http://www.zerohedge.com/news/2013-06-08/nsas-boundless-informant-collects-3-billion-intelligence-pieces-us-computer-networks
http://www.reuters.com/article/2013/06/08/us-europe-surveillance-prism-idUSBRE95614M20130608
and...
http://theweek.com/article/index/245311/sources-nsa-sucks-in-data-from-50-companies
http://www.guardian.co.uk/world/2013/jun/08/nsa-boundless-informant-global-datamining?guni=Network%20front:network-front%20full-width-1%20bento-box:Bento%20box:Position1
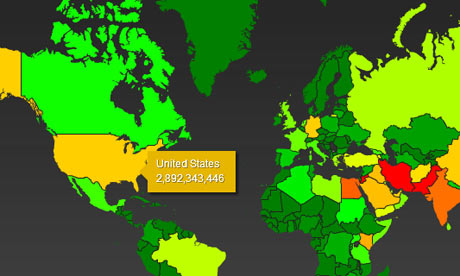

 The heat map reveals how much data is being collected from around the world. Note the '2007' date in the image relates to the document from which the interactive map derives its top secret classification, not to the map itself.
The heat map reveals how much data is being collected from around the world. Note the '2007' date in the image relates to the document from which the interactive map derives its top secret classification, not to the map itself.
http://rt.com/usa/obama-cyber-attack-list-418/
The NSA's "Boundless Informant" Collects 3 Billion Intelligence Pieces From US Computer Networks In One Month
Submitted by Tyler Durden on 06/08/2013 21:15 -0400
There's one reason why the administration, James Clapper and the NSA should just keep their mouths shut as the PRISM-gate fallout escalates: with every incremental attempt to refute some previously unknown facet of the US Big Brother state, a new piece of previously unleaked information from the same intelligence organization now scrambling for damage control, emerges and exposes the brand new narrative as yet another lie, forcing even more lies, more retribution against sources, more journalist persecution and so on.
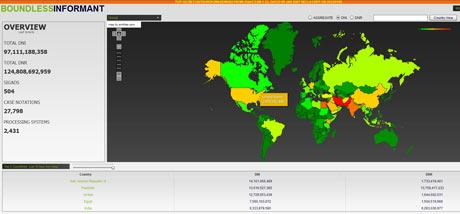
The latest piece of news once again comes from the Guardian's Glenn Greenwald who this time exposes the NSA's data mining tool "Boundless Informant" which according to leaked documents collected 97 billion pieces of intelligence from computer networks worldwide in March 2013 alone, and "3 billion pieces of intelligence from US computer networks over a 30-day period."
This is summarized in the chart below which shows that only the middle east has more active NSA-espionage than the US. Also, Obama may not want to show Xi the activity heat map for China, or else the whole "China is hacking us" script may promptly fall apart.
Using simple, non-AES 256 breaking math, 3 billion per month amounts to some 100 million intrusions into the US per day, or looked at from another perspective, just a little more than the "zero" which James Clapper vouched announced earlier today is the applicable number of US citizens falling under the NSA's espionage mandate: "Section 702 cannot be used to intentionally target any U.S. citizen, or any other U.S. person, or to intentionally target any person known to be in the United States." Oops.
But it gets worse for the NSA. As the Guardian reports, "Emmel, the NSA spokeswoman, told the Guardian: "Current technology simply does not permit us to positively identify all of the persons or locations associated with a given communication (for example, it may be possible to say with certainty that a communication traversed a particular path within the internet. It is harder to know the ultimate source or destination, or more particularly the identity of the person represented by the TO:, FROM: or CC: field of an e-mail address or the abstraction of an IP address). Thus, we apply rigorous training and technological advancements to combine both our automated and manual (human) processes to characterize communications – ensuring protection of the privacy rights of the American people. This is not just our judgment, but that of the relevant inspectors general, who have also reported this."
In other words, Americans are absolutely the target of billions of monthly intrusions, but said data "mining" is exempted because it is difficult to identify in advance if a US citizen is implicated in any metadata chain.
Only it isn't as it is the whole premise behind Boundless Informant.
