Wonder why every nation gets upset about NSA spying ... and yet American citizens remain passively quiet ?
The Guardian......

Ordinary Internet users, American and non-American alike, far outnumber legally targeted foreigners in the communications intercepted by theNational Security Agency from U.S. digital networks, according to a four-month investigation by The Washington Post.
Nine of 10 account holders found in a large cache of intercepted conversations, which former NSA contractor Edward Snowden provided in full to The Post, were not the intended surveillance targets but were caught in a net the agency had cast for somebody else.
Many of them were Americans. Nearly half of the surveillance files, a strikingly high proportion, contained names, e-mail addresses or other details that the NSA marked as belonging to U.S. citizens or residents. NSA analysts masked, or “minimized,” more than 65,000 such references to protect Americans’ privacy, but The Post found nearly 900 additional e-mail addresses, unmasked in the files, that could be strongly linked to U.S. citizens or U.S.residents.
The surveillance files highlight a policy dilemma that has been aired only abstractly in public. There are discoveries of considerable intelligence value in the intercepted messages — and collateral harm to privacy on a scale that the Obama administration has not been willing to address.
So it is ironic that the NSA targets as “extremists” (the word the U.S. government uses for “probable terrorists”) anyone who uses Tor or any other privacy tool … or even searches for information on privacy tools on the Internet.
Jacob Appelbaum and other privacy experts explain at Das Erste:
- Merely searching the web for the privacy-enhancing software tools outlined in the XKeyscore rules causes the NSA to mark and track the IP address of the person doing the search. Not only are German privacy software users tracked, but the source code shows that privacy software users worldwide are tracked by the NSA.
- Among the NSA’s targets is the Tor network funded primarily by the US government to aid democracy advocates in authoritarian states.
Reddit and other popular websites have promoted privacy tools. 6% of all American adults – and 15% of males aged 18-29 – use Reddit. Are they targeted as well?
If you think we’re exaggerating the threat to privacy from the NSA, remember that the Department of Homeland Security called DHS’ own privacy office “terrorists”.
And the Department of Justice blacked out words in a document saying their disclosure would pose a “grave threat” to national security. The words? The Fourth Amendment.
This flies in the face of American values. After all:
- The Founding Fathers valued privacy over safety. Indeed, the Revolutionary War was largely started to stop the use of spying by the British. Background here. In other words, the Founding Fathers gave up their safe life with little freedom to strive for real freedom.
- The Founding Fathers – and later the Supreme Court – also said that Americans have the right toanonymous political speech
And it shows an authoritarian mindset of treating any attempt to resist their power as terrorism.
Indeed, it is like a cancer that treats any immune system response as a threat to be taken out.
Examples are – sadly – widespread in modern America:
- Reporters are treated as the enemy. And real journalism – that is, exposing government corruption – is treated as terrorism
- Whistleblowers who expose government wrongdoing are prosecuted … in order to hide government hypocrisy
- The Department of Homeland Security and other government agencies want to unmask everyone, so that we have no anonymity in our political speech
- Protesting against the government’s claimed power to indefinitely detain anyone without charge … could result in your getting detained
- Indeed, protesting anything is considered low-level terrorism
- The Associated Press reported in 2011 – in relation to the pepper spraying of peaceful UC Davis students participating in Occupy protests:
http://www.zerohedge.com/news/2014-07-03/are-you-targeted-nsa
What Your "Startlingly Intimate, Voyeristic" NSA File Looks Like
Submitted by Tyler Durden on 07/06/2014 11:54 -0400
A few days ago, we asked a simple rhetorical question: "Are you targeted by the NSA?"
The answer, sadly for those reading this, is very likely yes, as it was revealed that as part of the NSA's XKeyscore program "a computer network exploitation system, as described in an NSA presentation, devoted to gathering nearly everything a user does on the internet" all it takes for a user to be flagged by America's superspooks is to go to a website the NSA finds less than "patriotic" and that user becomes a fixture for the NSA's tracking algos.
