Target.....
http://www.informationweek.com/security/attacks-and-breaches/target-breach-10-facts/d/d-id/1113228
http://krebsonsecurity.com/2013/12/cards-stolen-in-target-breach-flood-underground-markets/







http://krebsonsecurity.com/2013/12/sources-target-investigating-data-breach/







It’s not clear how many cards thieves may have stolen in the breach. But the sources I spoke with from two major card issuers said they have so far been notified by one of the credit card associations regarding more than one million of cards total from both issuers that were thought to have been compromised in the breach. A third source at a data breach investigation firm said it appears that “when all is said and done, this one will put its mark up there with some of the largest retail breaches to date.”
http://krebsonsecurity.com/2013/12/the-biggest-skimmers-of-all-fake-atms/









http://www.zdnet.com/adobe-warns-of-license-key-email-scam-7000024576/

http://www.informationweek.com/security/attacks-and-breaches/target-breach-10-facts/d/d-id/1113228
Target Breach: 10 Facts
Just in time for the holidays, Target confirmed Thursday that its systems were breached.
Thanks to the breach, one or more attackers successfully stole 40 million credit card numbers. Anyone who used a credit or debit card in any of Target's US stores between November 27 and December 15 may be a victim. Target.com users and customers at Target stores in Canada are not affected.
The Target attackers gained access not only to card numbers, but also card expiration dates, CVV codes, and cardholders' names. As a result, they could use the stolen information to make fraudulent purchases via phone or online as well as to create working counterfeit credit cards.
[For more on the Target breach, see Target Confirms Hackers Stole 40 Million Credit Cards.]
How did hackers likely steal the credit card data, and what should consumers who may have been affected by the breach do next?
Here's what we know about the breach, its likely repercussions for affected cardholders, and how they should respond:
1. Target declines to comment on data encryption questions.
How did hackers manage to steal 40 million cards? That's a pertinent question, since any retailer that stores credit card data, according to the Payment Card Industry Data Security Standard (PCI-DSS), is required to encrypt that data. Furthermore, if the data is properly encrypted in transit and at rest, it shouldn't be of any use to attackers.
How did hackers manage to steal 40 million cards? That's a pertinent question, since any retailer that stores credit card data, according to the Payment Card Industry Data Security Standard (PCI-DSS), is required to encrypt that data. Furthermore, if the data is properly encrypted in transit and at rest, it shouldn't be of any use to attackers.
"This is a breach that should've never happened," Forrester analyst John Kindervag said in an emailed statement. "The fact that three-digit CVV security codes were compromised shows they were being stored. Storing CVV codes has long been banned by the card brands and the PCI [Security Standards Council]."
Reached via email, a Target official declined to respond to questions about whether the retailer had stored the stolen card data in encrypted format, or whether it had been certified as PCI-compliant. "We continue to invest in our security practices to protect our guests' information including the retention of a leading third-party forensics firm to conduct a thorough investigation of this incident," Target spokeswoman Molly Snyder said via email. "We apologize for any inconvenience this has caused our guests."
Target has also declined to address how attackers got their hands on the data in the first place. "As this is an ongoing investigation, we don't have additional details to share on the questions you asked," said Snyder.
2. Malware, point-of-sale apps, and insiders suspected.
The fact that the Target data breach didn't touch its e-commerce operation, but rather its stores, suggests that attackers gained access to information that was gathered via point-of-sale (POS) terminals -- a fancy name for electronic cash registers.
The fact that the Target data breach didn't touch its e-commerce operation, but rather its stores, suggests that attackers gained access to information that was gathered via point-of-sale (POS) terminals -- a fancy name for electronic cash registers.
Hord Tipton, executive director of (ISC)2, said in an emailed statement that attackers likely infected massive numbers of POS terminals with malware. "It's one thing to compromise or affect one machine, but to get all of them begs the question of how this was plotted out in the first place," Tipton said. "How were the hackers so efficient? From what I can tell, it looks like an insider threat -- someone on the inside probably helped."
Alternately, attackers may have been able to remotely tap into the POS terminals by exploiting vulnerabilities in their built-in Web servers, Bala Venkat, the chief marketing officer for Web application security vendor Cenzic, said in an emailed statement. "When searching for vulnerable targets, attackers are discovering that many retail merchants and point-of-sale terminals haven't implemented some of the basic security measures required by [PCI]," he said, which would include two-factor authentication on the terminals for anyone attempting to remotely connect to it.
The breach was likely compounded by Target failing to monitor its POS terminals for signs of attack. "This seems rather obvious from the information revealed already about this Target breach," Venkat said.