An NSA factsheet about the program, acquired by the Guardian, says: "The tool allows users to select a country on a map and view the metadata volume and select details about the collections against that country."The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message.The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. One document says it is designed to give NSA officials answers to questions like, "What type of coverage do we have on country X" in "near real-time by asking the SIGINT [signals intelligence] infrastructure."Under the heading "Sample use cases", the factsheet also states the tool shows information including: "How many records (and what type) are collected against a particular country."A snapshot of the Boundless Informant data, contained in a top secret NSA "global heat map" seen by the Guardian, shows that in March 2013 the agency collected 97bn pieces of intelligence from computer networks worldwide.Iran was the country where the largest amount of intelligence was gathered, with more than 14bn reports in that period, followed by 13.5bn from Pakistan. Jordan, one of America's closest Arab allies, came third with 12.7bn, Egypt fourth with 7.6bn and India fifth with 6.3bn.
Next up: more NSA lies of course.
The disclosure of the internal Boundless Informant system comes amid a struggle between the NSA and its overseers in the Senate over whether it can track the intelligence it collects on American communications. The NSA's position is that it is not technologically feasible to do so.At a hearing of the Senate intelligence committee In March this year, Democratic senator Ron Wyden asked James Clapper, the director of national intelligence: "Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?""No sir," replied Clapper.Judith Emmel, an NSA spokeswoman, told the Guardian in a response to the latest disclosures: "NSA has consistently reported – including to Congress – that we do not have the ability to determine with certainty the identity or location of all communicants within a given communication. That remains the case."Other documents seen by the Guardian further demonstrate that the NSA does in fact break down its surveillance intercepts which could allow the agency to determine how many of them are from the US. The level of detail includes individual IP addresses.IP address is not a perfect proxy for someone's physical location but it is rather close, said Chris Soghoian, the principal technologist with the Speech Privacy and Technology Project of the American Civil Liberties Union. "If you don't take steps to hide it, the IP address provided by your internet provider will certainly tell you what country, state and, typically, city you are in," Soghoian said....At a congressional hearing in March last year, Alexander denied point-blank that the agency had the figures on how many Americans had their electronic communications collected or reviewed. Asked if he had the capability to get them, Alexander said: "No. No. We do not have the technical insights in the United States." He added that "nor do we do have the equipment in the United States to actually collect that kind of information".
Turns out they do, and that perjury in the US is now merely another facet of the "New Normal." Plus what difference does it make that yet another member of the most transparent administration perjured themselves. Then again, when the head of the Department of Justice is being investigated for lying to Congress under oath, one can only laugh.
That laughter risks becoming an imbecilic cackle when reading the following veiled threat to the Guardian from the NSA's Judith Emmel: "The continued publication of these allegations about highly classified issues, and other information taken out of context, makes it impossible to conduct a reasonable discussion on the merits of these programs."
In other words, the best discussion is one that would simply not take place as reporters should promptly stop actually reporting, and fall back to their New Normal role of being access journalists to important people (see Andrew Ross Sorkin's rise to fame on... nothing) with zero critical insight or investigative effort. Or else...
http://www.reuters.com/article/2013/06/08/us-europe-surveillance-prism-idUSBRE95614M20130608
(Reuters) - Europeans reacted angrily on Friday to revelations that U.S. authorities had tapped the servers of internet companies for personal data, saying they confirmed their worst fears about American Web giants and showed tighter regulations were needed.
The Washington Post and the Guardian aroused outrage with reports that the National Security Agency (NSA) and FBI had accessed central servers of Google, Facebook and others and gathered millions of phone users' data.
Europe, which lacks internet giants of its own, has long yearned to contain the power of the U.S. titans that dominate the Web, and privacy-focusedGermany was quick to condemn their co-operation with the U.S. security services.
"The U.S. government must provide clarity regarding these monstrous allegations of total monitoring of various telecommunications and Internet services," said Peter Schaar, German data protection and freedom of information commissioner.
"Statements from the U.S. government that the monitoring was not aimed at U.S. citizens but only against persons outside the United States do not reassure me at all."
The Post said the secret program involving the internet companies, code-named PRISM and established under President George W. Bush, had seen "exponential growth" during the past several years under Barack Obama.
Some of the companies named in the article have denied the government had "direct access" to their central servers. Nevertheless, the justice minister for the German state of Hesse, Joerg-Uwe Hahn, called for a boycott of the companies involved.
