http://www.aljazeera.com/news/europe/2014/08/russian-hackers-stole-12-billion-passwords-20148752422349560.html







Russian hackers 'stole 1.2 billion passwords' |
US security firm says Russian group stole more than a billion internet usernames and passwords over several years.
Last updated: 07 Aug 2014 07:22
|

The hackers had been collecting databases of personal information for years [Reuters]
|
| A US security firm says Russian hackers have stolen 1.2 billion usernames and passwords in a series of internet heists affecting 420,000 websites. According to Hold Security, the firm that uncovered the breach, the hackers had been collecting databases of personal information for years. Alex Holden, Chief Information Security Officer at Hold Security, said on Wednesday that in April the group began deploying a new online attack technique that quickly shot from computer system to computer system as unwitting infected users visited random websites. "Their data caches seemed to grow from April on at a rather alarming scale, getting them to what it is or what it was at the time," he said. A native of Kiev who now lives in Milwaukee, Holden has conducted research that contributed to other exposures of major hacks, including a breach at Adobe that exposed tens of millions of customer records. Tracked 'for months' He said he had been tracking the Russian criminals for seven months, but only was able to begin reviewing their massive cache of databases during the past few weeks. Holden timed his announcement to coincide with the annual Black Hat USA cybersecurity conference this week in Las Vegas, where it created quite a buzz. Brian Krebs, who investigates online cybercrime and blogs about it, said his phone and email were inundated while he was at the conference on Wednesday with people asking about Holden's announcement. "Alex isn't keen on disclosing his methods, but I have seen his research and data first hand and can say it's definitely for real," said Krebs. "Without spilling his secrets or methods, it is clear that he has a first-hand view on the day-to-day activities of some very active organised cybercrime networks and actors." Holden's discovery was revealed in the New York Times on Tuesday. The identities of the websites that were broken into were not identified by the Times, which cited nondisclosure agreements that required Hold Security to keep some information confidential. The reported break-ins are the latest incidents to raise doubts about the security measures that both big and small companies use to protect people's information online. Security experts believe hackers will continue breaking into computer networks unless companies become more vigilant. |
http://krebsonsecurity.com/2014/08/qa-on-the-reported-theft-of-1-2b-email-accounts/
Q&A on the Reported Theft of 1.2B Email Accounts
My phone and email have been flooded with questions and interview requests from various media outlets since security consultancy Hold Security dropped the news that a Russian gang has stolen more than a billion email account credentials. Rather than respond to each of these requests in turn, allow me to add a bit of perspective here in the most direct way possible: The Q&A.
Q: Who the heck is Alex Holden?
A: I’ve known Hold Security’s Founder Alex Holden for nearly seven years. Coincidentally, I initially met him in Las Vegas at the Black Hat security convention (where I am now). Alex is a talented and tireless researcher, as well as a forthright and honest guy. He is originally from Ukraine, and speaks/reads Russian and Ukrainian fluently. His research has been central toseveral of my big scoops over the past year, including the breach at Adobe that exposed tens of millions of customer records.
Q: Is this for real?
A: Alex isn’t keen on disclosing his methods, but I have seen his research and data firsthand and can say it’s definitely for real. Without spilling his secrets or methods, it is clear that he has a first-hand view on the day-to-day activities of some very active organized cybercrime networks and actors.
Q: Ok, but more than a billion credentials? That seems like a lot.
A: For those unfamiliar with the operations of large-scale organized crime syndicates, yes, it does. Unfortunately, there are more than a few successful cybercrooks who are quite good at what they do, and do it full-time. These actors — mostly spammers and malware purveyors (usually both) — focus on acquiring as many email addresses and account credentials as they can. Their favorite methods of gathering this information include SQL injection (exploiting weaknesses in Web sites that can be used to force the site to cough up user data) and abusing stolen credentials to steal even more credentials from victim organizations.
One micro example of this: Last year, I wrote about a botnet that enslaved thousands of hacked computers which disguised itself as a legitimate add-on for Mozilla Firefox and forced infected PCs to scour Web sites for SQL vulnerabilities.
Q: What would a crime network even do with a billion credentials?
A: Spam, spam and….oh, spam. Junk email is primarily sent in bulk using large botnets — collections of hacked PCs. A core component of the malware that powers these crime machines is the theft of passwords that users store on their computers and the interception of credentials submitted by victims in the process of browsing the Web. It is quite common for major spammers to rely on lists of billions of email addresses for distributing their malware and whatever junk products they are getting paid to promote.
Another major method of spamming (called “Webspam”) involves the use of stolen email account credentials — such as Gmail, Yahoo and Outlook — to send spam from victim accounts, particularly to all of the addresses in the contacts list of the compromised accounts.
Spam is such a core and fundamental component of any large-scale cybercrime operation that I spent the last four years writing an entire book about it, describing how these networks are created, the crooks that run them, and the cybercrime kingpins who make it worth their while. More information about this book and ways to pre-order it before its release in November is available here.
Q: Should I be concerned about this?
A: That depends. If you are the type of person who re-uses passwords at multiple sites — including email accounts — then the answer is yes. If you re-use your email password at another site and that other site gets hacked, there is an excellent chance that cyber crooks are plundering your inbox and using it to spam your friends and family to spread malware and to perpetuate the cybercrime food chain.
****
http://krebsonsecurity.com/2013/06/the-value-of-a-hacked-email-account/
10
JUN 13