But Gartner analyst Avivah Litan said in a blog post that the breach was likely not due to malware or hacking, but a very low-tech -- and insider -- attack. "If we've learned anything from the Snowden/NSA and WikiLeaks/Bradley Manning affairs, it's that insiders can cause the most damage because some basic controls are not in place," she said. "I wouldn't be surprised if that's the case with the Target Breach -- i.e., that Target did a great job protecting their systems from external intruders but dropped the ball when it came to securing insider access."
3. Full investigation may take months.
Although a statement released by Target said that it "has identified and resolved the issue" exploited by the attackers, it may be many months before Target has a complete picture of how the breach occurred. "It will be interesting to see how the attackers got into the network and what technical countermeasures were in place, but that will take months to surface as the forensics in such a case are extremely time consuming," Qualys CTO Wolfgang Kandek said via email.
Although a statement released by Target said that it "has identified and resolved the issue" exploited by the attackers, it may be many months before Target has a complete picture of how the breach occurred. "It will be interesting to see how the attackers got into the network and what technical countermeasures were in place, but that will take months to surface as the forensics in such a case are extremely time consuming," Qualys CTO Wolfgang Kandek said via email.
4. Stolen cards are already flooding black market.
Security experts said the timing of the breach corresponds with a recent surge of stolen credentials being offered for sale on underground cybercrime forums. "We started to detect that something was afoot on December 11th when [we] detected a massive increase – 10 - 20x -- in availability of high-value stolen cards on black-market sites," read a blog post from security vendor Easy Solutions. "Nearly every bank and [credit union] in the US seems to be affected."
Security experts said the timing of the breach corresponds with a recent surge of stolen credentials being offered for sale on underground cybercrime forums. "We started to detect that something was afoot on December 11th when [we] detected a massive increase – 10 - 20x -- in availability of high-value stolen cards on black-market sites," read a blog post from security vendor Easy Solutions. "Nearly every bank and [credit union] in the US seems to be affected."
Target has yet to say how it learned of the breach. But having a massive quantity of stolen credit cards flooding the market would have been a red flag for card issuers. One quick tipoff about the source of the breach would likely have been the large number of Target Redcard credit and debit card numbers.
5. PCI compliance failed to stop the breach.
Critics of the PCI standard -- created by American Express, Discover Financial Services, JCB International, MasterCard Worldwide, and Visa -- have long suggested that businesses that technically comply with PCI may not have robust information security practices in place. Furthermore, critics have charged that enforcement of the industry-advanced standard lacks teeth, as evidenced by the PCI Council sometimes retroactively revoking certifications.
Critics of the PCI standard -- created by American Express, Discover Financial Services, JCB International, MasterCard Worldwide, and Visa -- have long suggested that businesses that technically comply with PCI may not have robust information security practices in place. Furthermore, critics have charged that enforcement of the industry-advanced standard lacks teeth, as evidenced by the PCI Council sometimes retroactively revoking certifications.
In 1997, for example, TJ Maxx parent company TJX was breached, resulting in the theft of 90 million credit card numbers. In the wake of the breach, investigators revealed that TJX wasn't in compliance with nine of the 12 PCI data security standards. The breach reportedly served as a wakeup call for retailers to get compliant with PCI.
"PCI is designed to push nearly all risks and costs onto merchants and their banks through a series of contracts," said Rich Mogull, CEO of Securosis, in a blog post earlier this year.
But has PCI resulted in major retailers taking information security seriously? Witness the spectacle earlier this year of Visa suing PCI-compliant sports clothing retailer Genesco for $13 million, after the retailer suffered a data breach. The council also retroactively revoked the retailer's PCI compliance. That maneuver, Mogull alleged, allowed the PCI Security Standards Council to continue saying that "no PCI compliant organization has ever been breached."
"This is a clear fallacy -- merchants pass their assessments, they get breached, and then PCI retroactively revokes their certifications," Mogull said. "Fines are then levied against the acquiring bank and passed on to the merchant."
Going forward, Target will reportedly have to hire one of the 10 firms in the United States that are certified to perform PCI investigations. That firm also can't be the same as the company that certified Target's PCI compliance.
6. Consumers: don't panic.