"I am amazed at the flippant way in which companies such as Google and Microsoft seem to treat their users' data," he told the Handelsblatt newspaper. "Anyone who doesn't want that to happen should switch providers."
CONCERNS RIPPLE BEYOND EUROPE
The European Union has struggled to assert its citizens' rights to privacy in the United States for almost a decade.
Transatlantic agreements on sharing the financial and travel data of European citizens have taken years to complete, and the European Union is now trying to modernize an almost 20-year-old privacy law to strengthen Europeans' rights.
International concerns also echoed beyond Europe.
In Australia, the conservative opposition said it was "very troubled" and had voiced concern to U.S. diplomats in Canberra about what it called large-scale, covert surveillance of private data belonging to foreigners.
"There is a massive global trend to cloud services," said opposition communications spokesman Malcolm Turnbull, noting that the vast majority of providers were U.S. firms.
Fears about the security of data held on U.S. servers have already been a major factor in slow European adoption of "cloud" computing services, in which computing-intensive applications are done by central providers in large server farms.
The U.S. Patriot Act, signed into law after the September 11, 2001 attacks on the country, gave U.S. intelligence agencies significant new powers of data surveillance and had been a focal point of resistance.
"You hear more concerns in Europe than in the U.S., about the Patriot Act in particular. PRISM just enhances those concerns," said Mark Watts, a partner in London law firm Bristows specializing in privacy and data compliance.
"The main players that are mentioned are much more on the consumer cloud end... but it may be that emotionally it adds to the concerns about U.S. cloud providers," said Watts, whose clients include several large U.S. internet firms.
Cloud services accounted for $16.1 billion in revenues in western Europe last year, according to IT research firm Gartner, less than half the $32.9 billion generated in north America by firms such as Amazon or Salesforce.
Europe has tried to protect its citizens by imposing restrictions on the export of data to third countries without strong data protection laws, which can include the United States - but Bristows' Watts said these were easy to get around.
European Justice Commissioner and Vice President Viviane Reding said: "This case shows that a clear legal framework for the protection of personal data is not a luxury or constraint but a fundamental right."
Reding, who has been trying to push through an update to Europe's data protection laws for 18 months, noted that EU government leaders meeting in the European Council had been able to agree the Data Retention Directive relatively quickly.
Their action on the 2006 directive, which stipulates that phone and internet companies must store records to help in fighting serious crime, showed they could act fast when limiting civil liberties.
"It is time for the Council to prove it can act with the same speed and determination on a file which strengthens such rights," she said in an emailed statement.
WHOLESALE SURVEILLANCE
Some of Europe's difficulties in combating perceived data abuses arise from the fact that many European governments look with envy at the U.S. security services' powers.
Britain is trying to strengthen its already powerful monitoring capabilities by bringing in what critics say would be the West's most far-reaching surveillance laws.
The Guardian reported on Friday that Britain's eavesdropping and security agency, GCHQ, had been secretly gathering intelligence from PRISM and had had access to the system since at least June 2010.
GCHQ said in an emailed statement to Reuters: "Our work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorized, necessary and proportionate."
Mikko Hypponen, chief research officer at Finnish software security firm F-Secure, said outrage was the appropriate response to the U.S. revelations.
"What we have in our hands now is the first concrete proof of U.S.-based high-tech companies participating with the NSA in wholesale surveillance on us, the rest of the world, the non-American, you and me," he said.
But he added there was little that individuals could do, with precious few alternatives to the popular services offered by U.S. firms Facebook, Google or Apple.
"The long term solution is that Europe should have a dot.com industry just like the United States, which would give us economic benefits but more importantly would make us independent of the wholesale surveillance of the U.S. intelligence agencies."
and...
http://theweek.com/article/index/245311/sources-nsa-sucks-in-data-from-50-companies
Analysts at the National Security Agency can now secretly access real-time user data provided by as many as 50 American companies, ranging from credit rating agencies to internet service providers, two government officials familiar with the arrangements said.
Several of the companies have provided records continuously since 2006, while others have given the agency sporadic access, these officials said. These officials disclosed the number of participating companies in order to provide context for a series of disclosures about the NSA's domestic collection policies. The officials, contacted independently, repeatedly said that "domestic collection" does not mean that the target is based in the U.S. or is a U.S. citizen; rather, it refers only to the origin of the data.
