Report: U.S. Electric Grid ‘Inherently Vulnerable’ to Sabotage
Multiple unreported incidents raise security concerns
BY:
Electric grid compounds across the country have faced an uptick in unauthorized intrusions by unknown individuals, causing concern that the U.S. grid is “inherently vulnerable” to widespread sabotage, according to a recent oversight report issued by New Jersey’s Regional Operations Intelligence Center (ROIC), which monitors the threat level.
Following at least eight “reports of intrusions at electrical grid facilities in New Jersey” from October 2013 until January 2014, the ROIC’s Intelligence & Analysis Threat Unit issued a report warning that the U.S. electrical grid is “inherently vulnerable” to attacks that could wipe out power across large swaths of the country.
The ROIC report, released in late February, is marked as “unclassified” but designated “for official use only.” New Jersey State Police Spokesman Trooper Jeff Flynn confirmed that a report of this nature had been commissioned by ROIC when contacted by the Washington Free Beacon.
The multiple incidents of “sabotage” and crime outlined in the report “highlight the grid’s vulnerabilities to potential threats,” according to a copy of the report obtained by the Free Beacon.
U.S. officials and experts have increasingly warned over the years that the electrical grid could be a prime target for terrorists or others seeking to damage the country’s infrastructure and disrupt daily life.
The concern is that many of the incidents outlined in the ROIC report could be a sign that preparations are under away for a larger, coordinated attack on the grid.
Highly sensitive areas of the electrical grid were found to be lightly monitored, leaving them vulnerable to attack, according to the report.
“The electrical grid—a network of power generating plants, transmission lines, substations, and distribution lines—is inherently vulnerable,” the report said.
“Transmission substations are critical links in the electrical grid, making it possible for electricity to move long distances and serving as hubs for intersecting power lines,” according to the report. “Many of the grid’s important components sit out in the open, often in remote locations, protected by little more than cameras and chain-link fences.”
While the incidents are greatly concerning to security officials—and remain mostly unsolved—the ROIC “currently does not have enough information to classify the New Jersey incidents listed [in the report] as indicative of pre-operational activity or connect them to a pattern,” according to the report, which does not discount this possibility.
However, the incidents of grid tampering are not isolated to New Jersey.
An unidentified individual in Tucson, Ariz., in January, “removed multiple bolts from an electric tower’s support structure, increasing the potential for collapse and electrical service interruption.”
Authorities suspect that the goal was “sabotage rather than vandalism” due to the “deliberate manner of the bolt removal, including probable acquisition of the requisite tools,” the report said.
In April 2013, “unknown subject(s) fired multiple shots at an electrical transmission substation” in San Jose, Calif., “damaging several transformers,” the report notes.
Surveillance video of the incident shows sparks flying across the compound as bullets strike the substation.
“Authorities subsequently discovered intentionally cut fiber optic cables in a manhole,” according to the report. “No motive or suspects have been identified.”
Sabotage has also been reported in Jacksonville, Ark., where in August 2013, “an identified suspect … removed bolts from the base of a high-voltage transmission line tower and tried to bring down the 100-foot tower with a moving train,” according to the report
One month later, “the subject reportedly set a fire at a substation control house.”
In October of that year, “the subject cut into two electrical poles and used a tractor to pull them down, cutting power to thousands of customers,” according to the report.
While the incidents in San Jose received widespread media attention, several of the others did not.
New Jersey has experienced eight separate incidents of a similar nature since last year.
On Jan. 26, for instance, “employees found a hole, approximately three-foot high by two-foot wide, in the perimeter fence of an electric switching and substation in East Rutherford,” according to the report.
Several days before that incident, on Jan. 22, “an identified subject entered a Burlington generating station using false identification,” according to the report. “The subject claimed he had a gun (none found) and a bomb (package cleared).”
Other incidents include break-ins at certain electrical stations and the theft of various on-site materials.
The ROIC concluded that while “the incidents more likely involve vandalism and theft, rather than sabotage,” any type of “intrusion or damage to substations is a critical concern to the power supply and public safety.”
Counterterrorism expert Patrick Poole warned that these attacks could be a “test-run” for a larger act of sabotage.
