http://www.aljazeera.com/news/americas/2014/04/canadian-arrested-heartbleed-hacking-201441714953794271.htmlCanadian arrested for Heartbleed hacking |
Man arrested in first case linked to internet code bug which allows hackers to bypass encryption of private details.
Last updated: 17 Apr 2014 01:59
|

The Canadian government shut federal websites to guard against hackers. [Al Jazeera]
|
| A 19-year-old Canadian has become the first person arrested for theft of information related to the Heartbleed bug, a defect that allows hackers to bypass internet encryption code. Federal police in Canada said on Wednesday they had arrested and charged Stephen Arthuro Solis-Reyes over the theft of 900 Canadian taxpayers' data, which was made vulnerable by the "Heartbleed" bug. Solis-Reyes was arrested at his London, Ontario home on Tuesday without incident. He is scheduled to appear in court on Thursday to face charges of mischief and unauthorised use of a computer to steal data from the Canada Revenue Agency's website. "It is believed that Solis-Reyes was able to extract private information held by the CRA by exploiting the security vulnerability known as the Heartbleed bug," police said in a statement. The suspect was tracked down within four days after the CRA reported a serious security breach. Police said computer equipment was seized at the suspect's home, and that the investigation is still ongoing. The Canada Revenue Agency said 900 social insurance numbers - personal nine-digit codes required for working or accessing government benefits in Canada - had been stolen last week by "someone exploiting the Heartbleed vulnerability." Its website was shut for several days over concerns about the Heartbleed bug. The recently-discovered flaw in online-data scrambling software OpenSSL allows hackers to eavesdrop on online communications, steal data, impersonate websites and unlock encrypted data. OpenSSL is commonly used to protect passwords, credit card numbers and other data sent via the internet. More than half of websites use the software, but not all versions have the same vulnerability, according to heartbleed.com. |
Info Wars ....
Obamacare site vulnerable to ‘Heartbleed’ bug
People who have accounts on the enrollment website for President Barack Obama’s signature health care law are being told to change their passwords following an administration-wide review of the government’s vulnerability to the confounding Heartbleed Internet security flaw.
Senior administration officials said there is no indication that the HealthCare.gov site has been compromised and the action is being taken out of an abundance of caution. The government’s Heartbleed review is ongoing, the officials said, and users of other websites may also be told to change their passwords in the coming days, including those with accounts on the popular WhiteHouse.gov petitions page.
The Heartbleed programming flaw has caused major security concerns across the Internet and affected a widely used encryption technology that was designed to protect online accounts. Major Internet services have been working to insulate themselves against the problem and are also recommending that users change their website passwords.
Krebs On Security......
Heartbleed Bug: What Can You Do?
In the wake of widespread media coverage of the Internet security debacle known as the Heartbleed bug, many readers are understandably anxious to know what they can do to protect themselves. Here’s a short primer.
The Heartbleed bug concerns a security vulnerability in a component of recent versions ofOpenSSL, a technology that a huge chunk of the Internet’s Web sites rely upon to secure the traffic, passwords and other sensitive information transmitted to and from users and visitors.
Around the same time that this severe flaw became public knowledge, a tool was released online that allowed anyone on the Internet to force Web site servers that were running vulnerable versions of OpenSSL to dump the most recent chunk of data processed by those servers.
That chunk of data might include usernames and passwords, re-usable browser cookies, or even the site administrator’s credentials. While the exploit only allows for small chunks of data to be dumped each time it is run, there is nothing to prevent attackers from replaying the attack over and over, all the while recording fresh data flowing through vulnerable servers. Indeed, I have seen firsthand data showing that some attackers have done just that; for example, compiling huge lists of credentials stolen from users logging in at various sites that remained vulnerable to this bug.
For this reason, I believe it is a good idea for Internet users to consider changing passwords at least at sites that they visited since this bug became public (Monday morning). But it’s important that readers first make an effort to determine that the site in question is not vulnerable to this bug before changing their passwords. Here are some resources that can tell you if a site is vulnerable:
As I told The New York Times yesterday, it is likely that many online companies will be prompting or forcing users to change their passwords in the days and weeks ahead, but then again they may not (e.g., I’m not aware of messaging from Yahoo to its customer base about their extended exposure to this throughout most of the day on Monday). But if you’re concerned about your exposure to this bug, checking the site and then changing your password is something you can do now (keeping in mind that you may be asked to change it again soon).
