http://rt.com/usa/us-banks-magnetic-card-target-651/
( The use of outdated technology in US ( when compared with Europe and Canada ) gives thieves an edge - banks and retailers share blame for US weaknesses )
http://uk.reuters.com/article/2013/12/24/uk-target-databreach-exclusive-idUKBRE9BN0L420131224
http://www.zerohedge.com/news/2013-12-25/target-hack-included-pin-numbers
( Basically bank accounts are now at risk if you have used a debit card recently - Black Friday to mid December ( for now at Target but if the problem lies at the point of system technology level and not the merchant , it could be any debit card used anywhere during the timeframe at issue presently ... )
http://krebsonsecurity.com/2013/12/cards-stolen-in-target-breach-flood-underground-markets/
( The use of outdated technology in US ( when compared with Europe and Canada ) gives thieves an edge - banks and retailers share blame for US weaknesses )
Magnetic swipe: Obsolete credit card tech makes US prime Target for fraudsters
The attack on millions of customers’ credit cards at retailer Target has exposed the outdated security tools used in banking. And while the US is scheduled to switch to more modern card protection in 2015, not all parties are interested in modernization.
“We are using 20th century cards against 21st century hackers. The thieves have moved on but the cards have not,” Mallory Duncan, general counsel at the National Retail Federation told AP.
Target has refused to specify the means by which fraudsters managed to steal the data of up to 40 million customers between November 27 and December 15. But almost all experts, citing industry sources and existing fraud cases, say most likely the data was siphoned with special devices attached to payment terminals, which scanned the magnetic strips on the back of the card.
This type of hacking would not have been possible had Target used Chip and PIN cards, officially known as EMV, which encrypt the data, making it much harder to intercept at the point of use. In contrast the technology on magnetic stripes is similar to that of cassette tapes, which became obsolete more than a decade ago; they can also be easily reproduced.
More than 90 percent of all cards in the EU and four out of five in Canada use EMV. In total there are 1.6 billion of them around the world. Contrastingly, about 1 percent of US cards have the technology, and even those are not secure, as only one in ten American payment terminals can actually process information from the chip.
“The US is one of the last markets to convert from the magnetic stripe. There are fewer places in the world where that stolen data could be used. So the US becomes more of a high-value target,” Randy Vanderhoof, director of the EMV Migration Forum told UPI.
Major credit card issuers have told the US to fall in line with the rest of the world by October 2015. From that date onwards, whoever is responsible for the weakest link in the security chain will be left to foot the bill for a fraudulent transaction, which should theoretically incentivize banks and retailers to provide better security measures.
Only it isn’t that simple.
US banks have calculated that the amount they lose from fraud – on average – is smaller than paying for a rollout of brand new terminals and cards across the country. They also enjoy better fees for processing the cumbersome and ineffectual signature verifications than they would if the system was converted to PIN as elsewhere.
“Compared to the tens of millions of transactions that are taking place every day, even the fraud that they have to pay for is small compared to the profit they are making from using less secure cards,” said Duncan.
Meanwhile retailers do not want to foot the bill either, and have engaged in legal battles with banks, which are only likely to intensify as the new data networks need to be created.
In the rest of the world the changeover was either mandated by the government, or brand new payment systems were put in where cards had not been used before at all, as in developing markets.
Experts estimate that by the October 2015 only 60 percent of cards will be compliant with new technology requirements.
In the meantime, it is likely the customers will have to pay for the increased susceptibility to fraud – in the form of higher banking charges needed to cover the theft. Though the situation simply can’t carry on as now, particularly as US citizens are now often struggling to have their old-fashioned credit cards accepted in parts of the world.
“Part of the cost in the system is for fraud protection. It costs money, and someone's going to pay for it eventually,” Jason Oxman, chief executive of the Electronic Transactions Association, told AP.
http://uk.reuters.com/article/2013/12/24/uk-target-databreach-exclusive-idUKBRE9BN0L420131224
Exclusive: Target hackers stole encrypted bank PINs - source
BOSTON/NEW YORK
1 OF 3. People shop at a Target store during Black Friday sales in the Brooklyn borough of New York, November 29, 2013.
CREDIT: REUTERS/ERIC THAYER
(Reuters) - The hackers who attacked Target Corp and compromised up to 40 million credit cards and debit cards also managed to steal encrypted personal identification numbers (PINs), according to a senior payments executive familiar with the situation.