“While some of these incidents involving substations can be attributed to metal scavenging, it’s planned attacks, much like the one in San Jose, that have officials worried the most and raises a number of questions,” Poole told the Free Beacon. “Why was this substation targeted? What were they trying to accomplish with this attack? Was this a test-run for something larger?”
“What the New Jersey ROIC report shows is that this fits into a larger pattern of incidents, which should be keeping someone at Homeland Security up at night,” Poole said. “The other big question is how many more of these incidents are going unreported?”
The ROIC report outlines several types of suspicious behavior that authorities should be on the lookout for.
These include the “photographing objects or facilities that would not normally be photographed,” instances of individuals “loitering in sensitive areas,” and other types of atypical behavior such as “unfamiliar or out of place persons posing as panhandlers, protesters, vendors, [or] news agents.”
Flynn told the Free Beacon that ROIC aims to analyze and codify various grid incidents across the country in order to “learn from those incidents and apply them to situations here in New Jersey.”
The goal is to reach “potential conclusions to solve potential problems we have in state,” Flynn said in response to questions about the report.
Hacks of note.......
Experian Lapse Allowed ID Theft Service Access to 200 Million Consumer Records
In October 2013, KrebsOnSecurity published an exclusive story detailing how a Vietnamese man running an online identity theft service bought personal and financial records on Americans directly from a company owned by Experian, one of the three major U.S. credit bureaus. Today’s story looks deeper at the damage wrought in this colossal misstep by one of the nation’s largest data brokers.

Vietnamese national Hieu Minh Ngo pleaded guilty last week to running the ID theft service Superget.info.
Last week, Hieu Minh Ngo, a 24-year-old Vietnamese national, pleaded guilty to running an identity theft service out of his home in Vietnam. Ngo was arrested last year in Guam by U.S. Secret Service agents after he was lured into visiting the U.S. territory to consummate a business deal with a man he believed could deliver huge volumes of consumers’ personal and financial data for resale.
But according to prosecutors, Ngo had already struck deals with one of the world’s biggest data brokers: Experian. Court records just released last week show that Ngo tricked an Experian subsidiary into giving him direct access to personal and financial data on more than 200 million Americans.
HIEU KNOWS YOUR SECRETS?
As I reported last year, the data was not obtained directly from Experian, but rather via Columbus, Ohio-based US Info Search. US Info Search had a contractual agreement with a California company named Court Ventures, whereby customers of Court Ventures had access to the US Info Search data as well as Court Ventures’ data, and vice versa.
Posing as a private investigator operating out of Singapore, Ngo contracted with Court Ventures, paying for his access to consumer records via regular cash wire transfers from a bank in Singapore. Through that contract, Ngo was able to make available to his clients access to the US Info Search database containing Social Security, date of birth and other records on more than 200 million Americans.
Experian came into the picture in March 2012, when it purchased Court Ventures (along with all of its customers — including Mr. Ngo). For almost ten months after Experian completed that acquisition, Ngo continued siphoning consumer data and making his wire transfers.
Ngo’s ID theft business attracted more than 1,300 customers who paid at least $1.9 million between 2007 and Feb. 2013
Until last week, the government had shared few details about the scope and the size of the data breach, such as how many Americans may have been targeted by thieves using Ngo’s identity theft service. According to a transcript of Ngo’s guilty plea proceedings obtained by KrebsOnSecurity, Ngo’s ID theft business attracted more than 1,300 customers who paid at least $1.9 million between 2007 and Feb. 2013 to look up Social Security numbers, dates of birth, addresses, previous addresses, phone numbers, email addresses and other sensitive data.
The government alleges that the service’s customers used the information for a variety of fraud schemes, including filing fraudulent tax returns on Americans, and opening new lines of credit and racking up huge bills in the names of unsuspecting victims. The transcript shows government investigators found that over an 18-month period ending Feb. 2013, Ngo’s customers made approximately 3.1 million queries on Americans.
Thieves Jam Up Smucker’s, Card Processor
Jam and jelly maker Smucker’s last week shuttered its online store, notifying visitors that the site was being retooled because of a security breach that jeopardized customers’ credit card data. Closer examination of the attack suggests that the company was but one of several dozen firms — including at least one credit card processor — hacked last year by the same criminal gang that infiltrated some of the world’s biggest data brokers.