It is entirely possible that we may see a second wave of attacks against this bug, as it appears also to be present in a great deal of Internet hardware and third-party security products, such as specific commercial firewall and virtual private network (VPN) tools. The vast majority of non-Web server stuff affected by this bug will be business-oriented devices (and not consumer-grade products such as routers, e.g.). The SANS Internet Storm Center is maintaining a list of commercial software and hardware devices that either have patches available for this bug or that will need them.
For those in search of more technical writeups/analyses of the Hearbleed bug, see this Vimeo video and this blog post (hat tip once again to Sandro Süffert).
Finally, given the growing public awareness of this bug, it’s probable that phishers and other scam artists will take full advantage of the situation. Avoid responding to emailed invitations to reset your password; rather, visit the site manually, either using a trusted bookmark or searching for the site in question.
Cybercrime updates.......
17
APR 14
3 Million Customer Credit, Debit Cards Stolen in Michaels, Aaron Brothers Breaches
Nationwide arts and crafts chain Michaels Stores Inc. said today that two separate eight-month-long security breaches at its stores last year may have exposed as many as 3 million customer credit and debit cards.
 The disclosure, made jointly in a press release posted online and in a statement on the company’s Web site, offers the first real details about the breach since the incident was first disclosed by KrebsOnSecurity on January 25, 2014.
The disclosure, made jointly in a press release posted online and in a statement on the company’s Web site, offers the first real details about the breach since the incident was first disclosed by KrebsOnSecurity on January 25, 2014.
The statements by Irving, Texas-based Michaels suggest that the two independent security firms it hired to investigate the break-ins initially found nothing.
“After weeks of analysis, the Company discovered evidence confirming that systems of Michaels stores in the United States and its subsidiary, Aaron Brothers, were attacked by criminals using highly sophisticated malware that had not been encountered previously by either of the security firms,” the statement reads.
The Michaels breach first came to light just weeks after retail giant Target Corp. said thatcyber thieves planted malware on cash registers at its stores across the nation, stealing more than 40 million credit and debit card numbers between Nov. 27 and Dec. 15, 2013. That malware was designed to siphon card data when customers swiped their cards at the cash register.
According to Michaels, the affected systems contained certain payment card information, such as payment card number and expiration date, about both Michaels and Aaron Brothers customers. The company says there is no evidence that other customer personal information, such as name, address or debit card PIN, was at risk in connection with this issue.
The company’s statement says the attack on Michaels’ targeted “a limited portion of the point-of-sale systems at a varying number of stores between May 8, 2013 and January 27, 2014.”
“Only a small percentage of payment cards used in the affected stores during the times of exposure were impacted by this issue,” the statement continues. “The analysis conducted by the security firms and the Company shows that approximately 2.6 million cards may have been impacted, which represents about 7% of payment cards used at Michaels stores in the U.S. during the relevant time period. The locations and potential dates of exposure for each affected Michaels store are listed on www.michaels.com.”
Regarding Aaron Brothers, Michaels Stores said it has confirmed that between June 26, 2013 and February 27, 2014, 54 Aaron Brothers stores were affected by this malware, noting that the locations for each affected Aaron Brothers store are listed on www.aaronbrothers.com.
“The Company estimates that approximately 400,000 cards were potentially impacted during this period. The Company has received a limited number of reports from the payment card brands and banks of fraudulent use of payment cards potentially connected to Michaels or Aaron Brothers.” Continue reading →
15
APR 14
Hardware Giant LaCie Acknowledges Year-Long Credit Card Breach
Computer hard drive maker LaCie has acknowledged that a hacker break-in at its online store exposed credit card numbers and contact information on customers for the better part of the past year. The disclosure comes almost a month after the breach was first disclosed by KrebsOnSecurity.
On Mar. 17, 2014, this blog published evidence showing that the Web storefront for French hardware giant LaCie (now owned by Seagate) had been compromised by a group of hackers that broke into dozens of online stores using security vulnerabilities in Adobe’s ColdFusionsoftware. In response, Seagate said it had engaged third-party security firms and that its investigation was ongoing, but that it had found no indication that any customer data was compromised.