What should consumers who may have been affected by the data breach do next? "React, don't panic," Eva Velasquez, president and CEO of the Identity Theft Resource Center, said via phone. "Because we know that this is causing a lot of anxiety." On the upside, Target said that only card information -- and not people's personal information -- appears to have been stolen by attackers. "So now is the time to monitor statements very carefully," she said. "If you find any other evidence of fraudulent activity, obviously contact your financial institution."
What should consumers who may have been affected by the data breach do next? "React, don't panic," Eva Velasquez, president and CEO of the Identity Theft Resource Center, said via phone. "Because we know that this is causing a lot of anxiety." On the upside, Target said that only card information -- and not people's personal information -- appears to have been stolen by attackers. "So now is the time to monitor statements very carefully," she said. "If you find any other evidence of fraudulent activity, obviously contact your financial institution."
One measure of people's panic is that Target's Redcard website and phone lines have been largely inaccessible since the company confirmed the breach Thursday. "We are working hard to resolve this issue by adding team member support and system capacity as quickly as possible. We apologize for the inconvenience and appreciate our guests' patience," Target spokesman Eric Hausman told the Minneapolis/St. Paul Business JournalFriday morning. In the meantime, the retailer is attempting to triage the outages by fielding customers' questions via Twitter.
7. Visa: we're investigating.
The Identity Theft Resource Center's Velasquez said that anyone who discovers fraud shouldn't have trouble getting help. "This is so big that if fraud is discovered on your card, it's not like your financial institutions are not going to know about this issue," she said.
The Identity Theft Resource Center's Velasquez said that anyone who discovers fraud shouldn't have trouble getting help. "This is so big that if fraud is discovered on your card, it's not like your financial institutions are not going to know about this issue," she said.
Officials at Visa, for example, said Thursday that they're aware of the breach and have already begun working to mitigate any fallout, in part by working to distribute stolen card numbers to all affected issuers. "When such incidents occur, Visa works with the breached entity to provide card issuers with the compromised accounts so they can take steps to protect consumers through fraud monitoring and, if needed, reissuing cards," Visa said in an emailed statement. "Because of advanced fraud-monitoring capabilities, the incidence of fraud involving compromised accounts is actually rare, and Visa fraud rates remain near historic lows."
8. Watch fraud-reporting time limits.
Despite those assurances, anyone who might be a victim of the Target breach should beware card issuers' fraud-reporting windows. Different organizations, for example, may place 30-, 60-, or 90-day limits on when they'll accept a fraud notice, following a cardholder receiving their statement. Others, such as American Express, have no time limit for reporting fraud.
Despite those assurances, anyone who might be a victim of the Target breach should beware card issuers' fraud-reporting windows. Different organizations, for example, may place 30-, 60-, or 90-day limits on when they'll accept a fraud notice, following a cardholder receiving their statement. Others, such as American Express, have no time limit for reporting fraud.
9. Debit card holders: call your bank immediately.
Debit card users should be especially vigilant. Credit card users won't be out of pocket if they suffer fraud and contest the charges, but the opposite is true for debit card holders since fraudulent transactions may take their bank balance to zero.
Debit card users should be especially vigilant. Credit card users won't be out of pocket if they suffer fraud and contest the charges, but the opposite is true for debit card holders since fraudulent transactions may take their bank balance to zero.
Accordingly, Velasquez recommended that any debit card users who might have been Target breach victims immediately contact their card issuers and ask for advice. "Tell them you're a victim of the Target breach," she said. To help combat fraud, different institutions offer different options, such as putting passwords on accounts or changing PIN codes. "But alerting your specific financial institution is really the way to go, because they all have different rules," she said.
10. Kudos to Target for coming clean quickly.
When it comes to information security, Target may have blown it. But according to Velasquez, the retailer does deserve credit for coming clean about the breach so quickly. "Four days? That's lightning speed," she said. "I think they deserve at least a few points for taking the hit and alerting their consumers ahead of time, and not trying to push it off until after the Christmas sales."
When it comes to information security, Target may have blown it. But according to Velasquez, the retailer does deserve credit for coming clean about the breach so quickly. "Four days? That's lightning speed," she said. "I think they deserve at least a few points for taking the hit and alerting their consumers ahead of time, and not trying to push it off until after the Christmas sales."
Compare the speed of Target's notification, for example, to the recent breach at JP Morgan Chase, for which the financial institution didn't issue an alert for more than two months. Or take the breach of the Washington State court system, which was publicly revealed in May 2013 after being detected in February. But state officials don't actually known when the breach occurred, saying they'd narrowed the window only to sometime since September 2012 and before February 2013.