As Smucker’s referenced in its FAQ about the breach, the malware that hit this company’s site behaves much like a banking Trojan does on PCs, except it’s designed to steal data from Web server applications.
PC Trojans like ZeuS, for example, siphon information using two major techniques: snarfing passwords stored in the browser, and conducting “form grabbing” — capturing any data entered into a form field in the browser before it can be encrypted in the Web session and sent to whatever site the victim is visiting.
The malware that tore into the Smucker’s site behaved similarly, ripping out form data submitted by visitors — including names, addresses, phone numbers, credit card numbers and card verification code — as customers were submitting the data during the online checkout process.
What’s interesting about this attack is that it drives home one important point about malware’s role in subverting secure connections: Whether resident on a Web server or on an end-user computer, if either endpoint is compromised, it’s ‘game over’ for the security of that Web session. With Zeus, it’s all about surveillance on the client side pre-encryption, whereas what the bad guys are doing with these Web site attacks involves sucking down customer data post- or pre-encryption (depending on whether the data was incoming or outgoing).
Sally Beauty Hit By Credit Card Breach
Nationwide beauty products chain Sally Beauty appears to be the latest victim of a breach targeting their payment systems in stores, according to both sources in the banking industry and new raw data from underground cybercrime shops that traffic in stolen credit and debit cards.
On March 2, a fresh batch of 282,000 stolen credit and debit cards went on sale in a popular underground crime store. Three different banks contacted by KrebsOnSecurity made targeted purchases from this store, buying back cards they had previously issued to customers.
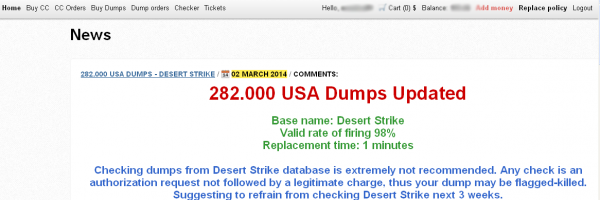
The card shop Rescator advertising a new batch of cards. 15 cards purchased by banks from this batch all were found to have been recently used at Sally Beauty stores.
The banks each then sought to determine whether all of the cards they bought had been used at the same merchant over the same time period. This test, known as “common point of purchase” or CPP, is the core means by which financial institutions determine the source of a card breach.
Each bank independently reported that all of the cards (15 in total) had been used within the last ten days at Sally Beauty locations across the United States. Denton, Texas-based Sally Beauty maintains some 2,600 stores, and the company has stores in every U.S. state.
Asked about the banks’ findings, Sally Beauty spokeswoman Karen Fugate said the company recently detected an intrusion into its network, but that neither the company’s information technology experts nor an outside forensics firm could find evidence that customer card data had been stolen from the company’s systems.
Fugate said Sally Beauty uses an intrusion detection product called Tripwire, and that a couple of weeks ago — around Feb. 24 — Tripwire detected activity. Unlike other products that try to detect intrusions based on odd or anomalous network traffic, Tripwire fires off alerts if it detects that certain key system files have been modified.
In response to the Tripwire alert, Fugate said, the company’s information technology department “shut down all external communications” and began an investigation. That included bringing in Verizon Enterprise Solutions, a company often hired to help businesses respond to cyber intrusions.
“Since [Verizon's] involvement, which has included a deconstruction of the methods used, an examination of network traffic, all our logs and all potentially accessed servers, we found no evidence that any data got out of our stores,” Fugate said. “But our investigation continues, of course with their assistance.”
Illinois Bank: Use Cash for Chicago Taxis
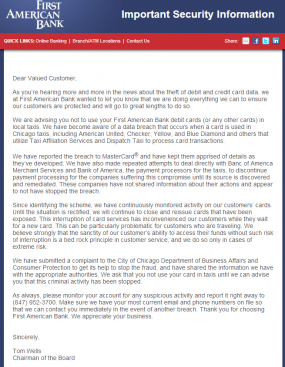
First American Bank in Illinois is urging residents and tourists alike to avoid paying for cab rides in Chicago with credit or debit cards, warning that an ongoing data breach seems to be connected with card processing systems used by a large number of taxis in the Windy City.