In a statement sent to this reporter on Monday, however, Seagate allowed that its investigation had indeed uncovered a serious breach. Seagate spokesman Clive J. Over said the breach may have exposed credit card transactions and customer information for nearly a year beginning March 27, 2013. From his email:
“To follow up on my last e-mail to you, I can confirm that we did find indications that an unauthorized person used the malware you referenced to gain access to information from customer transactions made through LaCie’s website.”“The information that may have been accessed by the unauthorized person includes name, address, email address, payment card number and card expiration date for transactions made between March 27, 2013 and March 10, 2014. We engaged a leading forensic investigation firm, who conducted a thorough investigation into this matter. As a precaution, we have temporarily disabled the e-commerce portion of the LaCie website while we transition to a provider that specializes in secure payment processing services. We will resume accepting online orders once we have completed the transition.”Security and data privacy are extremely important to LaCie, and we deeply regret that this happened. We are in the process of implementing additional security measures which will help to further secure our website. Additionally, we sent notifications to the individuals who may have been affected in order to inform them of what has transpired and that we are working closely and cooperatively with the credit card companies and federal authorities in their ongoing investigation.
It is unclear how many customer records and credit cards may have been accessed during the time that the site was compromised; Over said in his email that the company did not have any additional information to share at this time. Continue reading →
Fake Tax Return filing fraud..........
14
APR 14







APR 14
Crimeware Helps File Fraudulent Tax Returns
Many companies believe that if they protect their intellectual property and customers’ information, they’ve done a decent job of safeguarding their crown jewels from attackers. But in an increasingly common scheme, cybercriminals are targeting the Human Resources departments at compromised organizations and rapidly filing fraudulent federal tax returns on all employees.
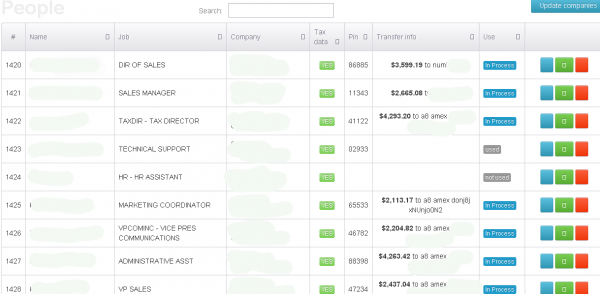
Last month, KrebsOnSecurity encountered a Web-based control panel that an organized criminal gang has been using to track bogus tax returns filed on behalf of employees at hacked companies whose HR departments had been relieved of W2 forms for all employees.

An obfuscated look at the he control panel for a tax fraud operation involving more than a half dozen victim organizations.
According to the control panel seen by this reporter, the scammers in charge of this scheme have hacked more than a half-dozen U.S. companies, filing fake tax returns on nearly every employee. At last count, this particular scam appears to stretch back to the beginning of this year’s tax filing season, and includes fraudulent returns filed on behalf of thousands of people — totaling more than $1 million in bogus returns.
The control panel includes a menu listing every employee’s W2 form, including all data needed to successfully file a return, such as the employee’s Social Security number, address, wages and employer identification number. Each fake return was apparently filed using the e-filing service provided by H&R Block, a major tax preparation and filing company. H&R Block did not return calls seeking comment for this story.

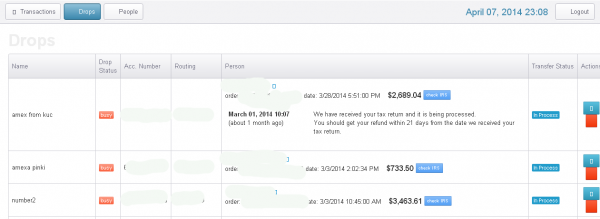
The “drops” page of this tax fraud operation lists the nicknames of the co-conspirators who agreed to “cash out” funds on the prepaid cards generated by the bogus returns — minus a small commission.
Fraudulent returns listed in the miscreants’ control panel that were successfully filed produced a specific five-digit tax filing Personal Identification Number (PIN) apparently generated by H&R Block’s online filing system. An examination of the panel suggests that successfully-filed returns are routed to prepaid American Express cards that are requested to be sent to addresses in the United States corresponding to specific “drops,” or co-conspirators in the scheme who have agreed to receive the prepaid cards and “cash out” the balance — minus their fee for processing the bogus returns.
Alex Holden, chief information security officer at Hold Security, said although tax fraud is nothing new, automating the exploitation of human resource systems for mass tax fraud is an innovation.
“The depth of this specific operation permits them to act as a malicious middle-man and tax preparation company to be an unwitting ‘underwriter’ of this crime,” Holden said. “And the victims maybe exploited not only for 2013 tax year but also down the road, and perhaps subject of higher scrutiny by IRS — not to mention potential financial losses. Companies should look at their human resource infrastructure to ensure that payroll, taxes, financial, medical, and other benefits are afforded the same level of protection as their other mission-critical assets.”
