Drones used back to 2006 by the FBI ?
Operating with almost no public notice, the FBIhas spent more than $3 million to operate a fleet of small drone aircraft in domestic investigations, according to a report released Thursday by a federal watchdog agency.
The unmanned surveillance planes have helped FBI agents storm barricaded buildings, track criminal suspects and examine crime scenes since 2006, longer than previously known, according to the 35-page inspector general’s audit of drones used by the Justice Department.
The FBI unmanned planes weigh less than 55 pounds each and are unarmed, the report said. The FBI declined requests to discuss its drone operations Thursday.
In June, Robert S. Mueller III, then director of the FBI, acknowledged the existence of the drone program for the first time during congressional testimony.
Read More...
The unmanned surveillance planes have helped FBI agents storm barricaded buildings, track criminal suspects and examine crime scenes since 2006, longer than previously known, according to the 35-page inspector general’s audit of drones used by the Justice Department.
The FBI unmanned planes weigh less than 55 pounds each and are unarmed, the report said. The FBI declined requests to discuss its drone operations Thursday.
In June, Robert S. Mueller III, then director of the FBI, acknowledged the existence of the drone program for the first time during congressional testimony.
Read More...
Lots of Agencies on the drone mission - Predator used by Customs , how long armed drones are flying over the US at this point ?
Drone Loans: Customs and Border Protection Records 500 Predator Flights for Other Agencies
September 27, 2013
Source: EFF

Customs & Border Protection released a new listto EFF this week that details the extensive number of times that the agency has flown its Predator drones on behalf of other agencies—500 flights in total over a three-year period. This list shows, yet again, how little we know about drone flights in this country and how important it is that we place limits on drone use to protect Americans’ privacy rights.
EFF obtained the list of federal, state and local agencies as a result of our Freedom of Information Act lawsuit against the agency. Not only does the list show the total number of flights by year between 2010 and 2012, but it shows CBP flew its drones over 100 times just for Department of Justice components including FBI, DEA and US Marshals. This is in direct contradiction to a recently released DOJ Office of Inspector General (OIG) Report (pdf) that stated DHS had flown its drones on only two occasions for DOJ law enforcement components.
We discussed some of the other agencies that benefited from CBP’s Predators in a previous post, but some agencies on the list are new. These include the Grand Forks SWAT, the North Dakota Narcotics Task Force, the Bureau of Indian Affairs, the Arizona Department of Public Safety, the Minnesota Drug Task Force, and several branches of the military.
The list also includes several county sheriff’s departments. However, CBP has refused to release the names of these agencies, arguing in a recent court filing that to do so would disclose secret law enforcement techniques and would somehow “reveal that CBP is aware of the illegal activities taking place in a particular location.” It’s hard to fathom how releasing the name of a county sheriff department—without any other information about the drone flight for that department—would somehow let the criminals in the area know they’re being watched and help them evade detection.
Even after all the attention drone surveillance has garnered in the US, CBP has yet to establish rules for its drone flights that would protect Americans’ privacy rights. In the report on the DOJ’s drone use, the Inspector General severely chastised DOJ for similarly failing to implement privacy-protecting rules—and for willfully failing to recognize that drone surveillance raises privacy issues different from surveillance with manned aircraft. The OIG recognized what EFF has been saying all along—that the advanced technological capabilities of drones, their low operational costs as compared to manned aircraft, and their ability to conduct “pervasive tracking of an individual’s movements” whether on “public or private property “ raise “unique concerns about privacy and the collection of evidence.”
We welcome the Inspector General’s investigation of DOJ drone use and hope the same will happen within the Department of Homeland Security—and within CBP in particular. We also encourage the agencies to follow the OIG’s recommendation to convene a working group to address the privacy risks and establish explicit agency-wide rules to protect individual privacy interests.
We discussed some of the other agencies that benefited from CBP’s Predators in a previous post, but some agencies on the list are new. These include the Grand Forks SWAT, the North Dakota Narcotics Task Force, the Bureau of Indian Affairs, the Arizona Department of Public Safety, the Minnesota Drug Task Force, and several branches of the military.