In an unusually blunt and public statement sent to customers on Friday, Elk Grove, Ill.-based First American Bank said, “We are advising you not to use your First American Bank debit cards (or any other cards) in local taxis.” The message, penned by the bank’s chairman Tom Wells, continued:
“We have become aware of a data breach that occurs when a card is used in Chicago taxis, including American United, Checker, Yellow, and Blue Diamond and others that utilize Taxi Affiliation Services and Dispatch Taxi to process card transactions.”
“We have reported the breach to MasterCard® and have kept them apprised of details as they’ve developed. We have also made repeated attempts to deal directly with Banc of America Merchant Services and Bank of America, the payment processors for the taxis, to discontinue payment processing for the companies suffering this compromise until its source is discovered and remediated. These companies have not shared information about their actions and appear to not have stopped the breach.”
Bank of America, in a written statement, declined to discuss the matter, saying BofA “cannot discuss specific client matters.” Neither Taxi Affiliation Services nor Dispatch Taxi returned messages seeking comment.
Christi Childers, associate general counsel and compliance officer at First American Bank, said the bank made the decision to issue the warning about 18 days after being alerted to a pattern of fraud on cards that were all previously used at taxis in Chicago. The bank, which only issues MasterCard debit cards, has begun canceling cards used in Chicago taxis, and has already reissued 220 cards related to the fraud pattern. So far, the bank has seen more than 466 suspicious charges totaling more than $62,000 subsequent to those cards being used in Chicago taxis.
Assisted Living Concepts Data Breach Exposes 43,600 Employees' Payroll Info
Current and former employees' names, addresses, birthdates, pay information and Social Security numbers were exposed.

Chicago's Assisted Living Concepts (ALC) recently began notifying approximately 43,600 current and former employees that their personal information may have been exposed when an unauthorized person gained access to ALC's login credentials at its payroll services vendor (h/t DataBreaches.net).
The breach occurred between December 14, 2013 and January 14, 2014, and exposed current and former employees' names, addresses, birthdates, Social Security numbers and pay information. The vendor notified ALC of the breach on February 14, 2014.
"We have reported the incident to law enforcement authorities, including the Federal Bureau of Investigation (FBI), and are cooperating with them," ALC CEO Jack R. Callison, Jr., wrote in the notification letter [PDF]. "In addition, upon learning of this issue, we immediately took steps to prevent any further unauthorized access to our payroll systems, deactivating the user credentials that were compromised and taking our payroll systems offline until the issues were resolved. Our vendor has also implemented a new, two-factor authentication procedure for access to sensitive payroll records. We are utilizing this new additional capability going forward."
Survey Finds 40 Percent of CryptoLocker Malware Victims Have Paid Ransom
Researchers at the University of Kent found that approximately one in 30 people in the U.K. have been hit by the ransomware.

A recent survey of 1,502 U.K. residents conducted by researchers at the University of Kent has found that approximately 40 percent of those whose computers were infected by the CryptoLocker ransomware have paid the ransom required to recover their data.
Approximately one in 30 respondents said they had been a victim of the ransomware.
"If the results reported on the rate of CryptoLocker victims who pay a ransom are to be strengthened by further research, these figures would be extremely troubling, netting criminals behind the ransomware hundreds of millions," University of Kent lecturer Dr. Julio Cesar Hernandez-Castro said in a statement.
"This would encourage them to continue with this form of cybercrime, potentially prompting other criminal gangs to jump into an extremely profitable cybercrime market," Hernandez-Castro added.
The survey also found that while more than two thirds of respondents said they feel at risk of cybercrime when online, and more than a quarter said they'd been a victim of a cyber attack over the past year, fully 28.2 percent claimed not to engage in any security practices online at all, such as using anti-virus software, firewalls or password management tools.
An executive summary of the survey's findings can be viewed here [PDF].

ReplyDeleteThis site is good because they give us a new thing and new ideas and new topic how good all of they are we should appreciate them because of these good thing.
I know something information, to know you can click here
airport taxi princeton
taxi in princeton
taxi cabs
I Interesting post. I have been wondering about this issue,so thanks for posting.
ReplyDeleteTo get new information visit here
auto mechanic Brisbane
Car Services Brisbane
four wheel drive suspension