One major U.S. bank fears that the thieves would be able to crack the encryption code and make fraudulent withdrawals from consumer bank accounts, said the executive, who spoke on the condition of anonymity because the data breach is still under investigation.
Target spokeswoman Molly Snyder said "no unencrypted PIN data was accessed" and there was no evidence that PIN data has been "compromised." She confirmed that some "encrypted data" was stolen, but declined to say if that included encrypted PINs.
"We continue to have no reason to believe that PIN data, whether encrypted or unencrypted, was compromised. And we have not been made aware of any such issue in communications with financial institutions to date," Snyder said by email. "We are very early in an ongoing forensic and criminal investigation."
The No. 3 U.S. retailer said last week that hackers stole data from as many as 40 million cards used at Target stores during the first three weeks of the holiday shopping season, making it the second-largest data breach in U.S. retail history.
Target has not said how its systems were compromised, though it described the operation as "sophisticated." The U.S. Secret Service and the Justice Department are investigating. Officials with both agencies have declined comment on the investigations.
The attack could end up costing hundreds of millions of dollars, but it is unclear so far who will bear the expense.
While bank customers are typically not liable for losses because of fraudulent activity on their credit and debit cards, JPMorgan Chase & Co and Santander Bank said they have lowered limits on how much cash customers can take out of teller machines and spend at stores.
The unprecedented move has led to complaints from consumer advocates about the inconvenience it caused from the late November Thanksgiving holiday into the run-up to Christmas. But sorting out account activity after a fraudulent withdrawal could take a lot more time and be worse for customers.
JPMorgan has said it was able to reduce inconvenience by giving customers new debit cards printed quickly at many of its branches, and by keeping branches open for extended hours. A Santander spokeswoman was not available for comment on Tuesday.
Security experts said it is highly unusual for banks to reduce caps on withdrawals, and the move likely reflects worries that PINs have fallen into criminal hands, even if they are encrypted.
"That's a really extreme measure to take," said Avivah Litan, a Gartner analyst who specializes in cyber security and fraud detection. "They definitely found something in the data that showed there was something happening with cash withdrawals."
BREAKING THE CODE
While the use of encryption codes may prevent amateur hackers from obtaining the digital keys to customer bank deposits, the concern is the coding cannot stop the kind of sophisticated cyber criminal who was able to infiltrate Target for three weeks.
Daniel Clemens, CEO of Packet Ninjas, a cyber security consulting firm, said banks were prudent to lower debit card limits because they will not know for sure if Target's PIN encryption was infallible until the investigation is completed.
As an example of potential vulnerabilities in PIN encryption, Clemens said he once worked for a retailer who hired his firm to hack into its network to find security vulnerabilities. He was able to access the closely guarded digital "key" used to unscramble encrypted PINs, which he said surprised his client, who thought the data was secure.
In other cases, hackers can get PINs by using a tool known as a "RAM scraper," which captures the PINs while they are temporarily stored in memory, Clemens said.
The attack on Target began on November 27, the day before the Thanksgiving holiday and continued until December 15. Banks that issue debit and credit cards learned about the breach on December 18, and Target publicly disclosed the loss of personal account data on December 19.
On December 21, JPMorgan, the largest U.S. bank, alerted 2 million of its debit cardholders that it was lowering the daily limits on ATM withdrawals to $100 and capping store purchases with their cards at $500.
On Monday, the bank partly eased the limits it had imposed on Saturday, setting them at $250 a day for ATM withdrawals and $1,000 a day for purchases. (The usual debit card daily limits are $200 to $500 for cash withdrawals and $500 for purchases, a bank spokeswoman said last week.)