The Wall Street Journal reported today that U.S. credit card companies had also provided customer information. The officials would not disclose the names of the companies because, they said, doing so would provide U.S. enemies with a list of companies to avoid. They declined to confirm the list of participants in an internet monitoring program revealed by the Washington Post and the Guardian, but both confirmed that the program existed.
"The idea is to create a mosaic. We get a tip. We vet it. Then we mine the data for intelligence," one of the officials said.
In a statement, Director of National Intelligence James Clapper said that programs collect communications "pursuant to section 702 of the Foreign Intelligence Surveillance Act, " and "cannot be used to intentionally target any U.S. citizen, any other U.S person, or anyone within the United States."
He called the leaks "reprehensible" and said the program "is among the most important" sources of "valuable" intelligence information the government takes in.
One of the officials who spoke to me said that because data types are not standardized, the NSA needs several different collection tools, of which PRISM, disclosed today by the Guardian and the Washington Post, is one. PRISM works well because it is able to handle several different types of data streams using different basic encryption methods, the person said. It is a "front end" system, or software, that allows an NSA analyst to search through the data and pull out items of significance, which are then stored in any number of databases. PRISM works with another NSA program to encrypt and remove from the analysts' screen data that a computer or the analyst deems to be from a U.S. person who is not the subject of the investigation, the person said. A FISA order is required to continue monitoring and analyzing these datasets, although the monitoring can start before an application package is submitted to the Foreign Intelligence Surveillance Court.
From the different types of data, including their credit card purchases, the locations they sign in to the internet from, and even local police arrest logs, the NSA can track people it considers terrorism or espionage suspects in near-real time. An internet geo-location cell is on constant standby to help analysts determine where a subject logs in from. Most of the collection takes place on subjects outside the U.S, but a large chunk of the world's relevant communication passes through American companies with servers on American soil. So the NSA taps in locally to get at targets globally.
It is not clear how the NSA interfaces with the companies. It cannot use standard law enforcement transmission channels to do, since most use data protocols that are not compatible with that hardware. Several of the companies mentioned in the Post report deny granting access to the NSA, although it is possible that they are lying, or that the NSA's arrangements with the company are kept so tightly compartmentalized that very few people know about it. Those who do probably have security clearances and are bound by law not to reveal the arrangement.
This arrangement allows the U.S. companies to "stay out of the intelligence business," one of the officials said. That is, the government bears the responsibility for determining what's relevant, and the company can plausibly deny that it subjected any particular customer to unlawful government surveillance. Previously, Congressional authors of the FAA said that such a "get out of jail free" card was insisted by corporations after a wave of lawsuits revealed the extent of their cooperation with the government.
It is possible, but not likely, that the NSA clandestinely burrows into servers on American soil, without the knowledge of the company in question, although that would be illegal.
The 2008 FISA Amendments Act allow the NSA to analyze, with court orders, domestic communications of all types for counter-terrorism, counter-espionage, counter-narcotics and counter-proliferation purposes. If the agency believes that both ends of the communication, or the circle of those communicating, are wholly within the U.S., the FBI takes over. If one end of the conversation is outside the U.S., the NSA keeps control of the monitoring. An administration official said that such monitoring is subject to "extensive procedures," but as the Washington Post reported, however, it is often very difficult to segregate U.S. citizens and residents from incidental contact.
One official likened the NSA's collection authority to a van full of sealed boxes that are delivered to the agency. A court order, similar to the one revealed by the Guardian, permits the transfer of custody of the "boxes." But the NSA needs something else, a specific purpose or investigation, in order to open a particular box. The chairman of the Senate intelligence committee, Sen. Dianne Feinstein, said the standard was "a reasonable, articulatable" suspicion, but did not go into details.
Legally, the government can ask companies for some of these records under a provision of the PATRIOT Act called the "business records provision." Initially, it did so without court cognizance. Now, the FISC signs off on every request.
Armed with what amounts to a rubber stamp court order, however, the NSA can collect and store trillions of bytes of electromagnetic detritus shaken off by American citizens. In the government's eyes, the data is simply moving from one place to another. It does not become, in the government's eyes, relevant or protected in any way unless and until it is subject to analysis. Analysis requires that second order.