There's no such thing as perfection when it comes to software applications, but organizations should make every effort to ensure that their developers do everything in their power to get as close as possible. This Dark Reading report, Integrating Vulnerability Management Into The Application Development Process, examines the challenges of finding and remediating bugs in applications that are growing in complexity and number, and recommends tools and best practices for weaving vulnerability management into the development process from the very beginning. (Free registration required.)
http://krebsonsecurity.com/2013/12/cards-stolen-in-target-breach-flood-underground-markets/
Cards Stolen in Target Breach Flood Underground Markets
Credit and debit card accounts stolen in a recent data breach at retail giant Target have been flooding underground black markets in recent weeks, selling in batches of one million cards and going for anywhere from $20 to more than $100 per card, KrebsOnSecurity has learned.
Prior to breaking the story of the Target breach on Wednesday, Dec. 18, I spoke with a fraud analyst at a major bank who said his team had independently confirmed that Target had been breached after buying a huge chunk of the bank’s card accounts from a well-known “card shop” — an online store advertised in cybercrime forums as a place where thieves can reliably buy stolen credit and debit cards.
There are literally hundreds of these shady stores selling stolen credit and debit cards from virtually every bank and country. But this store has earned a special reputation for selling quality “dumps,” data stolen from the magnetic stripe on the backs of credit and debit cards. Armed with that information, thieves can effectively clone the cards and use them in stores. If the dumps are from debit cards and the thieves also have access to the PINs for those cards, they can use the cloned cards at ATMs to pull cash out of the victim’s bank account.
At least two sources at major banks said they’d heard from the credit card companies: More than a million of their cards were thought to have been compromised in the Target breach. One of those institutions noticed that one card shop in particular had recently alerted its loyal customers about a huge new batch of more than a million quality dumps that had been added to the online store. Suspecting that the advertised cache of new dumps were actually stolen in the Target breach, fraud investigators with the bank browsed this card shop’s wares and effectively bought back hundreds of the bank’s own cards.
When the bank examined the common point of purchase among all the dumps it had bought from the shady card shop, it found that all of them had been used in Target stores nationwide between Nov. 27 and Dec. 15. Subsequent buys of new cards added to that same shop returned the same result.
On Dec. 19, Target would confirm that crooks had stolen 40 million debit and credit cards from stores nationwide in a breach that extended from Nov. 27 to Dec. 15. Not long after that announcement, I pinged a source at a small community bank in New England to see whether his institution had been notified by Visa or MasterCard about specific cards that were potentially compromised in the Target breach.
This institution has issued a grand total of more than 120,000 debit and credit cards to its customers, but my source told me the tiny bank had not yet heard anything from the card associations about specific cards that might have been compromised as a result of the Target breach. My source was anxious to determine how many of the bank’s cards were most at risk of being used for fraud, and how many should be proactively canceled and re-issued to customers. The bank wasn’t exactly chomping at the bit to re-issue the cards; that process costs around $3 to $5 per card, but more importantly it didn’t want to unnecessarily re-issue cards at a time when many of its customers would be racing around to buy last-minute Christmas gifts and traveling for the holidays.
On the other hand, this bank had identified nearly 6,000 customer cards — almost 5 percent of all cards issued to customers — that had been used at Target stores nationwide during the breach window described by the retailer.
“Nobody has notified us,” my source said. “Law enforcement hasn’t said anything, our statewide banking associations haven’t sent anything out…nothing. Our senior legal counsel today was asking me if we have positive confirmation from the card associations about affected cards, but so far we haven’t gotten anything.”
When I mentioned that a big bank I’d spoken with had found a 100 percent overlap with the Target breach window after purchasing its available cards off a particular black market card shop called rescator[dot]la, my source at the small bank asked would I be willing to advise his fraud team on how to do the same?
CARD SHOPPING
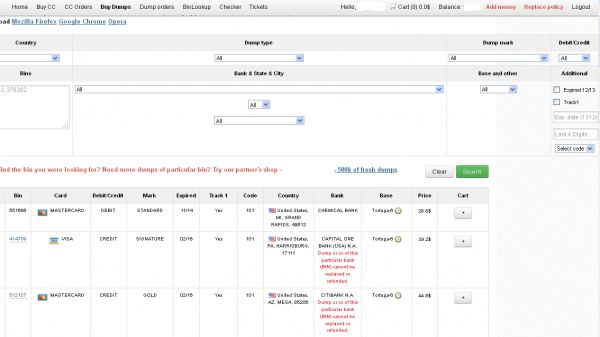
Ultimately, I agreed to help in exchange for permission to write about the bank’s experience without actually naming the institution. The first step in finding any of the bank’s cards for sale was to browse the card shop’s remarkably efficient and customer-friendly Web site and search for the bank’s “BINs”; the Bank Identification Number is merely the first six digits of a debit or credit card, and each bank has its own unique BIN or multiple BINs.