On Monday, Santander - a unit of Spain's Banco Santander - followed suit, lowering the daily limits on cash withdrawals and purchases on Santander and Sovereign branded debit and credit cards of customers who used them at Target when the breach occurred. Santander did not disclose the new limits, but said it was monitoring the accounts and issuing new cards to customers who were affected.
The largest breach against a U.S. retailer, uncovered in 2007 at TJX Cos Inc, led to the theft of data from more than 90 million credit cards over about 18 months.
and.....
( Basically bank accounts are now at risk if you have used a debit card recently - Black Friday to mid December ( for now at Target but if the problem lies at the point of system technology level and not the merchant , it could be any debit card used anywhere during the timeframe at issue presently ... )
Target Hack Included PIN Numbers
Submitted by Tyler Durden on 12/25/2013 08:49 -0500
When the first response taken by major banks such as JPMorgan, in the aftermath of the massive 40 million credit and debit card hack of the third largest US retailer Target, was to lower ATM withdrawal and purchase limits, it became clear that there was more here than simply a well-organized credit card number scrape. And indeed, as Reuters reports, the hackers who compromised up to 40 million credit cards and debit cards also managed to steal encrypted personal identification numbers (PINs) according to a senior payments executive familiar with the situation. And since from there to emptying bank accounts and saved deposits is only a keystroke away, with no credit card processor intermediate to offload liability to, banks had no choice but to immediately limit debit card access to as much 10% of their clients, in JPM's case, in an unprecedented first, which just may have shown the way of how to limit a cash withdrawal panic if and when the need to do so arises.
Target has not said how its systems were compromised, though it described the operation as "sophisticated." The U.S. Secret Service and the Justice Department are investigating. Officials with both agencies have declined comment on the investigations.The attack could end up costing hundreds of millions of dollars, but it is unclear so far who will bear the expense....Daniel Clemens, CEO of Packet Ninjas, a cyber security consulting firm, said banks were prudent to lower debit card limits because they will not know for sure if Target's PIN encryption was infallible until the investigation is completed.As an example of potential vulnerabilities in PIN encryption, Clemens said he once worked for a retailer who hired his firm to hack into its network to find security vulnerabilities. He was able to access the closely guarded digital "key" used to unscramble encrypted PINs, which he said surprised his client, who thought the data was secure.In other cases, hackers can get PINs by using a tool known as a "RAM scraper," which captures the PINs while they are temporarily stored in memory, Clemens said.The attack on Target began on November 27, the day before the Thanksgiving holiday and continued until December 15. Banks that issue debit and credit cards learned about the breach on December 18, and Target publicly disclosed the loss of personal account data on December 19.
And since in black hat hacker circles what is known by one is known by all, it is only a matter of time before America's other largest retailers, are hit by the same PIN scraping technique, which in turn "forces" the banks to once again lower ATM withdrawal limits on a few million other debit card users. Ironically, perhaps instead of focusing on where the poor and middle classes shop, it may be time for the black hat hacker community to take a look at companies like Netjets and Ferrari where the PIN "scraping" wouldn't drain the fund of the median income American but focus on those who have directly benefited from Bernanke's ongoing asset inflation monetary experiment.
and...
http://www.cnbc.com/id/101293579
Banks could sue over Target breach
Cards Stolen in Target Breach Flood Underground Markets
Credit and debit card accounts stolen in a recent data breach at retail giant Target have been flooding underground black markets in recent weeks, selling in batches of one million cards and going for anywhere from $20 to more than $100 per card, KrebsOnSecurity has learned.
Prior to breaking the story of the Target breach on Wednesday, Dec. 18, I spoke with a fraud analyst at a major bank who said his team had independently confirmed that Target had been breached after buying a huge chunk of the bank’s card accounts from a well-known “card shop” — an online store advertised in cybercrime forums as a place where thieves can reliably buy stolen credit and debit cards.
There are literally hundreds of these shady stores selling stolen credit and debit cards from virtually every bank and country. But this store has earned a special reputation for selling quality “dumps,” data stolen from the magnetic stripe on the backs of credit and debit cards. Armed with that information, thieves can effectively clone the cards and use them in stores. If the dumps are from debit cards and the thieves also have access to the PINs for those cards, they can use the cloned cards at ATMs to pull cash out of the victim’s bank account.