The list also includes several county sheriff’s departments. However, CBP has refused to release the names of these agencies, arguing in a recent court filing that to do so would disclose secret law enforcement techniques and would somehow “reveal that CBP is aware of the illegal activities taking place in a particular location.” It’s hard to fathom how releasing the name of a county sheriff department—without any other information about the drone flight for that department—would somehow let the criminals in the area know they’re being watched and help them evade detection.
Even after all the attention drone surveillance has garnered in the US, CBP has yet to establish rules for its drone flights that would protect Americans’ privacy rights. In the report on the DOJ’s drone use, the Inspector General severely chastised DOJ for similarly failing to implement privacy-protecting rules—and for willfully failing to recognize that drone surveillance raises privacy issues different from surveillance with manned aircraft. The OIG recognized what EFF has been saying all along—that the advanced technological capabilities of drones, their low operational costs as compared to manned aircraft, and their ability to conduct “pervasive tracking of an individual’s movements” whether on “public or private property “ raise “unique concerns about privacy and the collection of evidence.”
We welcome the Inspector General’s investigation of DOJ drone use and hope the same will happen within the Department of Homeland Security—and within CBP in particular. We also encourage the agencies to follow the OIG’s recommendation to convene a working group to address the privacy risks and establish explicit agency-wide rules to protect individual privacy interests.
NSA....Spying on metadat impacts freedom of association as well as violation of privacy right
NSA’s Spying On Metadata Violates Our Freedom of Association
September 28, 2013
Source: Washington's Blog
Why You Should You Care If the Government Spies On Your Metadata
The government has sought to “reassure” us that it is only tracking “metadata” such as the time and place of the calls, and not the actual content of the calls.
But technology experts say that “metadata” can be more revealing than the content of your actual phone calls.
For example, the ACLU notes:
ARS Technica noted last month:
Remember, a U.S. federal judge found that the statute allowing indefinite detention of Americans without due process has a “chilling effect” on free speech. Top reporters have said that they are less likely to interview controversial people, for fear of being accused of “supporting” terrorists.
Given the insanely broad list of actions and beliefs which may get one labeled as a “potential terrorist” by local, state or federal law enforcement, the free association of Americans is being chilled. For example, people may be less willing to call their niece calling to end the Fed, their Occupy-attending aunt, their Tea Party-promoting cousin, their anti-war teacher, or their anti-fracking uncle.
Foreign Policy reported this week that metadata may not catch terrorists, but it’s great at busting journalists and their sources:
Spying on Americans’ metadata destroys our constitutional right to freedom of association … and virtually everything the Founding Fathers fought for.
Indeed, computer experts have used an analogy to explain how powerful metadata is: the English monarchy could have stopped the Founding Fathers in their tracks if they only possessed “metadata” regarding which colonist talked to whom.
But technology experts say that “metadata” can be more revealing than the content of your actual phone calls.
For example, the ACLU notes:
A Massachusetts Institute of Technology study a few years back found that reviewing people’s social networking contacts alone was sufficient to determine their sexual orientation. Consider, metadata from email communications was sufficient to identify the mistress of then-CIA Director David Petraeus and then drive him out of office.
The “who,” “when” and “how frequently” of communications are often more revealing than what is said or written. Calls between a reporter and a government whistleblower, for example, may reveal a relationship that can be incriminating all on its own.
Repeated calls to Alcoholics Anonymous, hotlines for gay teens, abortion clinics or a gambling bookie may tell you all you need to know about a person’s problems. If a politician were revealed to have repeatedly called aphone sex hotline after 2:00 a.m., no one would need to know what was said on the call before drawing conclusions. In addition sophisticated data-mining technologies have compounded the privacy implications by allowing the government to analyze terabytes of metadata and reveal far more details about a person’s life than ever before.The Electronic Frontier Foundation points out:
What [government officials] are trying to say is that disclosure of metadata—the details about phone calls, without the actual voice—isn’t a big deal, not something for Americans to get upset about if the government knows. Let’s take a closer look at what they are saying:New York Magazine explains:
- They know you rang a phone sex service at 2:24 am and spoke for 18 minutes. But they don’t know what you talked about.