According to the “base” name for all stolen cards sold at this card shop, the proprietor sells only cards stolen in the Target breach.
A quick search on the card shop for the bank’s BINs revealed nearly 100 of its customers’s cards for sale, a mix of MasterCard dumps ranging in price from $26.60 to $44.80 apiece. As one can imagine, this store doesn’t let customers pay for purchases with credit cards; rather, customers can “add money” to their accounts using a variety of irreversible payment mechanisms, including virtual currencies like Bitcoin, Litecoin, WebMoney and PerfectMoney, as well as the more traditional wire transfers via Western Union and MoneyGram.
With my source’s newly registered account funded via wire transfer to the tune of USD $450, it was time to go shopping. My source wasn’t prepared to buy up all of the available cards that match his institution’s BINs, so he opted to start with a batch of 20 or so of the more recently-issued cards for sale.
Like other card shops, this store allows customers to search for available cards using a number of qualifications, including BIN; dozens of card types (MasterCard, Visa, et. al.); expiration date; track type; country; and the name of the financial institution that issued the card.
A key feature of this particular dumps shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle.”
Indeed, shortly after the Target breach began, the proprietor of this card shop — a miscreant nicknamed “Rescator” and a key figure on a Russian-language cybercrime forum known as “Lampeduza” — was advertising a brand new base of one million cards, called Tortuga.
Rescator even created a graphical logo in the Lampeduza forum’s typeface and style, advertising “valid 100% rate,” and offering a money-back guarantee on any cards from this “fresh” base that were found to have been canceled by the card issuer immediately after purchase. In addition, sometime in December, this shop ceased selling cards from other bases aside from those from the Tortuga base. As the month wore on, new Tortuga bases would be added to shop, with each base incrementing by one with almost every passing day (e.g., Tortuga1, Tortuga2, Tortuga3, etc.).
Another fascinating feature of this card shop is that it appears to include the ZIP code and city of the store from which the cards were stolen. One fraud expert I spoke with who asked to remain anonymous said this information is included to help fraudsters purchasing the dumps make same-state purchases, thus avoiding any knee-jerk fraud defenses in which a financial institution might block transactions out-of-state from a known compromised card.
The New England bank decided to purchase 20 of its own cards from this shop, cards from Tortuga bases 6-9, and Tortuga 14 and 15. The store’s “shopping cart” offers the ability to check the validity of each purchased card. Any cards that are checked and found to be invalid automatically get refunded. A check of the cards revealed that just one of the 20 had already been canceled.
The bank quickly ran a fraud and common point-of-purchase analyses on each of the 19 remaining cards. Sure enough, the bank’s database showed that all had been used by customers to make purchases at Target stores around the country between Nov. 29 and Dec. 15.
“Some of these already have confirmed fraud on them, and a few of them were actually just issued recently and have only been used at Target,” my source told me. Incredibly, a number of the cards were flagged for fraud after they were used to make unauthorized purchases at big box retailers, including — wait for it — Target. My source explained that crooks often use stolen dumps to purchase high-priced items such as Xbox consoles and high-dollar amount gift cards, goods that can be fenced, auctioned or otherwise offloaded quickly and easily for cash.
My source said his employer isn’t yet sure which course of action it will take, but that it’s likely the bank will re-issue some or all of the 5,300+ cards affected by the Target breach — most likely sometime after Dec. 25.
The bank is unconcerned that its cards compromised in the Target breach might be used for online shopping fraud because the stolen data does not include the CVV2 — the three digit security code printed on the backs of customer cards. Most online merchants require customers to supply the CVV2 as proof that they posses the legitimate, physical card for the corresponding account that is being used to fund the online purchase.
Update, 5:20 p.m. ET: In a message to consumers, Target CEO Gregg Steinhafel said Target would be offering free credit monitoring for affected customers. Not sure how credit monitoring helps with this specific breach, but at any rate here’s the rest of his statement:“Yesterday we shared that there was unauthorized access to payment card data at our U.S. stores. The issue has been identified and eliminated. We recognize this has been confusing and disruptive during an already busy holiday season. Our guests’ trust is our top priority at Target and we are committed to making this right.We want our guests to understand that just because they shopped at Target during the impacted time frame, it doesn’t mean they are victims of fraud. In fact, in other similar situations, there are typically low levels of