ULTIPRO USERS TARGETED
I spoke at length with Doug, a 45-year-old tax fraud victim at a company that was listed in the attacker’s control panel. Doug agreed to talk about his experience if I omitted his last name and his employer’s name from this story. Doug confirmed that the information in the attacker’s tax fraud panel was his and mostly correct, but he said he didn’t recognize the Gmail address used to fraudulently submit his taxes at H&R Block.
Doug said his employer recently sent out a company-wide email stating there had been a security breach at a cloud provider that was subcontracted to handle the company’s employee benefits and payroll systems.
“Our company sent out a blanket email saying there had been a security breach that included employee names, addresses, Social Security numbers, and other information, and that they were going to pay for a free year’s worth of credit monitoring,” Doug said.
Almost a week after that notification, the company sent out a second notice stating that the breach extended to the personal information of all spouses and children of its employees.
“We were later notified that the breach was much deeper than originally suspected, which included all of our beneficiaries, their personal information, my life insurance policy, 401-K stuff, and our taxes,” Doug said. “My sister-in-law is an accountant, so I raced to her and asked her to help us file our taxes immediately. She pushed them through quickly but the IRS came back and said someone had already filed our taxes a few days before us.”
Doug has since spent many hours filling out countless forms with a variety of organizations, including the Federal Trade Commission, the FBI, the local police department, and of course the Internal Revenue Service.
Doug’s company and another victim at a separate company whose employees were all listed as recent tax fraud victims in the attacker’s online control panel both said their employers’ third-party cloud provider of payroll services was Weston, Fla.-based Ultimate Software. In each case, the attackers appear to have stolen the credentials of the victim organization’s human resources manager, credentials that were used to manage employee payroll and benefits atUltipro, an online HR and payroll solutions provider.
Jody Kaminsky, senior vice president of marketing at Ultimate Software, said the company has no indication of a compromise of Ultimate’s security. Instead, she said Doug’s employer appears to have had its credentials stolen and abused by this fraud operation.
“Although we are aware that several customers’ employees were victims of tax fraud, we have no reason to believe this unauthorized access was the result of a compromise of our own security,” Kaminsky said. “Rather, our investigation suggests this is the result of stolen login information on the end-user level and not our application.”
Kaminsky continued:
“Unfortunately incidents of tax fraud this tax season across the U.S. are increasing and do not appear to be limited to just our customers or any one company (as I’m sure you’re well aware due to your close coverage of this issue). Over the past several weeks, we have communicated multiple times with our customers about recent threats of tax fraud and identity theft schemes.”“We believe through schemes such as phishing or malware on end-user computers, criminals are attempting to obtain system login information and use those logins to access employee data for tax fraud purposes. We take identity theft schemes extremely seriously. As tax season progresses, we have been encouraging our customers to take steps to protect their systems such as enforcing frequent password resets and ensuring employee computers’ are up-to-date on anti-malware protection.”
PROTECT YOURSELF FROM TAX FRAUD
According to a 2013 report from the Treasury Inspector General’s office, the U.S. Internal Revenue Service (IRS) issued nearly $4 billion in bogus tax refunds in 2012. The money largely was sent to people who stole Social Security numbers and other information on U.S. citizens, and then filed fraudulent tax returns on those individuals claiming a large refund but at a different address.
It’s important to note that fraudsters engaged in this type of crime are in no way singling out H&R Block or Ultipro. Cybercrooks in charge of large collections of hacked computers can just as easily siphon usernames and passwords — as well as incomplete returns — from taxpayers who are preparing returns via other online filing services, including TurboTax andTaxSlayer.
If you become the victim of identity theft outside of the tax system or believe you may be at risk due to a lost/stolen purse or wallet, questionable credit card activity or credit report, etc., you are encouraged to contact the IRS at the Identity Protection Specialized Unit, toll-free at 1-800-908-4490 so that the IRS can take steps to further secure your account.
That process is likely to involve the use of taxpayer-specific PINs for people that have had issues with identity theft. If approved, the PIN is required on any tax return filed for that consumer before a return can be accepted. To start the process of applying for a tax return PIN from the IRS, check out the steps at this link. You will almost certainly need to file an IRS form 14039 (PDF), and provide scanned or photocopied records, such a drivers license or passport.
The most frightening aspect of this tax crimeware panel is that its designers appear to have licensed it for resale. It’s not clear how much this particular automated fraud machine costs, but sources in the financial industry tell this reporter that this same Web interface has been implicated in multiple tax return scams targeting dozens of companies in this year’s tax-filing season.






No comments:
Post a Comment