At least two sources at major banks said they’d heard from the credit card companies: More than a million of their cards were thought to have been compromised in the Target breach. One of those institutions noticed that one card shop in particular had recently alerted its loyal customers about a huge new batch of more than a million quality dumps that had been added to the online store. Suspecting that the advertised cache of new dumps were actually stolen in the Target breach, fraud investigators with the bank browsed this card shop’s wares and effectively bought back hundreds of the bank’s own cards.
When the bank examined the common point of purchase among all the dumps it had bought from the shady card shop, it found that all of them had been used in Target stores nationwide between Nov. 27 and Dec. 15. Subsequent buys of new cards added to that same shop returned the same result.
On Dec. 19, Target would confirm that crooks had stolen 40 million debit and credit cards from stores nationwide in a breach that extended from Nov. 27 to Dec. 15. Not long after that announcement, I pinged a source at a small community bank in New England to see whether his institution had been notified by Visa or MasterCard about specific cards that were potentially compromised in the Target breach.
This institution has issued a grand total of more than 120,000 debit and credit cards to its customers, but my source told me the tiny bank had not yet heard anything from the card associations about specific cards that might have been compromised as a result of the Target breach. My source was anxious to determine how many of the bank’s cards were most at risk of being used for fraud, and how many should be proactively canceled and re-issued to customers. The bank wasn’t exactly chomping at the bit to re-issue the cards; that process costs around $3 to $5 per card, but more importantly it didn’t want to unnecessarily re-issue cards at a time when many of its customers would be racing around to buy last-minute Christmas gifts and traveling for the holidays.
On the other hand, this bank had identified nearly 6,000 customer cards — almost 5 percent of all cards issued to customers — that had been used at Target stores nationwide during the breach window described by the retailer.
“Nobody has notified us,” my source said. “Law enforcement hasn’t said anything, our statewide banking associations haven’t sent anything out…nothing. Our senior legal counsel today was asking me if we have positive confirmation from the card associations about affected cards, but so far we haven’t gotten anything.”
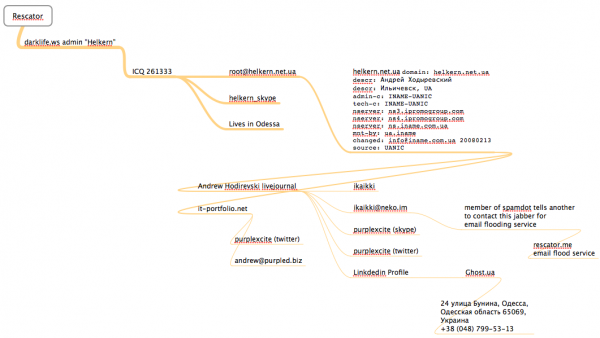
When I mentioned that a big bank I’d spoken with had found a 100 percent overlap with the Target breach window after purchasing its available cards off a particular black market card shop called rescator[dot]la, my source at the small bank asked would I be willing to advise his fraud team on how to do the same?