So assuming one is being tracked by the NSA - or as it is also known for politically correct reasons "intercepted" - as a "person of interest" or worse, just what kind of data does the NSA collect? The latest report by the WaPo titled "In NSA-intercepted data, those not targeted far outnumber the foreigners who are" sheds much needed light on just how extensive the NSA's data collection effort is.
According to WaPo, the files on intercepted Americans "have a startlingly intimate, even voyeuristic quality. They tell stories of love and heartbreak,illicit sexual liaisons, mental-health crises, political and religious conversions, financial anxieties and disappointed hopes. The daily lives of more than 10,000 account holders who were not targeted are catalogued and recorded nevertheless."
The Post reviewed roughly160,000 intercepted e-mail and instant-message conversations, some of them hundreds of pages long, and 7,900 documents taken from more than 11,000 online accounts.
Remember when the NSA said they only target foreigners, and only those who are of particular actionable interest? They lied.
Nine of 10 account holders found in a large cache of intercepted conversations, which former NSA contractor Edward Snowden provided in full to The Post, were not the intended surveillance targets but were caught in a net the agency had cast for somebody else.Many of them were Americans. Nearly half of the surveillance files, a strikingly high proportion,contained names, e-mail addresses or other details that the NSA marked as belonging to U.S. citizens or residents. NSA analysts masked, or “minimized,” more than 65,000 such references to protect Americans’ privacy, but The Post found nearly 900 additional e-mail addresses, unmasked in the files, that could be strongly linked to U.S. citizens or U.S.residents.
Going back to "your" file:
Taken together, the files offer an unprecedented vantage point on the changes wrought by Section 702 of the FISA amendments, which enabled the NSA to make freer use of methods that for 30 years had required probable cause and a warrant from a judge. One program, code-named PRISM,extracts content stored in user accounts at Yahoo, Microsoft, Facebook, Google and five other leading Internet companies. Another, known inside the NSA as Upstream, intercepts data on the move as it crosses the U.S. junctions of global voice and data networks.
It gets worse, because that bed-wetting habit you kicked in the 2nd grade? The NSA knows all about it.
Among the latter are medical records sent from one family member to another, résumés from job hunters and academic transcripts of schoolchildren. In one photo, a young girl in religious dress beams at a camera outside a mosque.Scores of pictures show infants and toddlers in bathtubs, on swings, sprawled on their backs and kissed by their mothers. In some photos, men show off their physiques. In others, women model lingerie, leaning suggestively into a webcam or striking risque poses in shorts and bikini tops.
How many Americans may be tracked by the NSA at any one time? Turns out ther answer is lots:
The Obama administration declines to discuss the scale of incidental collection. The NSA, backed by Director of National Intelligence James R. Clapper Jr., has asserted that it is unable to make any estimate, even in classified form, of the number of Americans swept in. It is not obvious why the NSA could not offer at least a partial count, given that its analysts routinely pick out “U.S. persons” and mask their identities, in most cases, before distributing intelligence reports.If Snowden’s sample is representative, the population under scrutiny in the PRISM and Upstream programs is far larger than the government has suggested. In a June 26 “transparency report,” the Office of the Director of National Intelligence disclosed that 89,138 people were targets of last year’s collection under FISA Section 702. At the 9-to-1 ratio of incidental collection in Snowden’s sample, the office’s figure would correspond to nearly 900,000 accounts, targeted or not, under surveillance.
And tangentially, for those who are urging the NSA to release Lois Lerner's emails, all it would take are a few keystrokes:
“If I had wanted to pull a copy of a judge’s or a senator’s e-mail, all I had to do was enter that selector into XKEYSCORE,” one of the NSA’s main query systems, [Edward Snowden] said.
What the file would likely reveal is all the dirt the US intelligence apparatus had on said (Supreme Court) judge or senator, or IRS employee. After all, what better way to keep the system of "checks and balances" in check than to have dirt on all the key places of leverage.