And the government insists that the rules allowing the NSA or the FBI to analyze anything relating to U.S. persons or corporations are strict, bright-line, and are regularly scrutinized to ensure that innocents don't get caught up in the mix. The specifics, however, remain classified, as do the oversight mechanisms in place.
The wave of disclosures about the NSA programs have significantly unsettled the intelligence community.
The documents obtained by the two newspapers are marked ORCON, or originator controlled, which generally means that the agency keeps a record of every person who accesses them online and knows exactly who might have printed out or saved or accessed a copy. The NSA in particular has a good record of protecting its documents.
The scope of the leaks suggest to one former senior intelligence official who now works for a corporation that provides data to the NSA that several people with top-level security clearances had to be involved.
The motive, I suspect, is to punch through the brittle legal and moral foundation that modern domestic surveillance is based upon. Someone, at a very high level, or several people, may have simply found that the agency's zeal to collect information blinded it to the real-world consequences of such a large and unending program. The minimization procedures might also be well below the threshold that most Americans would expect.
Clapper said in his statement that the disclosures about the program "risk important protections for the security of Americans."
http://www.guardian.co.uk/world/2013/jun/08/nsa-boundless-informant-global-datamining?guni=Network%20front:network-front%20full-width-1%20bento-box:Bento%20box:Position1
Boundless Informant: the NSA's secret tool to track global surveillance data
Revealed: The NSA's powerful tool for cataloguing data – including figures on US collection
• Boundless Informant: mission outlined in four slides
• Read the NSA's frequently asked questions document
• Boundless Informant: mission outlined in four slides
• Read the NSA's frequently asked questions document


The color scheme ranges from green (least subjected to surveillance) through yellow and orange to red (most surveillance). Note the '2007' date in the image relates to the document from which the interactive map derives its top secret classification, not to the map itself.
The National Security Agency has developed a powerful tool for recording and analysing where its intelligence comes from, raising questions about its repeated assurances to Congress that it cannot keep track of all the surveillance it performs on American communications.
The Guardian has acquired top-secret documents about the NSAdatamining tool, called Boundless Informant, that details and even maps by country the voluminous amount of information it collects from computer and telephone networks.
The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message.
The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. One document says it is designed to give NSA officials answers to questions like, "What type of coverage do we have on country X" in "near real-time by asking the SIGINT [signals intelligence] infrastructure."
An NSA factsheet about the program, acquired by the Guardian, says: "The tool allows users to select a country on a map and view the metadata volume and select details about the collections against that country."
Under the heading "Sample use cases", the factsheet also states the tool shows information including: "How many records (and what type) are collected against a particular country."
A snapshot of the Boundless Informant data, contained in a top secret NSA "global heat map" seen by the Guardian, shows that in March 2013 the agency collected 97bn pieces of intelligence from computer networks worldwide.
 The heat map reveals how much data is being collected from around the world. Note the '2007' date in the image relates to the document from which the interactive map derives its top secret classification, not to the map itself.
The heat map reveals how much data is being collected from around the world. Note the '2007' date in the image relates to the document from which the interactive map derives its top secret classification, not to the map itself.
Iran was the country where the largest amount of intelligence was gathered, with more than 14bn reports in that period, followed by 13.5bn from Pakistan. Jordan, one of America's closest Arab allies, came third with 12.7bn, Egypt fourth with 7.6bn and India fifth with 6.3bn.
The heatmap gives each nation a color code based on how extensively it is subjected to NSA surveillance. The color scheme ranges from green (least subjected to surveillance) through yellow and orange to red (most surveillance).
The disclosure of the internal Boundless Informant system comes amid a struggle between the NSA and its overseers in the Senate over whether it can track the intelligence it collects on American communications. The NSA's position is that it is not technologically feasible to do so.
At a hearing of the Senate intelligence committee In March this year, Democratic senator Ron Wyden asked James Clapper, the director of national intelligence: "Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?"
"No sir," replied Clapper.
Judith Emmel, an NSA spokeswoman, told the Guardian in a response to the latest disclosures: "NSA has consistently reported – including to Congress – that we do not have the ability to determine with certainty the identity or location of all communicants within a given communication. That remains the case."