actual fraud. Most importantly, we want to reassure guests that they will not be held financially responsible for any credit and debit card fraud. And to provide guests with extra assurance, we will be offering free credit monitoring services. We will be in touch with those impacted by this issue soon on how and where to access the service.We understand it’s been difficult for some guests to reach us via our website and call center. We apologize and want you to understand that we are experiencing unprecedented call volume. Our Target teams are working continuously to build capacity and meet our guests’ needs.We take this crime seriously. It was a crime against Target, our team members, and most importantly, our guests. We’re in this together, and in that spirit, we are extending a 10% discount – the same amount our team members receive – to guests who shop in U.S. stores on Dec. 21 and 22. Again, we recognize this issue has been confusing and disruptive during an already busy holiday season. We want to emphasize that the issue has been addressed and let guests know they can shop with confidence at their local Target stores.”
http://krebsonsecurity.com/2013/12/sources-target-investigating-data-breach/
Sources: Target Investigating Data Breach
Nationwide retail giant Target is investigating a data breach potentially involving millions of customer credit and debit card records, multiple reliable sources tell KrebsOnSecurity. The sources said the breach appears to have begun on or around Black Friday 2013 — by far the busiest shopping day the year.
Update, Dec. 19: 8:20 a.m. ET: Target released a statement this morning confirming a breach, saying that 40 million credit and debit card accounts may have been impacted between Nov. 27 and Dec. 15, 2013.
Original story;
According to sources at two different top 10 credit card issuers, the breach extends to nearly all Target locations nationwide, and involves the theft of data stored on the magnetic stripe of cards used at the stores.
Minneapolis, Minn. based Target Brands Inc. has not responded to multiple requests for comment. Representatives from MasterCard and Visa also could not be immediately reached for comment.
Both sources said the breach was initially thought to have extended from just after Thanksgiving 2013 to Dec. 6. But over the past few days, investigators have unearthed evidence that the breach extended at least an additional week — possibly as far as Dec. 15. According to sources, the breach affected an unknown number of Target customers who shopped at the company’s bricks-and-mortar stores during that timeframe.
“The breach window is definitely expanding,” said one anti-fraud analyst at a top ten U.S. bank card issuer who asked to remain anonymous. “We can’t say for sure that all stores were impacted, but we do see customers all over the U.S. that were victimized.”
There are no indications at this time that the breach affected customers who shopped at Target’s online stores. The type of data stolen — also known as “track data” — allows crooks to create counterfeit cards by encoding the information onto any card with a magnetic stripe. If the thieves also were able to intercept PIN data for debit transactions, they would theoretically be able to reproduce stolen debit cards and use them to withdraw cash from ATMs.
It’s not clear how many cards thieves may have stolen in the breach. But the sources I spoke with from two major card issuers said they have so far been notified by one of the credit card associations regarding more than one million of cards total from both issuers that were thought to have been compromised in the breach. A third source at a data breach investigation firm said it appears that “when all is said and done, this one will put its mark up there with some of the largest retail breaches to date.”
Some of the largest retailer breaches to date may help explain what happened in this case. In 2007, retailer TJX announced that its systems had been breached by hackers. The company later learned that thieves had used the store’s wireless networks to access systems at its Massachusetts headquarters that were used to store data related to payment card, check and return transactions at stores across the country, and that crooks had made off with data from more than 45 million customer credit and debit cards.
In 2009, credit card processor Heartland Payment Systems disclosed that thieves had broken into is internal card processing network, and installed malicious software that allowed them to steal track data on more than 130 million cards.
http://krebsonsecurity.com/2013/12/the-biggest-skimmers-of-all-fake-atms/
The Biggest Skimmers of All: Fake ATMs
This blog has spotlighted some incredibly elaborate and minaturized ATM skimmers, fraud devices that thieves attach to ATMs in a bid to steal card data and PINs. But a skimmer discovered in Brazil last month takes this sort of fraud to another level, using a completely fake ATM designed to be stacked directly on top of a legitimate, existing cash machine.
On Saturday, Nov. 23, a customer at a Bank of Brazil branch in Curitiba, Brazil approached the cash machine pictured below, dipped his ATM card in the machine’s slot, and entered his PIN, hoping to get a printed statement of his bank balance.