JUN 13
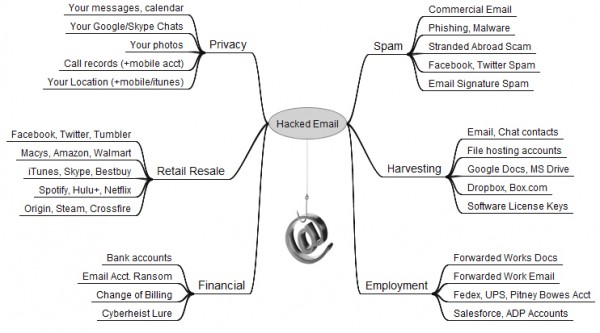
The Value of a Hacked Email Account
***
This post aims to raise awareness about the street value of a hacked email account, as well as all of the people, personal data, and resources that are put at risk when users neglect to properly safeguard their inboxes.
****
How much are these associated accounts worth? There isn’t exactly a central exchange for hacked accounts in the cybercrime underground, but recent price lists posted by several miscreants who traffic in non-financial compromised accounts offer some insights.
One prominent credential seller in the underground peddles iTunes accounts for $8, andFedex.com, Continental.com and United.com accounts for USD $6. Groupon.comaccounts fetch $5, while $4 buys hacked credentials at registrar and hosting providerGodaddy.com, as well as wireless providers Att.com, Sprint.com, Verizonwireless.com, and Tmobile.com. Active accounts at Facebook and Twitter retail for just $2.50 apiece.
As I’ve noted in previous stories, some crime shops go even lower with their prices for hacked accounts, charging between $1 to $3 for active accounts at dell.com, overstock.com,walmart.com, tesco.com, bestbuy.com and target.com, to name just a few.
Even if your email isn’t tied to online merchants, it is probably connected to other accounts you care about. Hacked email accounts are not only used to blast junk messages: They are harvested for the email addresses of your contacts, who can then be inundated with malware spam and phishing attacks. Those same contacts may even receive a message claiming you are stranded, penniless in some foreign country and asking them to wire money somewhere.
If you’ve purchased software, it’s likely that the license key to that software title is stored somewhere in your messages. Do you use online or cloud file-storage services like Dropbox,Google Drive or Microsoft Skydrive to backup or store your pictures, files and music? The key to unlocking access to those files also lies in your inbox.
If your inbox was held for ransom, would you pay to get it back? If your Webmail account gets hacked and was used as the backup account to receive password reset emails for another Webmail account, guess what? Attackers can now seize both accounts.
If you have corresponded with your financial institution via email, chances are decent that your account will eventually be used in an impersonation attempt to siphon funds from your bank account.
Until recently, some of the Web’s largest providers of online services offered little security beyond a username and password. Increasingly, however, the larger providers have moved to enabling multi-factor authentication to help users avoid account compromises. Gmail.com,Hotmail/Live.com, and Yahoo.com all now offer multi-step authentication that users can and should use to further secure their accounts. Dropbox, Facebook and Twitter also offer additional account security options beyond merely encouraging users to pick strong passwords.




No comments:
Post a Comment