- They know you called the suicide prevention hotline from the Golden Gate Bridge. But the topic of the call remains a secret.
- They know you spoke with an HIV testing service, then your doctor, then your health insurance company in the same hour. But they don’t know what was discussed.
- They know you received a call from the local NRA office while it was having a campaign against gun legislation, and then called your senators and congressional representatives immediately after. But the content of those calls remains safe from government intrusion.
Sorry, your phone records—oops, “so-called metadata”—can reveal a lot more about the content of your calls than the government is implying. Metadata provides enough context to know some of the most intimate details of your lives. And the government has given no assurances that this data will never be correlated with other easily obtained data.
- They know you called a gynecologist, spoke for a half hour, and then called the local Planned Parenthood‘s number later that day. But nobody knows what you spoke about.
“When you take all those records of who’s communicating with who, you can build social networks and communities for everyone in the world,” mathematician and NSA whistle-blower William Binney — “one of the best analysts in history,” who left the agency in 2001 amid privacy concerns — told Daily Intelligencer. “And when you marry it up with the content,” which he is convinced the NSA is collecting as well, “you have leverage against everybody in the country.”
“You are unique in the world,” Binney explained, based on the identifying attributes of the machines you use. “If I want to know who’s in the tea party, I can put together the metadata and see who’s communicating with who. I can construct the network of the tea party. If I want to pass that data to the IRS, then I can do that. That’s the danger here.”
At The New Yorker, Jane Mayer quoted mathematician and engineer Susan Landau’s hypothetical: “For example, she said, in the world of business, a pattern of phone calls from key executives can reveal impending corporate takeovers. Personal phone calls can also reveal sensitive medical information: ‘You can see a call to a gynecologist, and then a call to an oncologist, and then a call to close family members.’” [Landau gives a more detailed explanation here.]
“There’s a lot you can infer,” Binney continued. “If you’re calling a physician and he’s a heart specialist, you can infer someone is having heart problems. It’s all in the databases.” The data, he said, is “all compiled by code. The software does it all from the beginning — they have dossiers of everyone in the country. That’s done automatically. When you want to investigate or target somebody, a human becomes involved.”
***
The Guardian reports:“The public doesn’t understand,” Landau told Mayer. “It’s much more intrusive than content.”
The information collected on the AP [in the recent scandal regarding the government spying on reporters] was telephony metadata: precisely what the court order against Verizon shows is being collected by the NSA on millions of Americans every day.
***
Discussing the use of GPS data collected from mobile phones, an appellate court noted that even location information on its own could reveal a person’s secrets: “A person who knows all of another’s travels can deduce whether he is a weekly churchgoer, a heavy drinker, a regular at the gym, an unfaithful husband, an outpatient receiving medical treatment, an associate of particular individuals or political groups,” it read, “and not just one such fact about a person, but all such facts.”
ARS Technica noted last month:
The ACLU filed a declaration by Princeton Computer Science Prof. Edward Felten to support its quest for a preliminary injunction in that lawsuit. Felten, a former technical director of the Federal Trade Commission, has testified to Congress several times on technology issues, and he explained why “metadata” really is a big deal.
***
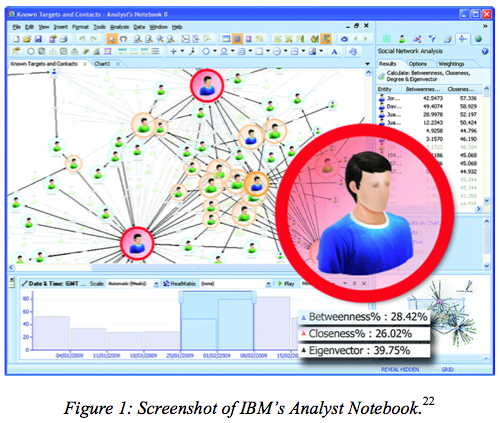
There are already programs that make it easy for law enforcement and intelligence agencies to analyze such data, like IBM’s Analyst’s Notebook. IBM offers courses on how to use Analyst’s Notebook to understand call data better.
