy on content coming through American Internet servers.
Forbes’ Andy Greenberg points out Alexander’s categorical denials that appear to be false testimony by yet another high-ranking Obama administration official:
In a congressional hearing in March of last year, for instance, NSA Director Keith Alexander was questioned about a Wired magazine cover story that included on-the-record interviews with multiple ex-NSA officials describing the agency’s collection of Americans’ voice and digital information. Speaking to Representative Hank Johnson, Alexander responded 14 times that the agency doesn’t collect the kind of domestic data Bamford had alleged.Here’s a sample of that questioning:Rep. Johnson: Does the NSA intercept Americans’ cell phone conversations?Director Alexander: No.
Google searches?No.Text messages?No.Amazon.com orders?No.Bank records?No.What judicial consent is required for NSA to intercept communications and information involving American citizens?Within the United States, that would be the FBI lead. If it were a foreign actor in the United States, the FBI would still have to lead. It could work that with NSA or other intelligence agencies as authorized. But to conduct that kind of collection in the United States it would have to go through a court order, and the court would have to authorize it. We’re not authorized to do it, nor do we do it.
The excerpt doesn’t include this, but Alexander categorically denied more than once in this clip that NSA even had the capability to conduct surveillance in the manner Wired reported, and that PRISM apparently confirms. Perhaps Alexander didn’t want to spill the beans in open testimony, but the proper answer would have been, “I don’t want to discuss our capabilities in open session, but I’d be glad to address your concerns in a classified briefing.” That would have raised eyebrows immediately — as it did yesterday with Eric Holder — but would have avoided perjury.
Forbes also has the video of DNI James Clapper’s suddenly-questionable testimony this year:
Sen. Wyden: Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?Director Clapper: No sir.It does not.Not wittingly. There are cases where they could inadvertantly perhaps collect, but not wittingly.
I’d like to see how the NSA squares this testimony with the exposure of PRISM. I’d guess that Senator Wyden and other members of Congress would as well.
http://hotair.com/archives/2013/06/07/video-dem-senator-basically-calls-obama-a-liar-for-claiming-that-congress-has-been-briefed-on-nsa-spying/
Video: Dem senator basically calls Obama a liar for claiming that Congress has been briefed on NSA spying
POSTED AT 4:01 PM ON JUNE 7, 2013 BY ALLAHPUNDIT
Enjoy as Jeff Merkley leaves a gaping hole in O’s “three branches of oversight” defense from earlier this afternoon. Direct quote:
“When it comes to telephone calls, every member of Congress has been briefed on this program,” Obama said. “With respect to all these programs, the relevant intelligence committees are fully briefed on these programs.”
According to Merkley, he wasn’t briefed on anything. If I understand him correctly, he’s claiming that he knew in vague terms that NSA was sweeping up lots of data but (a) he discovered the breadth of the phone-records data-mining only because he sought out details on that and (b) he had no idea whatsoever about PRISM. (He’s not a member of the Senate Intelligence Committee, though.) Why is PRISM, which seems to be far more intrusive than the phone-records program, being hidden from rank-and-file congressmen if the telephone data-mining isn’t? And why wasn’t Merkley briefed even on the phone-records harvesting? It’s hard to sell a “trust your government” argument when senators with civil-liberties concerns are being kept in the dark. Obama lied, NSA spied?
You need to watch to the end of the clip for all of the above but there’s a middle section on an unrelated topic that you can skip through. Oh, and if you feel insufficiently depressed by the last 36 hours, read this. It’ll straighten you right out.
Update: If the last link doesn’t straighten you out, this will. When Carl Levin asked the Pentagon last month for a list of Al Qaeda associates, they promised they’d provide one — with the stipulation that it’ll remain classified. As Doyle McManus notes, the public no longer has a right to know who its enemies are.



No comments:
Post a Comment