The WaPo has released a sterilized example of what a "target package" looks like for any given individual.
All of the above would be stunning... if it wasn't for a culture in which FaceBook has made the exhibitionist stripping of one's privacy and disclosure of every last piece of "intimate" personal information a daily chore. It is in this world, sadly, where the most recent confirmation of just how expansive Big Brother is, will merely be granted with a yawn by the vast majority of the population.
Finally, here's a thought for the cash-strapped US government: when the Fed is no longer able to monetize the US deficit, the NSA can just hire Goldman to IPO the NSA "social network." It should raise at least a few hundred billion in cash.
The Guardian......
Germany demands answers from US after arrest of suspected double agent
Case risks further straining ties with Washington in wake of last year's revelations of NSA's monitoring of Angela Merkel's phone

Angela Merkel with Barack Obama in October: relations have been strained since Edward Snowden's revelations of snooping on Germany by the NSA. Photograph: Jim Watson/AFP/Getty Images
The German government has demanded an explanation from Washington over the US intelligence services' apparent contact with a German man arrested last week on suspicion of being a double agent, the interior minister said in a newspaper interview.
"I expect everyone to cooperate promptly to clear up these allegations – with quick and clear comments from the United States as well," Thomas de Maizière told Bild, according to excerpts from its Monday edition.
The White House and state department have so far declined to comment on the arrest of a 31-year-old employee of Germany's BND foreign intelligence agency, who has admitted passing documents to a US contact, according to intelligence and political sources.
That includes information about a parliamentary committee looking into allegations by the former US intelligence contractor Edward Snowden that Washington carried out major surveillance in Germany, including monitoring the phone of the chancellor, Angela Merkel.
The case risks further straining ties with Washington, which have been sorely tested by revelations last year of large-scale snooping on Germany by the US National Security Agency.
Surveillance is a sensitive issue in a country where the memory of the Nazis' Gestapo secret police and communist East Germany's Stasi means the right to privacy is treasured.
The German head of state, Joachim Gauck, a former Protestant pastor and rights campaigner in the former German Democratic Republic, told German TV that the NSA affair was "a vexing episode".
"If it really is the case that a service has been using an employee from our service in this way, we have to say: 'That is enough'," the president said in a television interview to be broadcast later on Sunday.
De Maizière, one of the cabinet ministers closest to Merkel, called it a "very serious case" that had to be investigated fully to "gauge the scale of the alleged spying and especially answer the question of who was involved".
The US ambassador was called in on Friday to hear Berlin's request for an explanation and the foreign minister, Frank-Walter Steinmeier, said on Sunday that it was in Washington's own interests to help with the "quickest possible clarification of the facts".
It is not clear whether Merkel discussed the matter with President Obama in their phone call on Thursday, but her spokesman, Steffen Seibert, said: "We don't take the matter of spying for foreign intelligence agencies lightly."
One member of parliament on the committee investigating the NSA affair said the man arrested had no direct contact with the committee, whose meetings were confidential, and was "not a top agent".
The suspect had offered his services to the US voluntarily, intelligence and political sources said, and had been paid about €25,000 ($34,100) for passing on 218 BND documents to his unidentified American contact.
After the Snowden revelations, Berlin demanded that Washington agree to a "no-spy agreement" but the US has been unwilling to make such a commitment. German officials also emphasise that they rely on intelligence from US agencies.
The former US secretary of state Hillary Clinton, who was in Berlin promoting her new book, said on Sunday it was "clearly a serious issue" but she hoped the affair would not "undermine the necessary cooperation which exists between us".
Black Listed News.....
ORDINARY WEB USERS FAR OUTNUMBER FOREIGN TARGETS IN CONVERSATIONS INTERCEPTED BY THE NSA
| July 5, 2014 Share It | Print This |
 | Escape Big Pharma! Kick the subs. Inexpensive Organic Herbal Pain Relief. KratomForCheap.com |
SOURCE: WASHINGTON POST
Ordinary Internet users, American and non-American alike, far outnumber legally targeted foreigners in the communications intercepted by theNational Security Agency from U.S. digital networks, according to a four-month investigation by The Washington Post.