Court Documents
Unlike the actual contents of calls and e-mails, the metadata about those calls often can’t be hidden. And it can be incredibly revealing—sometimes moreso than the actual content.
Knowing who you’re calling reveals information that isn’t supposed to be public. Inspectors general at nearly every federal agency, including the NSA, “have hotlines through which misconduct, waste, and fraud can be reported.” Hotlines exist for people who suffer from addictions to alcohol, drugs, or gambling; for victims of rape and domestic violence; and for people considering suicide.
Text messages can measure donations to churches, to Planned Parenthood, or to a particular political candidate.
Felten points out what should be obvious to those arguing “it’s just metadata”—the most important piece of information in these situations is the recipient of the call.Indeed, the government’s spying on our metadata violates our right to freedom of expression, guaranteed by numerous laws and charters including the U.S. Constitution, the European Convention on Human Rights, the Canadian Charter of Rights and Freedoms, and international law, including articles 20 and 23 of the Universal Declaration of Human Rights, and Conventions 87 and 98 of the International Labor Organization.
The metadata gets more powerful as you collect it in bulk. For instance, showing a call to a bookie means a surveillance target probably made a bet. But “analysis of metadata over time could reveal that the target has a gambling problem, particularly if the call records also reveal a number of calls made to payday loan services.”
The data can even reveal the most intimate details about people’s romantic lives. Felten writes:
Consider the following hypothetical example: A young woman calls her gynecologist; then immediately calls her mother; then a man who, during the past few months, she had repeatedly spoken to on the telephone after 11pm; followed by a call to a family planning center that also offers abortions. A likely storyline emerges that would not be as evident by examining the record of a single telephone call.With a five-year database of telephony data, these patterns can be evinced with “even the most basic analytic techniques,” he notes.
By collecting data from the ACLU in particular, the government could identify the “John Does” in the organization’s lawsuits that have John Doe plaintiffs. They could expose litigation strategy by revealing that the ACLU was calling registered sex offenders, or parents of students of color in a particular school district, or people linked to a protest movement.
Remember, a U.S. federal judge found that the statute allowing indefinite detention of Americans without due process has a “chilling effect” on free speech. Top reporters have said that they are less likely to interview controversial people, for fear of being accused of “supporting” terrorists.
Given the insanely broad list of actions and beliefs which may get one labeled as a “potential terrorist” by local, state or federal law enforcement, the free association of Americans is being chilled. For example, people may be less willing to call their niece calling to end the Fed, their Occupy-attending aunt, their Tea Party-promoting cousin, their anti-war teacher, or their anti-fracking uncle.
Foreign Policy reported this week that metadata may not catch terrorists, but it’s great at busting journalists and their sources:
The National Security Agency says that the telephone metadata it collects on every American is essential for finding terrorists. And that’s debatable. [Indeed, top counter-terrorism experts say that all of this spying doesn’t keep us safe , and that it actually hurts U.S. counter-terror efforts (more here and here).] But this we know for sure: Metadata is very useful for tracking journalists and discovering their sources.Top experts have said that mass surveillance sets up the technological framework allowing for “turnkey tyranny”.
On Monday, a former FBI agent and bomb technician pleaded guilty to leaking classified information to the Associated Press about a successful CIA operation in Yemen. As it turns out, phone metadata was the key to finding him.
***
The real reason the government is going after leakers is because it can. Investigators today have greater access to phone records and e-mails than they did before Obama took office, allowing them to follow digital data trails straight to the source.
***
In a highly controversial move, investigators secretly obtained a subpoena for phone records of AP reporters and editors.
***
Once investigators looked at that phone metadata, they got their big break in the case.