Other documents seen by the Guardian further demonstrate that the NSA does in fact break down its surveillance intercepts which could allow the agency to determine how many of them are from the US. The level of detail includes individual IP addresses.
IP address is not a perfect proxy for someone's physical location but it is rather close, said Chris Soghoian, the principal technologist with the Speech Privacy and Technology Project of the American Civil Liberties Union. "If you don't take steps to hide it, the IP address provided by yourinternet provider will certainly tell you what country, state and, typically, city you are in," Soghoian said.
That approximation has implications for the ongoing oversight battle between the intelligence agencies and Congress.
On Friday, in his first public response to the Guardian's disclosures this week on NSA surveillance, Barack Obama said that that congressional oversight was the American peoples' best guarantee that they were not being spied on.
"These are the folks you all vote for as your representatives in Congress and they are being fully briefed on these programs," he said. Obama also insisted that any surveillance was "very narrowly circumscribed".
Senators have expressed their frustration at the NSA's refusal to supply statistics. In a letter to NSA director General Keith Alexander in October last year, senator Wyden and his Democratic colleague on the Senate intelligence committee, Mark Udall, noted that "the intelligence community has stated repeatedly that it is not possible to provide even a rough estimate of how many American communications have been collected under the Fisa Amendments Act, and has even declined to estimate the scale of this collection."
At a congressional hearing in March last year, Alexander denied point-blank that the agency had the figures on how many Americans had their electronic communications collected or reviewed. Asked if he had the capability to get them, Alexander said: "No. No. We do not have the technical insights in the United States." He added that "nor do we do have the equipment in the United States to actually collect that kind of information".
Soon after, the NSA, through the inspector general of the overall US intelligence community, told the senators that making such a determination would jeopardize US intelligence operations – and might itself violate Americans' privacy.
"All that senator Udall and I are asking for is a ballpark estimate of how many Americans have been monitored under this law, and it is disappointing that the inspectors general cannot provide it," Wyden toldWired magazine at the time.
The documents show that the team responsible for Boundless Informant assured its bosses that the tool is on track for upgrades.
The team will "accept user requests for additional functionality or enhancements," according to the FAQ acquired by the Guardian. "Users are also allowed to vote on which functionality or enhancements are most important to them (as well as add comments). The BOUNDLESSINFORMANT team will periodically review all requests and triage according to level of effort (Easy, Medium, Hard) and mission impact (High, Medium, Low)."
Emmel, the NSA spokeswoman, told the Guardian: "Current technology simply does not permit us to positively identify all of the persons or locations associated with a given communication (for example, it may be possible to say with certainty that a communication traversed a particular path within the internet. It is harder to know the ultimate source or destination, or more particularly the identity of the person represented by the TO:, FROM: or CC: field of an e-mail address or the abstraction of an IP address).
"Thus, we apply rigorous training and technological advancements to combine both our automated and manual (human) processes to characterize communications – ensuring protection of the privacy rights of the American people. This is not just our judgment, but that of the relevant inspectors general, who have also reported this."
She added: "The continued publication of these allegations about highly classified issues, and other information taken out of context, makes it impossible to conduct a reasonable discussion on the merits of these programs."
Damage Control Time: National Intelligence Releases PRISM "Facts"
Submitted by Tyler Durden on 06/08/2013 - 18:12
Confirming that the administration is in very hot water over this week's revelations of widespread domestic and global surveillance, moments ago this Saturday afternoon the head of National Intelligence James Clapperreleased "Facts on the Collection of Intelligence Pursuant to Section 702 of the Foreign Intelligence Surveillance Act" in which he says that PRISM is not an undisclosed collection or data mining program. It is an internal government computer system used to facilitate the government’s... collection of foreign intelligence information." In fact, the program is so legit, it doesn't even work to collect foreign data: "We cannot target even foreign persons overseas without a valid foreign intelligence purpose." Finally, any rumors that Google Glass will be reverting to its original codename "NSA SpyCam" are greatly exaggerated: "Service providers supply information to the Government when they are lawfully required to do so." In short - please believe him. He is from the government, he is telling the truth, and the government is here to help. As for all those Verizon (and other carrier) all too domestic phone intercepts: don't you worry about that.