CARD SHOPPING
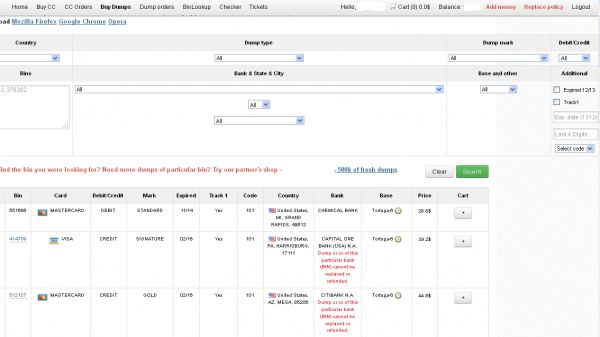
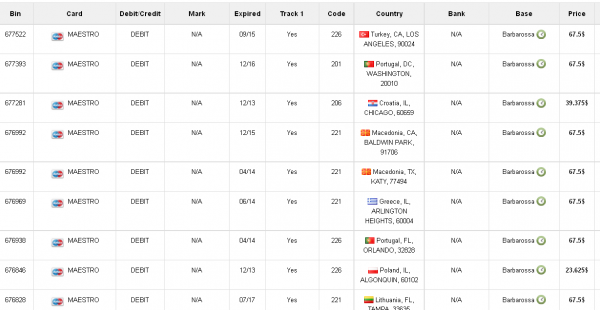
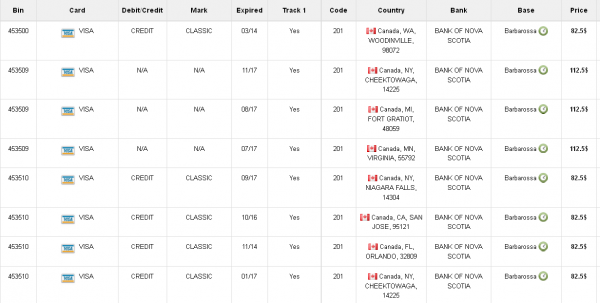
Ultimately, I agreed to help in exchange for permission to write about the bank’s experience without actually naming the institution. The first step in finding any of the bank’s cards for sale was to browse the card shop’s remarkably efficient and customer-friendly Web site and search for the bank’s “BINs”; the Bank Identification Number is merely the first six digits of a debit or credit card, and each bank has its own unique BIN or multiple BINs.

According to the “base” name for all stolen cards sold at this card shop, the proprietor sells only cards stolen in the Target breach.
A quick search on the card shop for the bank’s BINs revealed nearly 100 of its customers’s cards for sale, a mix of MasterCard dumps ranging in price from $26.60 to $44.80 apiece. As one can imagine, this store doesn’t let customers pay for purchases with credit cards; rather, customers can “add money” to their accounts using a variety of irreversible payment mechanisms, including virtual currencies like Bitcoin, Litecoin, WebMoney and PerfectMoney, as well as the more traditional wire transfers via Western Union and MoneyGram.
With my source’s newly registered account funded via wire transfer to the tune of USD $450, it was time to go shopping. My source wasn’t prepared to buy up all of the available cards that match his institution’s BINs, so he opted to start with a batch of 20 or so of the more recently-issued cards for sale.
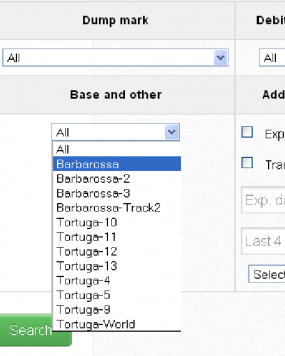
Like other card shops, this store allows customers to search for available cards using a number of qualifications, including BIN; dozens of card types (MasterCard, Visa, et. al.); expiration date; track type; country; and the name of the financial institution that issued the card.
A key feature of this particular dumps shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle.”
Indeed, shortly after the Target breach began, the proprietor of this card shop — a miscreant nicknamed “Rescator” and a key figure on a Russian-language cybercrime forum known as “Lampeduza” — was advertising a brand new base of one million cards, called Tortuga.
Rescator even created a graphical logo in the Lampeduza forum’s typeface and style, advertising “valid 100% rate,” and offering a money-back guarantee on any cards from this “fresh” base that were found to have been canceled by the card issuer immediately after purchase. In addition, sometime in December, this shop ceased selling cards from other bases aside from those from the Tortuga base. As the month wore on, new Tortuga bases would be added to shop, with each base incrementing by one with almost every passing day (e.g., Tortuga1, Tortuga2, Tortuga3, etc.).
Another fascinating feature of this card shop is that it appears to include the ZIP code and city of the store from which the cards were stolen. One fraud expert I spoke with who asked to remain anonymous said this information is included to help fraudsters purchasing the dumps make same-state purchases, thus avoiding any knee-jerk fraud defenses in which a financial institution might block transactions out-of-state from a known compromised card.