***
It’s no wonder that the Obama administration is going after leakers so often. Metadata is the closest thing to a smoking gun that they’re likely to have, absent a wiretap or a copy of an email in which the source is clearly seen giving a reporter classified information.
***
If you’re looking for a case study in the power of metadata, you’ve found it.
Spying on Americans’ metadata destroys our constitutional right to freedom of association … and virtually everything the Founding Fathers fought for.
Indeed, computer experts have used an analogy to explain how powerful metadata is: the English monarchy could have stopped the Founding Fathers in their tracks if they only possessed “metadata” regarding which colonist talked to whom.
And just what is the Navy up to with the mapping of DC by blimp ?
Source: Fox Baltimore
The US Naval Research Laboratory has been conducting aerial mapping operations with a blimp over the areas surrounding Washington DC since Saturday, September 21. The aerial mapping will cease on Oct. 5.
The blimp, a US Navy MZ-3A, has been operating under special approval of the US FAA and the TSA. The aerial mapping will be conducted within the Washington D.C. Flight Restriction Zone (DCA-FRZ) at the U.S. Department of Agriculture, Agricultural Research Service in Beltsville, Md., at U.S. Army Fort Belvoir in Fairfax, Va. and within the DCA-Special Flight Restrictions Area. At times the blimp will travel the region to the north to Frederick Municipal Airport in Maryland and to the southwest near Culpepper, Va.
The MZ-3A is government-owned and operated by contractor Integrated Systems Solutions, Inc.
The 178-foot MZ-3A blimp can travel at a top speed just under 50 knots and can remain aloft and nearly stationary for more than twelve hours.
And " Justice " For All ?
The US Naval Research Laboratory has been conducting aerial mapping operations with a blimp over the areas surrounding Washington DC since Saturday, September 21. The aerial mapping will cease on Oct. 5.
The blimp, a US Navy MZ-3A, has been operating under special approval of the US FAA and the TSA. The aerial mapping will be conducted within the Washington D.C. Flight Restriction Zone (DCA-FRZ) at the U.S. Department of Agriculture, Agricultural Research Service in Beltsville, Md., at U.S. Army Fort Belvoir in Fairfax, Va. and within the DCA-Special Flight Restrictions Area. At times the blimp will travel the region to the north to Frederick Municipal Airport in Maryland and to the southwest near Culpepper, Va.
The MZ-3A is government-owned and operated by contractor Integrated Systems Solutions, Inc.
The 178-foot MZ-3A blimp can travel at a top speed just under 50 knots and can remain aloft and nearly stationary for more than twelve hours.
And " Justice " For All ?
So Why is Dimon Getting to Plead His Case for JP Morgan (and Maybe Himself) Personally?
September 27, 2013
Source: Naked Capitalism
I got this e-mail from a law school professor this evening:
In case you wondered what the indignation was about, here’s a Washington Post recap:
But the more disturbing bit is the Administration’s high odds of jumping on what I suspect is a JP Morgan PR line, that touting this settlement as “the largest evah” will give Holder & Co. some sort of newfound credibility. Even the WaPo isn’t buying it:
In addition, JP Morgan has managed to promulgate the myth it was less deeply involved in the mortgage business because it perceived the risks and stayed away. Not true. For instance, it was rumored in February 2007 that Dimon wassniffing around Bear as a possible acquisition. Several correspondents wrote today of how eager JP Morgan was to increase its participation in the CDO business (mind you, I’ve heard this repeatedly over the years from insiders). From one message:
Thus it’s nuts for the DoJ to enter into any settlement that includes JP Morgan executives as individuals until it sees how the pending cases play out. And recall that we’ve already said even before the $920 million settlement that Dimon was a clear-cut case for a criminal Sarbanes Oxley prosecution. The information in the SEC’s order only strengthens our view (mind you, that does not mean we think in a nanosecond that Dimon will be charged criminally. But that threat could be used to force long-overdue corporate governance changes and if more damaging evidence were to surface, a timetable for Dimon’s departure).