Shoot The PRISM-Gate Messenger: Obama To Launch Criminal Probe Into NSA Leaks
Submitted by Tyler Durden on 06/07/2013 - 21:29
Suddenly embroiled in too many scandals to even list, and humiliated by a publicly-exposed (because everyone knew about the NSA superspy ambitions before, but with one major difference: it was a conspiracy theory.... now it is a conspiracy fact) surveillance scandal that makes Tricky Dick look like an amateur, earlier today, as expected, Obama came out and publicly declared "I am not a hacker" and mumbled something about "security", "privacy" and "inconvenience." He went on to explain how the government "welcomes the debate" of all three in the aftermath of the public disclosure that every form of electronic communication is intercepted and stored by the US government (now that said interception is no longer secret, of course) but more importantly how it is only the government, which is naturally here to help, that should be the ultimate arbiter in deciding what is best for all. Yet the PRISM-gate scandal which is sure to only get worse with time as Americans slowly realize they are living in a Orwellian police state, meant Obama would have to do more to appease a public so furious even the NYT issued a scathing editorial lamenting the obliteration of Obama's credibility. Sure enough, the president did. Reuters reports that the first course of action by the US government will be to... shoot the messenger.
'Little or no warning': Obama draws up worldwide cyber-attack target list
Published time: June 08, 2013 18:31
Edited time: June 08, 2013 19:24
Edited time: June 08, 2013 19:24
President Barack Obama ordered national security leaders to compile a list of potential overseas “adversaries” for US cyber-attacks which could be targeted with “little or no warning”, a top secret document reveals.
The 18-page, classified document, entitled Presidential Policy Directive 20, outlines plans for
Offensive Cyber Effects Operations (OCEO), cyber-attacks which would target US adversaries around the world.
“OCEO can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging,” the Washington Post cites the document as saying. “The United States government shall identify potential targets of national importance where OCEO can offer favorable balance of effectiveness and risk as compared with other instruments of national power,” it continues.
Offensive Cyber Effects Operations (OCEO), cyber-attacks which would target US adversaries around the world.
“OCEO can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging,” the Washington Post cites the document as saying. “The United States government shall identify potential targets of national importance where OCEO can offer favorable balance of effectiveness and risk as compared with other instruments of national power,” it continues.
The directive also mulls the potential use of cyber actions within the US, though any such operations must be conducted with prior authorization of the White House, unless “it qualifies as an Emergency Cyber Action.”
Under the heading "Policy Reviews and Preparation", a section marked "TS/NF" - top secret/no foreign - states: "The secretary of defense, the DNI [Director of National Intelligence], and the director of the CIA … shall prepare for approval by the president through the National Security Advisor a plan that identifies potential systems, processes and infrastructure against which the United States should establish and maintain OCEO capabilities…," the Guardian reports. The deadline for the plan is six months after the approval of the directive.
It further recognizes the potential for collateral damage in the wake of cyber operations, noting: “even subtle and clandestine operations, may generate cyber effects in locations other than the intended target, with potential unintended or collateral consequences that may effect [sic] US national interests in many locations.”
It further recognizes the potential for collateral damage in the wake of cyber operations, noting: “even subtle and clandestine operations, may generate cyber effects in locations other than the intended target, with potential unintended or collateral consequences that may effect [sic] US national interests in many locations.”
The document states that all cyber operations should conform with US and international law, noting that any operations which are "reasonably likely to result in significant consequences require specific presidential approval."
The directive, which was distributed to virtually every high-ranking member of the US Executive, was first signed by President Obama in mid-October though it was never published.
In November, a senior administration official told the Post how the directive was part and parcel of the White House effort to delineate between what constitutes an “offensive” or “defensive” action in the mercurial world of cyber-war and cyber-terrorism.
“What it does, really for the first time, is it explicitly talks about how we will use cyber-
operations,” the official said. “Network defense is what you’re doing inside your own networks. . . . Cyber-operations is stuff outside that space, and recognizing that you could be doing that for what might be called defensive purposes.”
Select statements from the memo were declassified in January, though no mention was made of US efforts to draw up a target list or bolster its offensive capability.