Nine of 10 account holders found in a large cache of intercepted conversations, which former NSA contractor Edward Snowden provided in full to The Post, were not the intended surveillance targets but were caught in a net the agency had cast for somebody else.
Many of them were Americans. Nearly half of the surveillance files, a strikingly high proportion, contained names, e-mail addresses or other details that the NSA marked as belonging to U.S. citizens or residents. NSA analysts masked, or “minimized,” more than 65,000 such references to protect Americans’ privacy, but The Post found nearly 900 additional e-mail addresses, unmasked in the files, that could be strongly linked to U.S. citizens or U.S.residents.
The surveillance files highlight a policy dilemma that has been aired only abstractly in public. There are discoveries of considerable intelligence value in the intercepted messages — and collateral harm to privacy on a scale that the Obama administration has not been willing to address.
READ MORE...
and...
NSA TARGETS AS “EXTREMISTS” AMERICANS WHO SIMPLY WISH TO PROTECT THEMSELVES FROM OPPRESSION
SOURCE: WASHINGTON’S BLOG
In the wake of revelations about the extent of mass surveillance by the NSA and other agencies, people are trying to protect themselves by adopting encryption and other privacy tools.The Guardian reported in January:The gathering crisis of trust around consumer web services and the fallout from Edward Snowden’s revelations is fuelling a significant uptake in anonymity tools, new research shows, as internet users battle censorship and assert their right to privacy online.Tor was created – largely with funding from the U.S. government – in order to allow people who live in repressive authoritarian regimes to communicate anonymously on the Internet.
Globally, 56% of those surveyed by GlobalWebIndex reported that they felt the internet is eroding their personal privacy, with an estimated 415 million people or 28% of the online population using tools to disguise their identity or location.
Aggregating market research data from 170,000 internet users worldwide, GWI found that 11% of all users claim to use Tor, the most high profile for anonymising internet access.
So it is ironic that the NSA targets as “extremists” (the word the U.S. government uses for “probable terrorists”) anyone who uses Tor or any other privacy tool … or even searches for information on privacy tools on the Internet.
Jacob Appelbaum and other privacy experts explain at Das Erste:
- Merely searching the web for the privacy-enhancing software tools outlined in the XKeyscore rules causes the NSA to mark and track the IP address of the person doing the search. Not only are German privacy software users tracked, but the source code shows that privacy software users worldwide are tracked by the NSA.
- Among the NSA’s targets is the Tor network funded primarily by the US government to aid democracy advocates in authoritarian states.
***If you read Linux Journal – or even read extremely popular sites like Boing Boing – the NSA will target you.
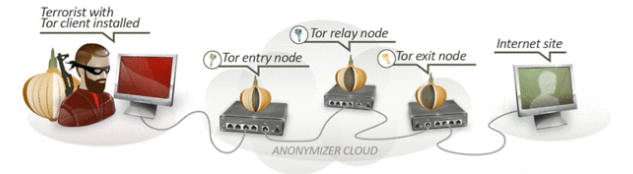
The NSA program XKeyscore is a collection and analysis tool and “a computer network exploitation system”, as described in an NSA presentation. It is one of the agency’s most ambitious programs devoted to gathering “nearly everything a user does on the internet.” The source code contains several rules that enable agents using XKeyscore to surveil privacy-conscious internet users around the world. The rules published here are specifically directed at the infrastructure and the users of the Tor Network, the Tails operating system, and other privacy-related software.
***
The former NSA director General Keith Alexander stated that all those communicating with encryption will be regarded as terror suspects and will be monitored and stored as a method of prevention, as quoted by the Frankfurter Allgemeine Zeitung in August last year. The top secret source code published here indicates that the NSA is making a concerted effort to combat any and all anonymous spaces that remain on the internet. Merely visiting privacy-related websites is enough for a user’s IP address to be logged into an NSA database.