But the flip side is that the negotiations supposedly included the question of whether the bank would be charged criminally. That sort of move has not been all that well received, since past criminal settlements have involved only subsidiaries (having a parent or critically important sub admit to criminal conduct would bar quite a few customers from doing business with it, and that’s widely viewed as a nuclear option and thus unusable in practice). And JP Morgan may be playing “don’t throw us in the briar patch,” acting as if it is extremely loath to admit to criminal charges at a subsidiary level when it hopes that that sort of sanction will buy the Administration enough PR points so as to make it less eager to pursue individuals to the maximum extent.
Holder indirectly acknowledged that issue. The Washington Post again:
So the good news is Jamie is actually breaking a sweat. The bad news is the Administration has signaled how accommodating it is likely to be through the unseemly act of giving him an audience.
wtf is with Eric Holder personally meeting with Jaimie Dimon? Since when do other targets of investigations get such access and solicitude? Do you think any AG would have met with Michael Milken when he was being investigated? Unreal.It should be no surprise by now to see the degree to which Administration officials toady and scrape to the banks. Oh yes, you’ll witness the occasional stern word in public from Obama and his minions to maintain the appearance that that they operate independently of their financial lords and masters. But Holder has been so absent from any meaningful action that it’s surprising to see him pretend to play a hands-on role. I’d was certain he had forgotten how to practice law, since his main job seemed to be acting as propagandist for Team Obama enforcement theater.
In case you wondered what the indignation was about, here’s a Washington Post recap:
The sage of Wall Street journeyed to Washington on Thursday, but Jamie Dimon’s visit was unlike any the JPMorgan Chase chief has made before.“Sage of Wall Street”? Ready the barf bag. The most lofty title Dimon has been given before it “titan” which is acceptable, if cloying, given JP Morgan’s size. But “sage of Wall Street” has heretofore been limited to Warren Buffett, who has not only his investment record but his cagey corn pone to legitimate that label. “Sage” connotes wisdom above all, and Dimon’s conduct during and after the Whale affair was anything but.
Dimon sought a meeting with Attorney General Eric H. Holder Jr. in an urgent bid to dispose of multiple government investigations into the bank’s conduct leading up to the financial crisis — and avoid criminal charges. The deal that Dimon discussed with Holder would involve paying the government at least $11 billion, the biggest settlement a single company has ever undertaken, according to several people familiar with the negotiations…
For Holder, 62, meanwhile, a landmark settlement with JPMorgan could help quiet criticism that the Justice Department has failed to hold Wall Street accountable for sparking the housing market’s crash and the ensuing recession. Holder was criticized by lawmakers and consumer advocates this year for saying that some banks had become too big to prosecute.
But the more disturbing bit is the Administration’s high odds of jumping on what I suspect is a JP Morgan PR line, that touting this settlement as “the largest evah” will give Holder & Co. some sort of newfound credibility. Even the WaPo isn’t buying it:
Even at $11 billion or more, the bank would be paying just a fraction of the damage it wreaked on mortgage investors, government agencies and homeowners. And a deal might ensure that no senior executives go to jail, which some experts say would let Wall Street avoid full responsibility.Comparing the past settlements to the pending JP Morgan deal is like comparing apples to stinky fruit. The next biggest one was for a single abuse, that of GlaxoSmithKline for selling antidepressants illegally. This settlement, by contrast, even though it involves only one product, covers a swathe of bad conduct across three institutions: Bear, WaMu, and JP Morgan. And it also includes the monster Fannie and Freddie putback liability. All the banks that had large subprime businesses are going to stump up large payments to put those claims to bed. By going out early and wrapping other outstanding litigation into the mix, the Morgan bank makes the settlement look more serious than it really is.