A completely fake ATM discovered in Brazil, designed to sit directly on top of the real cash machine.
When the transaction failed, the customer became suspicious and discovered that this ATM wasn’t a cash machine at all, but a complete fake designed to be seated directly on top of the real cash machine. Here’s what the legitimate ATM that was underneath looked like.
When the cops arrived, they pulled the fake ATM off the real cash machine. Here is the fake ATM, set down on the floor.
The backside of the phony cash machine reveals what may be a disassembled laptop with the screen facing outward. The entire apparatus is powered by two large batteries (right). Notice the card skimming device (top right, with the green light) and a side view of the component for the fake PIN pad (top).

The backside of the fake ATM shows what appears to be laptop and skimmer components powered by two huge batteries.
It’s not clear from the reporting in these stories from the Brazilian media (nor from theYoutube video from which the above photos were taken) exactly what hardware was included in this device. It seems difficult to believe that thieves would go to all this trouble without incorporating some type of GSM or 3G components that would allow them to retrieve the stolen information wirelessly. I don’t imagine it would be easy to simply walk away from a cash machine unnoticed while holding a giant fake ATM, and a wireless component would let the skimmer scammers offload any stolen data even after their creations were seized by the authorities.
This device appears to be nearly identical to a fake ATM found in April 2013 in Santa Cruz do Rio Pardo. The story about that April incident has much higher resolution photos, and states that the fake ATM indeed included a 3G mobile connection, ostensibly for sending the stolen card and PIN data to the thieves wirelessly via text message.
Interestingly, much like grammatical and spelling errors often given away phishing emails and Web sites, the thieves who assembled the video for the screen for the fake ATM used in the April robbery appear have made a grammatical goof in spelling “país,” the Portuguese word for “country”; apparently, they left off the acute accent.
Most skimming attacks (including the two mentioned here) take place over the weekend hours. Skimmer scammers like to place their devices at a time when they know the bank will be closed for an extended period, and when foot traffic to the machine will be at its highest.
Keep a keen eye out for anything that looks amiss when you visit the ATM; if you see something that doesn’t look right, notify the bank or owner of the machine, and go somewhere else to get your cash. More importantly, make sure you’re aware of your physical surroundings when you go to withdraw money, and whenever possible use cash machines in well-lit, open places. Most people probably have a better chance of being physically mugged while at the ATM than they do getting scammed by a skimmer. According to a January 2013 report by the U.S. State Department, this is especially true for foreigners in São Paulo, Brazil, where “express kidnappings” occur when criminals force their victims to extract their daily cash limit from an ATM machine.
Finally, although it would not have helped the victims of these fake Brazilian ATMs, using your hand to cover the PIN pad while you enter your digits is a great way to foil most skimmers, which tend to rely on hidden cameras as opposed to fake PIN pads or PIN pad overlays.
Fascinated by ATM skimmers? Check out my series on these fraud devices: All About Skimmers.
http://www.zdnet.com/adobe-warns-of-license-key-email-scam-7000024576/
Adobe warns of license key email scam
Summary: The company has issued a warning that a malicious email campaign is underway using Adobe software licenses as a lure. Adobe calls it a phishing attack, but other reports say it contains a malware attachment.
Adobe is reporting that "...a phishing campaign is underway involving malicious email purporting to deliver license keys for a variety of Adobe offerings."
Based on other reports, such as this one from MX Lab and this one from Cisco Security Intelligence Operations, the emails are not actually a phishing attack, but contain a ZIP file attachment which itself contains a malicious .exe file.
The file names are License_Key_OR4924.zip and License_Key_Document_Adobe_Systems_____.exe.
The email body, as reported by Cisco is thus:
Subject: Download your adobe softwareMessage Body:Hello.Thank you for buying Digital Publishing Suite, Professional Edition Digital Publishing Suite software.Your Adobe License key is in attached document below.Adobe Systems Incorporated.
The MX Lab report shows that there are many variations on the email body. They say the EXE file is 209KB. The VirusTotal report for the malware on Friday night showed 27 of the 49 engines detecting the threat using a variety of threat names.
Guilty Pleas for 13 People Involved in a PayPal DDoS Attack, and a (Strange) Call for Leniency from the Founder of PayPal’s Parent Company
On December 6, thirteen defendants pleaded guilty in U.S. federal court to charges related to their involvement in the cyber-attack of PayPal’s website as part of the group Anonymous. In pleading guilty, the defendants admitted to carrying out a Distributed Denial of Service (DDoS) attack against PayPal in December 2010.
Ten of the defendants each pleaded guilty to one felony count of Conspiracy and one misdemeanor count of Intentional Damage to a Protected Computer. One defendant pleaded guilty to one misdemeanor count of Reckless Damage to a Protected Computer, and the remaining two each pleaded guilty to one misdemeanor count of Intentional Damage to a Protected Computer. Read more
Brazilian "Feliz Natal" - give me your money now!
Dmitry Bestuzhev
Kaspersky Lab Expert
Posted December 21, 01:45 GMT
Tags: Internet Banking, Social Engineering, Campaigns, Malware Creators,Credit Cards
Kaspersky Lab Expert
Posted December 21, 01:45 GMT
Tags: Internet Banking, Social Engineering, Campaigns, Malware Creators,Credit Cards
0
Introduction
Today we got a spam message with a fake e-card in Portuguese leading to an interesting piece of malware:

