360 million newly stolen credentials on black market -- cybersecurity firm
26 February 2014 /BOSTON, REUTERS
A cybersecurity firm said on Tuesday that it uncovered stolen credentials from some 360 million accounts that are available for sale on cyber black markets, though it is unsure where they came from or what they can be used to access.
Alex Holden, chief information security officer of Hold Security LLC, said in an interview that his firm obtained the data over the past three weeks, meaning an unprecedented amount of stolen credentials is available for sale underground. “The sheer volume is overwhelming,” said Holden, whose firm last year helped uncover a major data breach at Adobe Systems Inc in which tens of millions of records were stolen.
Holden said he believes the 360 million records were obtained in separate attacks, including one that yielded some 105 million records, which would make it the largest single credential breaches known to date.
He said he believes the credentials were stolen in breaches that have yet to be publicly reported. The companies attacked may remain unaware until they are notified by third parties who find evidence of the hacking, he said. “We have staff working around the clock to identify the victims,” he said.
He has not provided any information about the attacks to other cybersecurity firms or authorities but intends to alert the companies involved if his staff can identify them.
The massive trove of credentials includes user names, which are typically email addresses, and passwords that in most cases are in unencrypted text. Holden said that in contrast, the Adobe breach, which he uncovered in October 2013, yielded tens of millions of records that had encrypted passwords, which made it more difficult for hackers to use them.
The email addresses are from major providers such as AOL Inc , Google Inc, Microsoft Corp and Yahoo Inc and almost all Fortune 500 companies and nonprofit organizations. Holden said he alerted one major email provider that is a client, but he declined to identify the company, citing a nondisclosure agreement.
Heather Bearfield, who runs the cybersecurity practice for accounting firm Marcum LLP, said she had no information about the information that Hold Security uncovered but that it was plausible for hackers to obtain such a large amount of data because these breaches are on the rise.
She said hackers can do far more harm with stolen credentials than with stolen payment cards, particularly when people use the same login and password for multiple accounts. “They can get access to your actual bank account. That is huge,” Bearfield said. “That is not necessarily recoverable funds.”
After recent payment-card data breaches, including one at US retailer Target, credit card companies stressed that consumers bear little risk because they are refunded rapidly for fraud losses.
Wade Baker, a data breach investigator with Verizon Communications Inc, said that the number of attacks targeting payment cards through point-of-sales systems peaked in 2011. That was partly because banks and retailers have gotten better at identifying that type of breach and quickly moving to prevent crooks from making fraudulent transactions, he said.
In addition to the 360 million credentials, the criminals are selling some 1.25 billion email addresses, which would be of interest to spammers, Hold Security said in a statement on its website.
Card Backlog Extends Pain from Target Breach
Last week’s story about steeply falling prices on credit and debit card data stolen from Target mentioned several reasons why many banks may not have already reissued all of their cards impacted by the breach. But it left out one other key reason: A huge backlog of orders at companies that manufacture credit and debit cards on behalf of financial institutions.
 Turns out, while the crooks responsible for monetizing the Target breach seem to have had little trouble counterfeiting stolen cards, the process by which banks obtain legitimate replacement cards for their customers is not always quite so speedy.
Turns out, while the crooks responsible for monetizing the Target breach seem to have had little trouble counterfeiting stolen cards, the process by which banks obtain legitimate replacement cards for their customers is not always quite so speedy.
I recently spoke with a gentleman who heads up security at a small federal credit union, and this individual said his institution ended up printing their own cards in-house after being told by their financial services provider that their order for some 2,000 new customer cards compromised in the Target breach would have to get behind a backlog of more than 2 million existing orders from other banks.
The credit union in question issues Visa-branded cards to its customers, but the actual physical cards are produced by Fiserv, a Brookfield, Wisc. financial services firm that also handles the online banking portals for a huge number of small to mid-sized financial institutions nationwide. In addition to servicing this credit union, Fiserv also prints cards for some of the biggest banks in the world, including Bank of America and Chase.
Shortly after the holidays, the credit union began alerting affected customers, notifying them that the institution would soon be reissuing cards. But when it actually went to place the order for the new cards, the institution was told it would have to get in line.
“They informed us that there was a backlog of 2 million cards, and said basically, ‘We’ll get to you when we get to you’,” the credit union source told KrebsOnSecurity.
Murray Walton, chief risk officer at Fiserv, acknowledged that the company has experienced extraordinarily high demand for new cards in the wake of the Target breach, but that Fiserv is quickly whittling down its existing backlog of orders.
“A large breach injects additional demand into a system that is already operating at near-peak capacity at year-end,” Walton said. “As a result, producers face the challenge of juggling existing contractual commitments with this incremental demand, and turn to mandatory overtime and staff augmentation to get the most out of their equipment and infrastructure. We believe we are managing this situation as well as possible, and are beginning to see our cycle times (order to delivery) diminish compared to a few weeks ago. Meanwhile, we note that fraud prevention is a multi-faceted challenge, and card reissue is only one arrow in the quiver. Alert consumers and behind-the-scenes fraud management programs are also essential.”
Faced with mounting customer service requests from account holders who’d been told to expect new cards, the credit union decided to take matters into its own hands.