***
The comment in the source code above describes Tails as “a comsec mechanism advocated by extremists on extremist forums”. In actuality, the software is used by journalists, human rights activists, and hundreds of thousands of ordinary people who merely wish to protect their privacy.
***
Tor Project’s Roger Dingledine stated the following: “We’ve been thinking of state surveillance for years because of our work in places where journalists are threatened. Tor’s anonymity is based on distributed trust, so observing traffic at one place in the Tor network, even a directory authority, isn’t enough to break it. Tor has gone mainstream in the past few years, and its wide diversity of users – from civic-minded individuals and ordinary consumers to activists, law enforcement, and companies – is part of its security. Just learning that somebody visited the Tor or Tails website doesn’t tell you whether that person is a journalist source, someone concerned that her Internet Service Provider will learn about her health conditions, or just someone irked that cat videos are blocked in her location. Trying to make a list of Tor’s millions of daily users certainly counts as wide scale collection. Their attack on the bridge address distribution service shows their “collect all the things” mentality – it’s worth emphasizing that we designed bridges for users in countries like China and Iran, and here we are finding out about attacks by our own country.
Reddit and other popular websites have promoted privacy tools. 6% of all American adults – and 15% of males aged 18-29 – use Reddit. Are they targeted as well?
If you think we’re exaggerating the threat to privacy from the NSA, remember that the Department of Homeland Security called DHS’ own privacy office “terrorists”.
And the Department of Justice blacked out words in a document saying their disclosure would pose a “grave threat” to national security. The words? The Fourth Amendment.
This flies in the face of American values. After all:
- The Founding Fathers valued privacy over safety. Indeed, the Revolutionary War was largely started to stop the use of spying by the British. Background here. In other words, the Founding Fathers gave up their safe life with little freedom to strive for real freedom.
- The Founding Fathers – and later the Supreme Court – also said that Americans have the right toanonymous political speech
And it shows an authoritarian mindset of treating any attempt to resist their power as terrorism.
Indeed, it is like a cancer that treats any immune system response as a threat to be taken out.
Examples are – sadly – widespread in modern America:
- Reporters are treated as the enemy. And real journalism – that is, exposing government corruption – is treated as terrorism
- Whistleblowers who expose government wrongdoing are prosecuted … in order to hide government hypocrisy
- The Department of Homeland Security and other government agencies want to unmask everyone, so that we have no anonymity in our political speech
- Protesting against the government’s claimed power to indefinitely detain anyone without charge … could result in your getting detained
- Indeed, protesting anything is considered low-level terrorism
- The Associated Press reported in 2011 – in relation to the pepper spraying of peaceful UC Davis students participating in Occupy protests:
Charles J. Kelly, a former Baltimore Police Department lieutenant who wrote the department’s use of force guidelines, said … After reviewing the video [of the pepper spraying of UC Davis students] he observed at least two cases of “active resistance”from protesters. In one instance, a woman pulls her arm back from an officer. In the second instance, a protester curls into a ball. Each of those actions could havewarranted more force, including baton strikes and pressure-point techniques.Of course, NSA apologists will pretend that targeting privacy tool users is necessary to stop the bad guys. This argument is demolished by the fact that for 5,000 years straight, mass surveillance hasalways been used by tyrants to crush dissent.
“What I’m looking at is fairly standard police procedure,” Kelly said.
- Videotaping or photographing police beating up peaceful protesters may be considered terrorism
http://www.zerohedge.com/news/2014-07-03/are-you-targeted-nsa
Are You Targeted By The NSA?
Submitted by Tyler Durden on 07/03/2014 16:01 -0400

Meet XKeyscore - "a computer network exploitation system", as described in an NSA presentation, devoted to gathering "nearly everything a user does on the internet." TheGerman site Das Erste has exposed the shocking truth about the rules used by the NSA to decide who is a "target" for surveillance. While the NSA claims to only "target" a small fraction of internet users, the perhaps unsurprising truth is very different. As Boing Boing concludes, one expert suggested that the NSA's intention here was to separate the sheep from the goats -- to split the entire population of the Internet into "people who have the technical know-how to be private" and "people who don't" and then capture all the communications from the first group.