In addition, JP Morgan has managed to promulgate the myth it was less deeply involved in the mortgage business because it perceived the risks and stayed away. Not true. For instance, it was rumored in February 2007 that Dimon wassniffing around Bear as a possible acquisition. Several correspondents wrote today of how eager JP Morgan was to increase its participation in the CDO business (mind you, I’ve heard this repeatedly over the years from insiders). From one message:
I had JPM CDO salesmen banging down my door in 2006 and early 2007. They wanted to do more, but didn’t have the staff, assets etc. They didn’t miss out on CDO carnage because of good risk management. They just weren’t that good at it.So let’s understand what Dimon’s confab with Holder was likely about (the JP Morgan chief also brought his general counsel and bank regulatory uberlawyer Rodg Cohen). The subtext of the article was that Dimon was pressing for a deal to be done quickly. Why the urgency? Well, one has to wonder how much Dimon is effectively appearing in a personal versus an executive capacity. It would be, um, inappropriate to conflate the two discussions, but it’s not hard to imagine that Dimon thought a personal meeting with Holder, showing what an impressive figure he is, could only work in his favor (it isn’t only Dimon who is impressed with his own impressiveness; journalists like Andrew Ross Sorkin and Gillian Tett, who uncharacteristically looks to have been swayed by being embedded at JP Morgan, have also fawned over him). Remember, the CFTC has not settled its Whale charges, and it might unearth some further violations or facts that make JP Morgan top brass look even worse. The DoJ (through its Southern District of New York office) has charged two JP Morgan traders. It isn’t clear whether it will succeed in getting either one extradited, but if it did, you can be sure they prosecutors would be seeing if they could get them to cop a plea bargain to implicate more senior management.
Thus it’s nuts for the DoJ to enter into any settlement that includes JP Morgan executives as individuals until it sees how the pending cases play out. And recall that we’ve already said even before the $920 million settlement that Dimon was a clear-cut case for a criminal Sarbanes Oxley prosecution. The information in the SEC’s order only strengthens our view (mind you, that does not mean we think in a nanosecond that Dimon will be charged criminally. But that threat could be used to force long-overdue corporate governance changes and if more damaging evidence were to surface, a timetable for Dimon’s departure).
But the flip side is that the negotiations supposedly included the question of whether the bank would be charged criminally. That sort of move has not been all that well received, since past criminal settlements have involved only subsidiaries (having a parent or critically important sub admit to criminal conduct would bar quite a few customers from doing business with it, and that’s widely viewed as a nuclear option and thus unusable in practice). And JP Morgan may be playing “don’t throw us in the briar patch,” acting as if it is extremely loath to admit to criminal charges at a subsidiary level when it hopes that that sort of sanction will buy the Administration enough PR points so as to make it less eager to pursue individuals to the maximum extent.
Holder indirectly acknowledged that issue. The Washington Post again:
The discussion centered partly on whether the bank could avoid criminal prosecution if it paid the fine and whether it would have to admit guilt. Asked about the negotiations in an unrelated news conference, Holder acknowledged the meeting but snapped at a reporter who suggested that “prison time” was not part of the talks. “You weren’t in the room when I said I was talking to them,” Holder said.Mind you, the Financial Times makes the meeting sound more like normal commercial haggling. If so, why did Dimon press to make a personal appearance? From the pink paper:
Mr Dimon’s trip to Washington followed Mr Holder personally rejecting a previous offer to resolve the matters as being too low. Talks were rekindled after the US threatened on Tuesday to sue the bank…Yves again. The only reason one might normally use to legitimate a meeting like this, is if talks between the two sides has become so acrimonious that the principals needed to meet. But that makes no sense with Dimon represented by the best lawyers money can buy, who happen also to be much cooler headed than he is, both in general and by virtue of not having to negotiate for themselves.
JPMorgan is arguing over the extent to which it should be responsible for the actions of Bear Stearns and Washington Mutual, both institutions that the bank bought during the crisis with the encouragement of the government.
The bank has said in disclosures to investors that it “believes it has no remaining exposure related to loans” sold to Fannie and Freddie. Mr Dimon has suggested it is not fair to punish the bank for past allegations of the two companies.
So the good news is Jamie is actually breaking a sweat. The bad news is the Administration has signaled how accommodating it is likely to be through the unseemly act of giving him an audience.
No comments:
Post a Comment