“We have the capability to print out the cards ourselves at a local branch, so some of our software developers wrote some scripts to export the customer data and we had two people who ended up burning the midnight oil for several days making these cards by hand.”
iOS Update Quashes Dangerous SSL Bug
Apple on Friday released a software update to fix a serious security weakness in its iOS mobile operating system that allows attackers to read and modify encrypted communications on iPhones, iPads and other iOS devices. The company says it is working to produce a patch for the same flaw in desktop and laptop computers powered by its OS X operating system.
 The update — iOS 7.0.6 — addresses a glaring vulnerability in the way Apple devices handle encrypted communications. The flaw allows an attacker to intercept, read or modify encrypted email, Web browsing, Tweets and other transmitted data, provided the attacker has control over the WiFi or cellular network used by the vulnerable device.
The update — iOS 7.0.6 — addresses a glaring vulnerability in the way Apple devices handle encrypted communications. The flaw allows an attacker to intercept, read or modify encrypted email, Web browsing, Tweets and other transmitted data, provided the attacker has control over the WiFi or cellular network used by the vulnerable device.
There has been a great deal of speculation and hand-waving about whether this flaw was truly a mistake or if it was somehow introduced intentionally as a backdoor. And it’s not yet clear how long this bug has been included in Apple’s software. In any case, if you have an iPhone or iPad or other iOS device, please take a moment to apply this fix.
Generally, I advise users to avoid downloading and installing security updates when they are using public WiFi or other untrusted networks. On the surface at least, it would seem that the irony of this situation for most users is that iOS devices will download updates automatically as long as users are connected to a WiFi network. But as several folks have already pointed out on Twitter, Apple uses code-signing on iOS and app updates to ensure that rogue code can’t be pushed to devices.
I will update this post when Apple ships the patch for OS X systems. For now, it may be wise to avoid using Safari on OS X systems. As Dan Goodin at Ars Technica writes, “because the Google Chrome and Mozilla Firefox browsers appear to be unaffected by the flaw, people should also consider using those browsers when possible, although they shouldn’t be considered a panacea.”
For a deeper dive on this vulnerability and its implications, check out this piece by Larry Seltzer at ZDNet, and this analysis by Google’s Adam Langley.
Fire Sale on Cards Stolen in Target Breach
Last year’s breach at Target Corp. flooded underground markets with millions of stolen credit and debit cards. In the days surrounding the breach disclosure, the cards carried unusually high price tags — in large part because few banks had gotten around to canceling any of them yet. Today, two months after the breach, the number of unsold stolen cards that haven’t been cancelled by issuing banks is rapidly shrinking, forcing the miscreants behind this historic heist to unload huge volumes of cards onto underground markets and at cut-rate prices.
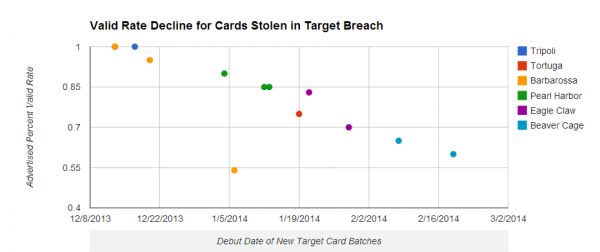
Cards stolen in the Target breach have become much cheaper as more of them come back declined or cancelled by issuing banks.
Earlier today, the underground card shop Rescator[dot]so moved at least 2.8 million cards stolen from U.S.-based shoppers during the Target breach. This chunk of cards, dubbed “Beaver Cage” by Rescator, was the latest of dozens of batches of cards stolen from Target that have gone on sale at the shop since early December.
The Beaver Cage batch of cards have fallen in price by as much as 70 percent compared to those in “Tortuga,” a huge chunk of several million cards stolen from Target that sold for between $26.60 and $44.80 apiece in the days leading up to Dec. 19 — the day that Target acknowledged a breach. Today, those same cards are now retailing for prices ranging from $8 to $28. The oldest batches of cards stolen in the Target breach –i.e., the first batches of stolen cards sold –are at the top of legend in the graphic above; the “newer,” albeit less fresh, batches are at the bottom.
The core reason for the price drop appears to be the falling “valid rate” associated with each batch. Cards in the Tortuga base were advertised as “100 percent valid,” meaning that customers who bought ten cards from the store could expect all 10 to work when they went to use them at retailers to purchase high-priced electronics, gift cards and other items that can be quickly resold for cash.
This latest batch of Beaver Cage cards, however, carries only a 60 percent valid rate, meaning that on average customers can expect at least 4 out of every 10 cards they buy to come back declined or canceled by the issuing bank.
The most previous batch of Beaver Cage cards — pushed out by Rescator on Feb. 6 — included nearly 4 million cards stolen from Target and carried a 65 percent valid rate. Prior to Beaver Cage, the Target cards were code-named “Eagle Claw.” On Jan. 29, Rescator debuted 4 million cards bearing the Eagle Claw name and a 70 percent valid rate. The first two batches of Eagle Claw-branded cards — a chunk of 2 million cards — were released on Jan. 21 with a reported 83 percent valid rate.

No comments:
Post a Comment