The NSA program XKeyscore is a collection and analysis tool and "a computer network exploitation system", as described in an NSA presentation. It is one of the agency’s most ambitious programs devoted to gathering "nearly everything a user does on the internet." The source code contains several rules that enable agents using XKeyscore to surveil privacy-conscious internet users around the world. The rules published here are specifically directed at the infrastructure and the users of the Tor Network, the Tails operating system, and other privacy-related software.
In a shocking story on the German site Tagesschau (Google translate), Lena Kampf, Jacob Appelbaum and John Goetz report on the rules used by the NSA to decide who is a "target" for surveillance.

Since the start of the Snowden story in 2013, the NSA has stressed that while it may intercept nearly every Internet user's communications, it only "targets" a small fraction of those, whose traffic patterns reveal some basis for suspicion. Targets of NSA surveillance don't have their data flushed from the NSA's databases on a rolling 48-hour or 30-day basis, but are instead retained indefinitely.
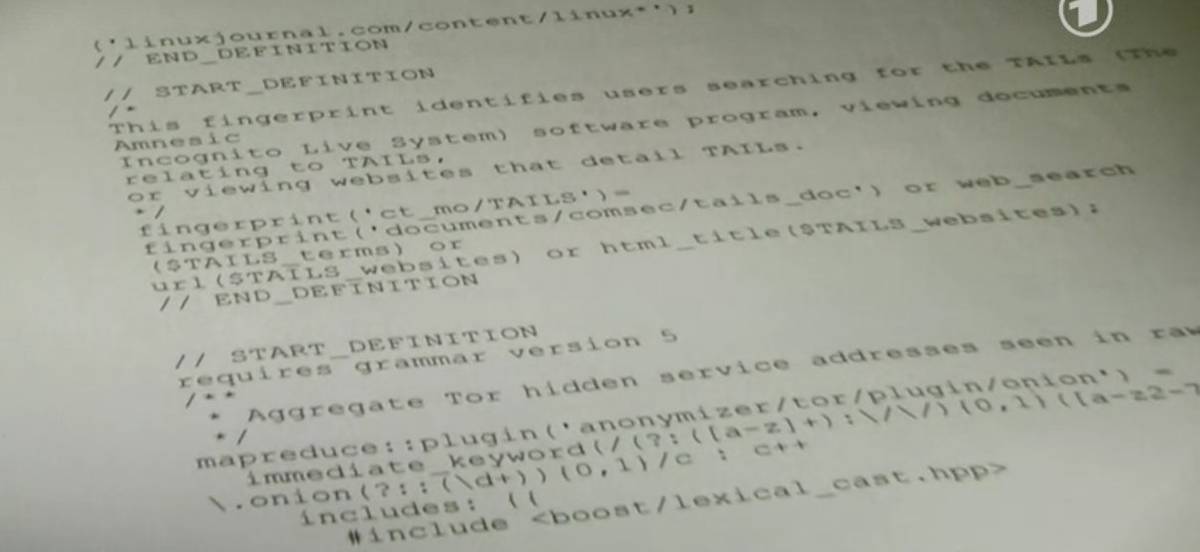
The authors of the Tagesschau story have seen the "deep packet inspection" rules used to determine who is considered to be a legitimate target for deep surveillance, and the results are bizarre.

According to the story, the NSA targets anyone who searches for online articles about Tails -- like this one that we published in April, or this article for teens that I wrote in May -- or Tor (The Onion Router, which we've been posted about since 2004). Anyone who is determined to be using Tor is also targeted for long-term surveillance and retention.
Tor and Tails have been part of the mainstream discussion of online security, surveillance and privacy for years. It's nothing short of bizarre to place people under suspicion for searching for these terms.