The New England bank decided to purchase 20 of its own cards from this shop, cards from Tortuga bases 6-9, and Tortuga 14 and 15. The store’s “shopping cart” offers the ability to check the validity of each purchased card. Any cards that are checked and found to be invalid automatically get refunded. A check of the cards revealed that just one of the 20 had already been canceled.
The bank quickly ran a fraud and common point-of-purchase analyses on each of the 19 remaining cards. Sure enough, the bank’s database showed that all had been used by customers to make purchases at Target stores around the country between Nov. 29 and Dec. 15.
“Some of these already have confirmed fraud on them, and a few of them were actually just issued recently and have only been used at Target,” my source told me. Incredibly, a number of the cards were flagged for fraud after they were used to make unauthorized purchases at big box retailers, including — wait for it — Target. My source explained that crooks often use stolen dumps to purchase high-priced items such as Xbox consoles and high-dollar amount gift cards, goods that can be fenced, auctioned or otherwise offloaded quickly and easily for cash.
My source said his employer isn’t yet sure which course of action it will take, but that it’s likely the bank will re-issue some or all of the 5,300+ cards affected by the Target breach — most likely sometime after Dec. 25.
The bank is unconcerned that its cards compromised in the Target breach might be used for online shopping fraud because the stolen data does not include the CVV2 — the three digit security code printed on the backs of customer cards. Most online merchants require customers to supply the CVV2 as proof that they posses the legitimate, physical card for the corresponding account that is being used to fund the online purchase.
Update, 5:20 p.m. ET: In a message to consumers, Target CEO Gregg Steinhafel said Target would be offering free credit monitoring for affected customers. Not sure how credit monitoring helps with this specific breach, but at any rate here’s the rest of his statement:“Yesterday we shared that there was unauthorized access to payment card data at our U.S. stores. The issue has been identified and eliminated. We recognize this has been confusing and disruptive during an already busy holiday season. Our guests’ trust is our top priority at Target and we are committed to making this right.We want our guests to understand that just because they shopped at Target during the impacted time frame, it doesn’t mean they are victims of fraud. In fact, in other similar situations, there are typically low levels of actual fraud. Most importantly, we want to reassure guests that they will not be held financially responsible for any credit and debit card fraud. And to provide guests with extra assurance, we will be offering free credit monitoring services. We will be in touch with those impacted by this issue soon on how and where to access the service.We understand it’s been difficult for some guests to reach us via our website and call center. We apologize and want you to understand that we are experiencing unprecedented call volume. Our Target teams are working continuously to build capacity and meet our guests’ needs.We take this crime seriously. It was a crime against Target, our team members, and most importantly, our guests. We’re in this together, and in that spirit, we are extending a 10% discount – the same amount our team members receive – to guests who shop in U.S. stores on Dec. 21 and 22. Again, we recognize this issue has been confusing and disruptive during an already busy holiday season. We want to emphasize that the issue has been addressed and let guests know they can shop with confidence at their local Target stores.”









![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](http://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
![Rescator, a.k.a. "Hel" a.k.a. "Helkern" the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.](http://krebsonsecurity.com/wp-content/uploads/2013/12/vor-1edited-600x414.png)
![Darklife admin "Helkern" brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.](http://krebsonsecurity.com/wp-content/uploads/2013/12/cihhacked-600x470.png)



![The email flood service at rescator[dot]me](http://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-me-news-600x360.png)


Merry Christmas,
ReplyDeleteThe Target card theft articles were very informative and interesting. I guess the black ops side of government must be getting a cut from fraud like this because it would appear that they could easily track down the perp's if they wanted to.
37 tons for Germany and they are probably lucky to get that. The PM story gets more interesting everyday.
Oh I did some Christmas eve shopping also and it wasn't overly busy at Valley View Mall or even Wal-Mart. In fact I just picked up some tissue paper at Wal-mart and walked right up to a register and paid.
DeleteMerry Xmas ! Wish all the best to you and your family !
Delete