The directive, which was distributed to virtually every high-ranking member of the US Executive, was first signed by President Obama in mid-October though it was never published.
In November, a senior administration official told the Post how the directive was part and parcel of the White House effort to delineate between what constitutes an “offensive” or “defensive” action in the mercurial world of cyber-war and cyber-terrorism.
“What it does, really for the first time, is it explicitly talks about how we will use cyber-
operations,” the official said. “Network defense is what you’re doing inside your own networks. . . . Cyber-operations is stuff outside that space, and recognizing that you could be doing that for what might be called defensive purposes.”
Select statements from the memo were declassified in January, though no mention was made of US efforts to draw up a target list or bolster its offensive capability.
When asked about efforts to ratchet up US offensive capabilities as outlined in the directive, a senior administration official told the Guardian: "Once humans develop the capacity to build boats, we build navies. Once you build airplanes, we build air forces."
The official added: "As a citizen, you expect your government to plan for scenarios. We're very interested in having a discussion with our international partners about what the appropriate boundaries are."
Reports of the directive came as Chinese President Xi Jinping met with President Obama for an informal two-day summit in the resort city of Rancho Mirage, California on Friday.
The official added: "As a citizen, you expect your government to plan for scenarios. We're very interested in having a discussion with our international partners about what the appropriate boundaries are."
Reports of the directive came as Chinese President Xi Jinping met with President Obama for an informal two-day summit in the resort city of Rancho Mirage, California on Friday.
In a bid to rebuff media reports that China regularly targeted the US military and corporations with cyber-attacks, President Xi told reporters with Obama at his side: “China is a victim of cyber- attacks and we hope that earnest measures can be taken to resolve this matter.”
Obama opted not to publicly accuse China of being behind a raft of cyber-attacks targeting US facilities and institutions. Rather, he called for “common rules of the road,” adding that China and the US should work together for a mutually beneficial cyber-security regime.
“As China continues in its development process and more of its economy is based on research and innovation and entrepreneurship, they’re going to have similar concerns, which is why I believe we can work together on this rather than at cross-purposes,” Obama said.
Despite Obama’s reticence to challenge China, Secretary of Defense Chuck Hagel recently issued a stern warning to China over its alleged cyber-attacks against the US: “We are also clear-eyed about the challenges in cyber. The United States has expressed our concerns about the growing threat of cyber intrusions, some of which appear to be tied to the Chinese government and military.”
Hagel’s comments came in the wake of a US Defense Science Board report which claimed around 40 Pentagon weapons programs and almost 30 other defense technologies had been compromised by Chinese hackers, some purportedly tied to the military or government.
In April, Gen. Keith Alexander, who heads both the National Security Agency and the new Cyber Command, signaled that the United States would more aggressively counter cyber-attacks from abroad with offensive operations.
Alexander told Congress that of 40 new CYBERCOM teams currently being assembled, 13 were being established to counter foreign cyber-attacks. Regarding the 13 teams of programmers and computer experts, the NSA chief stressed: “this defend-the-nation team, is not a defensive team.”
“As China continues in its development process and more of its economy is based on research and innovation and entrepreneurship, they’re going to have similar concerns, which is why I believe we can work together on this rather than at cross-purposes,” Obama said.
Despite Obama’s reticence to challenge China, Secretary of Defense Chuck Hagel recently issued a stern warning to China over its alleged cyber-attacks against the US: “We are also clear-eyed about the challenges in cyber. The United States has expressed our concerns about the growing threat of cyber intrusions, some of which appear to be tied to the Chinese government and military.”
Hagel’s comments came in the wake of a US Defense Science Board report which claimed around 40 Pentagon weapons programs and almost 30 other defense technologies had been compromised by Chinese hackers, some purportedly tied to the military or government.
In April, Gen. Keith Alexander, who heads both the National Security Agency and the new Cyber Command, signaled that the United States would more aggressively counter cyber-attacks from abroad with offensive operations.
Alexander told Congress that of 40 new CYBERCOM teams currently being assembled, 13 were being established to counter foreign cyber-attacks. Regarding the 13 teams of programmers and computer experts, the NSA chief stressed: “this defend-the-nation team, is not a defensive team.”






No comments:
Post a Comment