More importantly, this shows that the NSA uses "targeted surveillance" in a way that beggars common sense. It's a dead certainty that people who heard the NSA's reassurances about "targeting" its surveillance on people who were doing something suspicious didn't understand that the NSA meant people who'd looked up technical details about systems that are routinely discussed on the front page of every newspaper in the world.

But it's not the first time the NSA has deployed specialized, highly counterintuitive wordsmithing to play games with the public, the law and its oversight. From James Clapper's insistence that he didn't lie to Congress about spying on Americans because he was only intercepting all their data, but not looking at it all; to the internal wordgames on evidence in the original Prism leak in which the NSA claimed to have "direct access" to servers from Google, Yahoo, Microsoft, Apple, etc, even though this "direct access" was a process by which the FBI would use secret warrants to request information from Internet giants without revealing that the data was destined for the NSA.
I have known that this story was coming for some time now, having learned about its broad contours under embargo from a trusted source. Since then, I've discussed it in confidence with some of the technical experts who have worked on the full set of Snowden docs, and they were as shocked as I was.
One expert suggested that the NSA's intention here was to separate the sheep from the goats -- to split the entire population of the Internet into "people who have the technical know-how to be private" and "people who don't" and then capture all the communications from the first group.

Another expert said that s/he believed that this leak may come from a second source, not Edward Snowden, as s/he had not seen this in the original Snowden docs; and had seen other revelations that also appeared independent of the Snowden materials. If that's true, it's big news, as Snowden was the first person to ever leak docs from the NSA. The existence of a potential second source means that Snowden may have inspired some of his former colleagues to take a long, hard look at the agency's cavalier attitude to the law and decency.
* * *
And just this week it was all found perfectly legal... But it appears the US continues to make friends wherever it goes...
The German attorney Thomas Stadler, who specializes in IT law, commented: "The fact that a German citizen is specifically traced by the NSA, in my opinion, justifies the reasonable suspicion of the NSA carrying out secret service activities in Germany.For this reason, theGerman Federal Public Prosecutor should look into this matter and initiate preliminary proceedings."
So now you know - you are all being watched...
VISITING WEBSITES ABOUT PRIVACY GETS YOU PUT IN AN NSA DATABASE OF “EXTREMISTS”
Merely expressing an interest in anonymity makes you a target
Searching for online articles about privacy is enough to get someone put in an NSA database of “extremists,” according to new revelations published today.
In an article for German news outlet Tagesschau (translation here), Lena Kampf, Jacob Appelbaum and John Goetz reveal how the NSA’s “deep packet inspection” rules, which it uses to determine who to target for deep surveillance, include looking for web users who search for articles about Tor and Tails, an anonymous browser and a privacy-friendly operating system.
Those whose Internet traffic patterns suggest merely an interest in Tor or Tails are immediately put on a list of “extremists,” as is anyone who actually uses the Tor network.
“Tor and Tails have been part of the mainstream discussion of online security, surveillance and privacy for years. It’s nothing short of bizarre to place people under suspicion for searching for these terms,” writes Boing Boing’s Cory Doctorow, adding that the NSA’s goal is, “to split the entire population of the Internet into “people who have the technical know-how to be private” and “people who don’t” and then capture all the communications from the first group.”
The revelation once again highlights the fact that the NSA’s data dragnet has little to do with catching terrorists and everything to do with targeting anyone who values their right to privacy. The mass collection of such information only serves to make it easier for actual bad guys to evade detection since the federal agency is building such vast and unwieldy databases.
Earlier this week, journalist Glenn Greenwald announced that he was set to release new information based on leaked documents obtained by whistleblower Edward Snowden which would reveal which individuals and institutions were the targets of NSA spying.
However, at the last minute Greenwald said the story would be postponed as a result of the U.S. government, “suddenly began making new last-minute claims which we intend to investigate before publishing.”









No comments:
Post a Comment