Malware behind it
The link is a bit.ly short URL and shows that the campaign began today at 1 pm (December 20, 2013) with 628 clicks so far (6:15 pm ET). Most of the people who clicked on it live in Brazil:
 However if you check all statistics of the same Bit.ly user you may find another URLs leading to the same malware but on different domains with a total click number of 619 being USA this time the 2nd country with the most potential victims:
However if you check all statistics of the same Bit.ly user you may find another URLs leading to the same malware but on different domains with a total click number of 619 being USA this time the 2nd country with the most potential victims:
 In both cases the malware is the same and it is:
In both cases the malware is the same and it is:
CartaodeNatal (1).zip 281e25d7a5041bb911d95b937b953d6d
CartaodeNatal.zip 281e25d7a5041bb911d95b937b953d6d
The criminal behind it just prepared 2 different links: one of them is hosted on a purely cybercriminals server and the other one is located on a legitimate hacked Brazilian company web site.
So what does 281e25d7a5041bb911d95b937b953d6d do? It’s a .cpl file detected as Trojan-Downloader.Win32.Banload.cpph and downloading other malicious and non-malicious files from Internet. All files are downloaded from a server located in Brazil:Today we got a spam message with a fake e-card in Portuguese leading to an interesting piece of malware:

(Header translation: You got a Christmas e-card. Somebody very special has sent this Christmas e-card for you. In case you are not able to visualize it, click here. Much better than any present is a happy family).
Malware behind it
The link is a bit.ly short URL and shows that the campaign began today at 1 pm (December 20, 2013) with 628 clicks so far (6:15 pm ET). Most of the people who clicked on it live in Brazil:


CartaodeNatal (1).zip 281e25d7a5041bb911d95b937b953d6d
CartaodeNatal.zip 281e25d7a5041bb911d95b937b953d6d
The criminal behind it just prepared 2 different links: one of them is hosted on a purely cybercriminals server and the other one is located on a legitimate hacked Brazilian company web site.

The files are encrypted and can’t be run if you download them right from the server:
 Once the initial Banloader .cpl is executed it will try to launch Mozilla Firefox from the command line, showing a Java update page (legitimate) even though by double clicking on it we have already given it permission to start its malicious activities. Disguised as a regular application update it will execute several command line processes in the background and it will create copies in the system to make the task of system cleanup much harder.
Once the initial Banloader .cpl is executed it will try to launch Mozilla Firefox from the command line, showing a Java update page (legitimate) even though by double clicking on it we have already given it permission to start its malicious activities. Disguised as a regular application update it will execute several command line processes in the background and it will create copies in the system to make the task of system cleanup much harder.
 We can see from the dependency analysis and network traffic that this file has nothing to do with Java and it´s injecting the malicious code into the memory address of commonly used Windows’ processes.
We can see from the dependency analysis and network traffic that this file has nothing to do with Java and it´s injecting the malicious code into the memory address of commonly used Windows’ processes.
After all the actions have been performed in the victim’s system the user is asked to reboot the environment.

The initial Banloader downloads and executes “The Avenger” anti-rootkit in order to remove some AV products from the recently infected system. This the list of the files to be removed from the system during the reboot:
 The cleanup Avenger batch file is the next one:
The cleanup Avenger batch file is the next one:
 Finally the newly download banker itself is downloaded to the system as rundll32.cpl and executed via CurrentVersion\Run key.
Finally the newly download banker itself is downloaded to the system as rundll32.cpl and executed via CurrentVersion\Run key.
Who’s behind it and other interesting data?
It’s certainly somebody from Brazil. We found traces indicating that this criminal likes to play online games. Also an identical profile the same day posted on bit.ly 7 different URLs. Judging by the time he posted it seems to correspond to a normal work day shift, the activity begins around 9 am and finishes around 2 pm and today is Friday – a working day. That means this is his main “job” – to code, to infect victim’s machine and to steal their money.
Another interesting data is the Santa Claus embedded into the original email is also shortlinked via bit.ly and pointing to a legitimate Brazilian government Web site. The bit.ly statistics shows there are 5707 clicks on it. In reality they are not real clicks but the previsualization made by potential victims via email providers. In other words if the email is configured to show external images in the emails, it will automatically open the original bit.ly url producing a click for the counter. So what’s interesting here? We’ve seen that total number of people who clicked on the mentioned fake e-card is 1247, while the total number of clicks on the Santa’s image is 5707. That means that 21.8% percent of people are very susceptible to the social engineering attacks, still making click while others are more careful and probably won’t click at all.
@dimitribest
@spontiroli


After all the actions have been performed in the victim’s system the user is asked to reboot the environment.

(Translation: Windows update has finished. The system will be rebooted)
The initial Banloader downloads and executes “The Avenger” anti-rootkit in order to remove some AV products from the recently infected system. This the list of the files to be removed from the system during the reboot:


Who’s behind it and other interesting data?
It’s certainly somebody from Brazil. We found traces indicating that this criminal likes to play online games. Also an identical profile the same day posted on bit.ly 7 different URLs. Judging by the time he posted it seems to correspond to a normal work day shift, the activity begins around 9 am and finishes around 2 pm and today is Friday – a working day. That means this is his main “job” – to code, to infect victim’s machine and to steal their money.
Another interesting data is the Santa Claus embedded into the original email is also shortlinked via bit.ly and pointing to a legitimate Brazilian government Web site. The bit.ly statistics shows there are 5707 clicks on it. In reality they are not real clicks but the previsualization made by potential victims via email providers. In other words if the email is configured to show external images in the emails, it will automatically open the original bit.ly url producing a click for the counter. So what’s interesting here? We’ve seen that total number of people who clicked on the mentioned fake e-card is 1247, while the total number of clicks on the Santa’s image is 5707. That means that 21.8% percent of people are very susceptible to the social engineering attacks, still making click while others are more careful and probably won’t click at all.
@dimitribest
@spontiroli








No comments:
Post a Comment